Chapter: Embedded Systems
Embedded Programming Concepts
EMBEDDED
PROGRAMMING CONCEPTS
Programming in Assembly and HLL
• Processor
and memory-sensitive instructions: Program codes maybe written in assembly
• Most of
codes: Written in a high level language (HLL), 'C‘, 'C++‘or Java
Assembly Language Programming
Advantage
Assembly codes sensitive to the processor, memory, ports and devices hardware Gives a precise control of the processor internal devices
Enables full use of processor specific features in its instruction set and its addressing modes Machine codes are compact, processor and memory sensitive
System needs a smaller memory.
Memory needed does not depend on the programmer data type selection and rule declarations
Not the compiler specific and library functions specific
Device driver codes may need only a few assembly instructions. Bottom-up-design approach
Advantage of using high level language (HLL) for
Programming
Short Development Cycle
• Code
reusability─ A function or routine can be repeatedly used in a program
• Standard
library functions─ For examples, the mathematical functions and delay ( ), wait
( ), sleep ( ) functions
• Use of
the modular building blocks
• Sub-modules
are designed first for specific and distinct set of actions, then the modules
and finally integration into complete design.
• First
code the basic functional modules and then build a bigger module and then
integrate into the final system
• First
design of main program (blueprint),then its modules and finallythe sub-modules
are designed for specific and distinct set of actions.
• Top-down
design Most favoured program design approach
Use of Data Type and Declarations
• Examples,
char, int, unsigned short, long, float,
double, Boolean.
• Each data
type provides an abstraction of the (i) methods to use, manipulate and
represent, and (ii) set of permissible operations.
Use of Type Checking
• Type
checking during compilation makes the program less prone to errors.
• Example─
type checking on a char data type variable (a character) does not permit
subtraction, multiplication and division.
Use of Control Structures, loops and Conditions
• Control
Structures and loops
• Examples─
while, do-while, break and for
• Conditional
Statements examples
if, if- else, else - if and switch - case)
• Makes
tasks simple for the program flow Design
Use of Data Structures _ Data structure
- A way
of organizing large amounts of data.
_ A data
elements‘ collection
_ Data
element in a structure identified and accessed with the help of a few pointers
and/or indices and/or functions.
Standard Data structure
• Queue
• Stack
• Array –
one dimensional as a vector
• Multidimensional
• List
• Tree
Use of Objects
_ Objects
bind the data fields and methods to manipulate those fields
_ Objects
reusability
_ Provide
inheritance, method overloading, overriding and interfacing
_ Many
other features for ease in programming
Advantage of using C for Programming
C
•Procedure
oriented language (No objects)
• Provision
of inserting the assembly language codes in between (called inline assembly) to
obtain a direct hardware control.
• A large
program in ‗C‘ splits into the declarations for variables, functions and data
structure, simpler functional blocks and statements.
In-line assembly codes of C functions
• Processor
and memory sensitive part of the program within the inline assembly, and the
complex part in the HLL codes.
• Example
function ouportb (q, p)
• Example─ Mov al, p; out q, al
C Program Elements
Preprocessor include Directive
_ Header,
configuration and other available source files are made the part of an embedded
system program source file by this directive
Examples of Preprocessor include Directives
# include
"VxWorks.h" /* Include VxWorks
functions*/
# include
"semLib.h" /* Include Semaphore
functions Library */
# include
"taskLib.h" /* Include multitasking
functions Library */
# include
"sysLib.c" /* Include
system library for system functions */
# include
"netDrvConfig.txt" /*
Include a text file that provides the 'Network Driver Configuration'. */
include
"prctlHandlers.c" /*
Include file for the codes for handling and actions as per the protocols used
for driving streams to the network. */
Preprocessor Directive for the Definitions
• Global
Variables ─ # define volatile Boolean IntrEnable
Constants
─ # define false 0
•
Strings─ # define welcomemsg"Welcome
To ABC Telecom"
Preprocessor Macros
• Macro - A
named collection of codes that is defined in a program as preprocessor
directive.
