Chapter: Security in Computing : Security in Networks
Types of IDSs(Intrusion Detection Systems)
Types of IDSs
The two general types of
intrusion detection systems are signature based and heuristic. Signature-based intrusion detection
systems perform simple pattern-matching and report situations that match a
pattern corresponding to a known attack type. Heuristic intrusion detection
systems, also known as anomaly based, build a model of acceptable behavior and
flag exceptions to that model; for the future, the administrator can mark a
flagged behavior as acceptable so that the heuristic IDS will now treat that
previously unclassified behavior as acceptable.
Intrusion detection devices
can be network based or host based. A etwork -based IDS is a stand-alone device
attached to the network monitor traffic throughout that network; a host-based
IDS runs on to a single workstation or client or host, to protect that one
host.
Early intrusion detection
systems (for example, [DEN87b, LUN90a, FOX90
, LIE89]) worked after the fact, by
reviewing logs of system activity to spot potential misuses that had occurred.
The administrator could review the results of the IDS to find and fix
weaknesses in the system. Now, however, intrusion detection systems operate in
real time (or near real time), watching activity and raising alarms in time for
the administrator to take protective action.
Signature-Based Intrusion Detection
A simple signature for a
known attack type might describe a series of TCP SYN packets sent to many different
ports in succession and at times close to one another, as would be the case for
a port scan. An intrusion detection system would probably find nothing unusual
in the first SYN, say, to port 80, and then another (from the same source
address) to port 25. But as more and more ports receive SYN packets, especially
ports that are not open, this pattern reflects a possible port scan. Similarly,
some implementations of the protocol stack fail if they receive an ICMP packet
with a data length of 65535 bytes, so such a packet would be a pattern for
which to watch.
The problem with
signature-based detection is the signatures themselves. An attacker will try to
modify a basic attack in such a way that it will not match the known signature
of that attack. For example, the attacker may convert lowercase to uppercase
letters or convert a symbol such as "blank space" to its character
code equivalent %20. The IDS must necessarily work from a canonical form of the
data stream in order to recognize that %20 matches a pattern with a blank
space. The attacker may insert malformed packets that the IDS will see, to
intentionally cause a pattern mismatch; the protocol handler stack will discard
the packets because of the malformation. Each of these variations could be detected
by an IDS, but more signatures require additional work for the IDS, which
reduces performance.
Of course, signature-based
IDSs cannot detect a new attack for which a signature is not yet installed in
the database. Every attack type starts as a new pattern at some time, and the
IDS is helpless to warn of its existence.
Signature-based intrusion
detection systems tend to use statistical
analysis. This approach uses statistical tools both to obtain sample
measurements of key indicators (such as amount of external activity, number of
active processes, number of transactions) and to determine whether the
collected measurements fit the predetermined attack signatures.
Ideally, signatures should
match every instance of an attack, match subtle variations of the attack, but
not match traffic that is not part of an attack. However, this goal is grand
but unreachable.
Heuristic Intrusion Detection
Because signatures are
limited to specific, known attack patterns, another form of intrusion detection
becomes useful. Instead of looking for matches, heuristic intrusion detection
looks for behavior that is out of the ordinary. The original work in this area
(for example, [TEN90]) focused on the
individual, trying to find characteristics of that person that might be helpful
in understanding normal and abnormal behavior. For example, one user might
always start the day by reading e-mail, write many documents using a word
processor, and occasionally back up files. These actions would be normal. This
user does not seem to use many administrator utilities. If that person tried to
access sensitive system management utilities, this new behavior might be a clue
that someone else was acting under the user's identity.
If we think of a compromised
system in use, it starts clean, with no intrusion, and it ends dirty, fully
compromised. There may be no point in the trace of use in which the system
changed from clean to dirty; it was more likely that little dirty events
occurred, occasionally at first and then increasing as the system became more
deeply compromised. Any one of those events might be acceptable by itself, but
the accumulation of them and the order and speed at which they occurred could
have been signals that something unacceptable was happening. The inference
engine of an intrusion detection system performs continuous analysis of the
system, raising an alert when the system's dirtiness exceeds a threshold.