• Differs
from a function in the sense that once a macro is defined by a name, the
compiler puts the corresponding codes at the macro at every place where that
macro-name appears.re used for short codes only.
Difference between Macro and Function
• The codes
for a function compiled once only
• On
calling that function, the processor has to save the context, and on return
restore the context.
• Macros
are used for short codes only.
• When a
function call is used instead of macro, the overheads (context saving and
return) will take a time, T overheads that is the same order of magnitude as the
time, Texec for execution of short codes within a function.
• Use the function
when the Toverheads<<Texec and macro when Toverheads ~= or >
Texec.
Use of Modifiers
·
auto
·
unsigned
·
static
·
const
·
register
·
interrupt
·
extern
·
volatile
·
volatile static
Use of infinite loops
_
Infinite loops- Never desired inusual programming. Why? The program will never
end and never exit or proceed further to the codes after the loop.
_
Infinite loop is a feature in embedded system programming! Example:
A
telephone is never switching off.
The
system software in the telephone has to be always in awaiting loop that finds
the ring onthe line. An exit from the loop will make the system hardware redundant.
# define false 0
# define true 1
# void main (void) {
/* Call RTOS run here */
rtos.run ( );
/* Infinite while loops follows in each task. So
never there is return from the RTOS. */
}
void task1 (....) {
/* Declarations */.
while (true) {
/* Run Codes that repeatedly execute */ /* Run
Codes that execute on an event*/
if (flag1)
{....;}; flag1 =0;
/* Codes that execute for message to the kernel */
message1 ( ); } }
Use of
typedef
_
Example─ A compiler version may not process the declaration as an unsigned byte
_ The 'unsigned character' can then be used as a data type.
_
Declared as follows: typedef unsigned character port A data _ Used as follows:
#define PbyteportAdata0xF1
Use of Pointers
Pointers
are powerful tools when used correctly and according to certain basic
principles.
# define
COM ((structsio near*) 0x2F8);
This
statement with a single masterstroke assigns the addresses to all 8variables
Byte at the sio Addresses
0x2F8:
Byte at RBR/THR /DLATCH-LByte
0x2F9:
Byte at DLATCH-HByte
0x2FA:
Byte at IER;
0x2FB:
Byte at LCR;
0x2FC:
Byte at MCR;
0x2FD:
Byte at LSR;
0x2FE:
Byte at MSR
0x2FF:
Byte Dummy Character
Example
Free the
memory spaces allotted to a datastructure.
#define NULL (void*) 0x0000
• Now
statement & COM ((structsionear*) =
NULL;assigns the COM to Null and make freethe memory between 0x2F8 and
0x2FFfor other uses.
Data
structure
• Example─
structure sio
• Eight
characters─ Seven for thebytes in BR/THR/DLATCHLByte,IER, IIR, LCR, MCR, LSR,
MSR registers of serial line device and one dummy variablere consisting of 8 character variables structure for the COM port 2 in the UART serial line device at an
IBMPC.
Example of Data structure declaration
• Assume structured variable COM at the addresses
beginning 0x2F8.
# define
COM ((structsio near*) 0x2F8)
• COM is at 8 addresses 0x2F8-0x2FF and is a
structure consisting of 8 character variables structure for the COM port 2
inthe UART serial line device at an IBMPC.
# define
COM1 ((structsio near*) 0x3F8);
It will give another structured variableCOM1 at
addresses beginning 0x3F8using the data structure declared earlier as sio
Use of functions
(i)
Passing the Values (elements):
The
values are copied into the arguments of the functions. When the function is
executed in this way, it does not change a variable's value at the function,
which calls new function.
(ii)
Passing the References
When an
argument value to a function passes through a pointer, the called function can
change this value. On returning from this function, the new value may be available
in the calling program or another function called by this function.
Use of Reentrant Function
• Reentrant
function- A function usable by the several tasks and routines synchronously (at
the same time). This is because all the values of its argument are retrievable
from the stack.
Three conditions for a function called as reentrant function
1. All
the arguments pass the value sand none of the argument is a pointer (address)
whenever a calling function calls that function.