Inference engines work in two
ways. Some, called state-based intrusion detection systems, see the system
going through changes of overall state or configuration. They try to detect
when the system has veered into unsafe modes. Others try to map current
activity onto a model of unacceptable activity and raise an alarm when the
activity resembles the model. These are called model-based intrusion detection
systems. This approach has been extended to networks in [MUK94]. Later work (for example, [ FOR96, LIN99])
sought to build a dynamic model of behavior, to accommodate variation and
evolution in a person's actions over time. The technique compares real activity
with a known representation of normality.
Alternatively, intrusion
detection can work from a model of known bad activity. For example, except for
a few utilities (login, change password, create user), any other attempt to
access a password file is suspect. This form of intrusion detection is known as
misuse intrusion detection. In this work, the real activity is compared
against a known suspicious area.
All heuristic intrusion
detection activity is classified in one of three categories: good/benign,
suspicious, or unknown. Over time, specific kinds of actions can move from one
of these categories to another, corresponding to the IDS's learning whether
certain actions are acceptable or not.
As with pattern-matching,
heuristic intrusion detection is limited by the amount of information the
system has seen (to classify actions into the right category) and how well the
current actions fit into one of these categories.
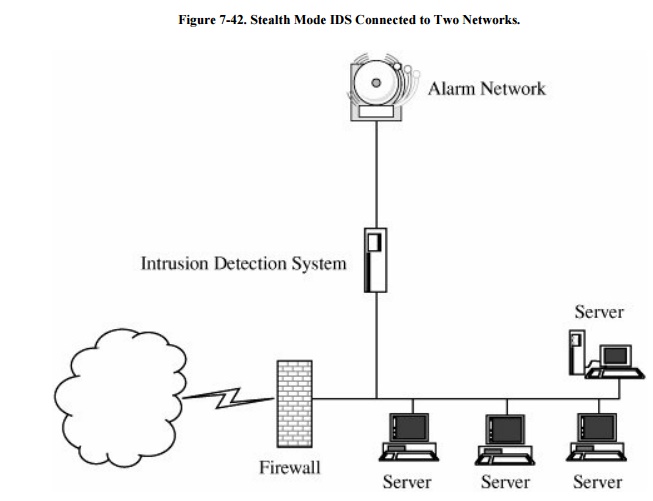
Stealth Mode
An IDS is a network device
(or, in the case of a host-based IDS, a program running on a network device).
Any network device is potentially vulnerable to network attacks. How useful
would an IDS be if it itself were deluged with a denial-of-service attack? If
an attacker succeeded in logging in to a system within the protected network,
wouldn't trying to disable the IDS be the next step?
To counter those problems,
most IDSs run in stealth mode,
whereby an IDS has two network interfaces: one for the network (or network
segment) being monitored and the other to generate alerts and perhaps other
administrative needs. The IDS uses the monitored interface as input only; it
never sends packets out through that interface. Often, the interface is
configured so that the device has no published address through the monitored
interface; that is, a router cannot route anything to that address directly,
because the router does not know such a device exists. It is the perfect
passive wiretap. If the IDS needs to generate an alert, it uses only the alarm
interface on a completely separate control network. Such an architecture is
shown in Figure 7-42.
Other IDS Types
Some security engineers
consider other devices to be IDSs as well. For instance, to detect unacceptable
code modification, programs can compare the active version of a software code
with a saved version of a digest of that code. The tripwire program [KIM98] is the most well known software (or
static data) comparison program. You run tripwire on a new system, and it
generates a hash value for each file; then you save these hash values in a
secure place (offline, so that no intruder can modify them while modifying a
system file). If you later suspect your system may have been compromised, you
rerun tripwire, providing it the saved hash values. It recomputes the hash
values and reports any mismatches, which would indicate files that were
changed.
System vulnerability
scanners, such as ISS Scanner or Nessus, can be run against a network. They
check for known vulnerabilities and report flaws found.
As we have seen, a honeypot
is a faux environment intended to lure an attacker. It can be considered an
IDS, in the sense that the honeypot may record an intruder's actions and even
attempt to trace who the attacker is from actions, packet data, or connections.
Related Topics