2. When
an operation is not atomic, that function should not operate on any variable,
which is declared outside the function or which an interrupt servicer outine
uses or which is a global variable but passed by reference and not passed by
value as an argumentnto the function. [The value of such a variable or
variables, which is not local, does not save on the stack when there is call to
another program.]
3. That
function does not call any other function that is not itself Reentrant.
Data Structures: Arrays
• Array:
A structure with a series of data items sequentially placed in memory
(i) Each
element accessible by anidentifier name (which points tothe array) and an
index, i (which define offset from
the first element)
(ii)
istarts
from 0 and is +ve integer
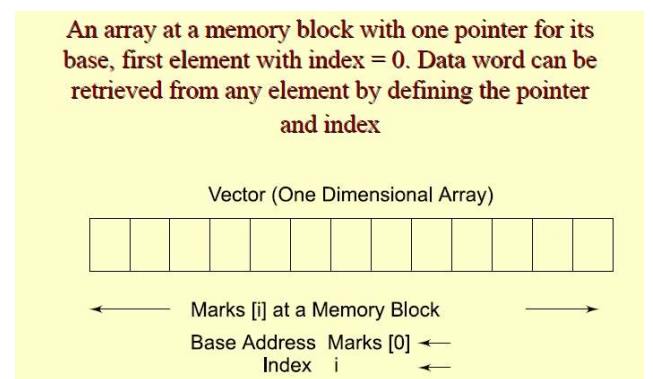
One
dimensional array (vector)
Example
1:
Unsigned int
salary [11];
salary[0] –
1st month salary. salary[11] –
12th month salary Each integer is
of 32-bit (4 bytes);
salary assigned 48 bytes addressspace
Example
2: sioCOM [1];
COM [0]– COM1 port data record with structure equivalent to sio
COM [1]– COM2 port data record with structure equivalent to sio
COM assigned 2*8 characters = 16
bytes address space
Two
dimensional array
Example
3:
Unsigned int
salary [11, 9];
salary[3, 5]– 4th month 6th year salary
salary[11, 4] – 12th month 5th year
salary salary assigned 12*10*4 = 480 bytes address
space
Multi-dimensional
array
Example
4:
char pixel [143,175, 23];
pixel [0, 2, 5] – 1st horizontal line
index x,3rd vertical line index y, 6th color c.pixel assigned 144*176*24
= 608256bytes address space in a colored picture of resolution 144x 176 and
24colors.
Programming using functions and function queues
_ Use of
multiple function calls in the main ( )
_ Use of
multiple function calls in cyclic order
_ Use of
pointer to a function
_ Use of
function queues and
_ Use of
the queues of the function pointers built by the ISRs.
It
reduces significantly the ISR latency periods. Each device ISR is therefore
able to execute within its stipulated deadline
1.Multiple function calls
2. Multiple function calls in cyclic order Use
• One of
the most common methods is the use of multiple function-calls in a cyclic order
in an infinite loop of the main ( ).
3. Use of function pointers
* sign
when placed before the function name then it refers to all the compiled form of
the statements in the memory that are specified within the curly braces when
declaring the function.
• A
returning data type specification (for example, void) followed by'(*function Name) (function Arguments)'calls the statements of the function Name using the function Arguments, and on a return, itreturns the specified data
object. We can thus use the function pointer for invoking a call to the
function.
4. Queue of Function-pointers
Application
_ Makes
possible the designing of ISRs with short codes and by running the functions of
the ISRsat later stageso all pending ISRsfinishes
Multiple ISRs insertion of Function pointers into a
Queue
• The ISRs
insert the function pointers
• The
pointed functions in the queue execute at later stages by deleting from the
queue
• These
queued functions execute after the service to all pending ISRs finishes
Priority Function Queue of Multiple ISRs
• When
there are multiple ISRs, a high priority interrupt service routine is executed
first and the lowest priority.
• The ISRs
insert the function pointers into a priority queue of function pointers[ISR can
now be designed short enough sothat other source don‘t miss a deadline
forservice]
Related Topics