Chapter: Security in Computing : Security in Networks
Types of Networks
Types of Networks
A network is a collection of
communicating hosts. But to understand the network and how it works, we have
several key questions to ask, such as How many hosts? Communicating by what
means? To answer these questions, we are helped by an understanding of several
types of subclasses of networks, since they commonly combine into larger
networks. The subclasses are general notions, not definitive distinctions. But
since the terms are commonly used, we present several common network subclasses
that have significant security properties.
Local Area Networks
As the name implies, a local area network (or LAN)
covers a small distance, typically within a single building. Usually a LAN
connects several small computers, such as personal computers, as well as
printers and perhaps some dedicated file storage devices. Figure 7-10 shows the arrangement of a typical
LAN. The primary advantage of a LAN is the opportunity for its users to share
data and programs and to share access to devices such as printers.
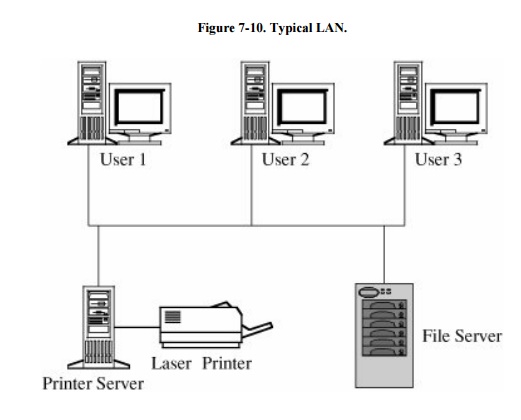
Most LANs have the following
characteristics.
·
Small. Typically, fewer than 100 users share a single LAN, within a
distance less than 3 kilometers, or 2 miles. More commonly, a LAN is much
smaller, stretching less than 1 kilometer inside a single building.
·
Locally controlled. The equipment is owned and managed by a single
organization. The users all are affiliated with a single organization, such as
a company, a department, a workgroup, or a physical proximity.
·
Physically protected. The LAN is on the premises of a company or
other organization, so malicious outsiders usually cannot readily get to the
LAN equipment.
Limited scope. Many LANs support a single
group, department, floor, activity, or other geographical or administrative
unit. As a result, each has a narrowly scoped set of functions it performs.
Wide Area Networks
A wide area network, or WAN, differs from a local area network in
terms of both size or distance (as its name implies, it covers a wider
geographic area than does a LAN) and control or ownership (it is more likely
not to be owned or controlled by a single body). Still, there tends to be some
unifying principle to a WAN. The hosts on a WAN may all belong to a company
with many offices, perhaps even in different cities or countries, or they may
be a cluster of independent organizations within a few miles of each other, who
share the cost of networking hardware. These examples also show how WANs
themselves differ. Some are under close control and maintain a high degree of
logical and physical isolation (typically, these are WANs controlled by one
organization), while others are only marriages of convenience. Typical
characteristics of WANs are these.
·
Single control. Typically, a single organization is responsible for
and controls a wide area network. Even if a network is shared by several
unrelated subscribers, one organization usually determines who may join the
network.
·
Covers a significant distance. A WAN generally serves a distance greater
than a LAN can cover, typically from a few miles to the entire globe.
·
Physically exposed (often, but not always). Most wide area networks
use publicly available communications media, which are relatively exposed.
However, the fact that many subscribers share those media helps protect the
privacy of any one subscriber.
Other network types include
campus area networks (CANs) and metropolitan area networks (MANs). A CAN is
usually under the control of a single organization, such as a university or company,
and covers the adjacent buildings of one site of that organization. A MAN often
covers a city, with the communication offering of one provider in that area.
CANs, MANs, and WANs cover a wide range of possibilities; they loosely
characterize everything between LANs and Internets, the two extremes of the
networking spectrum.
Internetworks (Internets)
Networks of networks, or
internetwork networks, are sometimes called internets. An internet is a
connection of two or more separate networks, in that they are separately
managed and controlled. The most significant internetwork is known as the
Internet, because it connects so many of the other public networks.
The Internet is, in fact, a
federation of networks, loosely controlled by the Internet Society (ISOC) and
the Internet Corporation for Assigned Names and Numbers (ICANN). These
organizations enforce certain minimal rules of fair play to ensure that all
users are treated equitably, and they support standard protocols so that users
can communicate. These are the characteristics of the Internet.
Federation. Almost no general
statements can be made about Internet users or even network service providers.
Some may access the network through businesses or government organizations
whose memberships are very restrictive, while others may obtain access simply
by paying a small monthly fee.
Enormous. No one really knows
how large the Internet is. Our knowledge is incomplete in part because new
hosts are added daily, in part because one Internet access point can support
hundreds or thousands of machines connected through that single access point,
and in part because nobody has laid the basis for an accurate census. The
Internet connects many thousands of networks. In 2006, according to isc.org,
there were almost 400 million Internet hosts and well over 700 million users.
Based on past history, we can expect the size of the Internet to double each
year. Sidebar 7-1 describes the large
number of outside accesses just to one pubic news web site.
Sidebar
7-1: Traffic at a Typical Web Site
Many sites record network traffic data;
some publicize the data and many more use the data internally to monitor
performance, manage resources, or demonstrate usage. For example, the site worldpress.org
provides readers with an international view of important news: what stories are
reported and how stories are covered throughout the world. During summer 2006,
they averaged monthly 2 million visits by 800,000 visitors with over 3 million
pages viewed.
The median
length of a visit was approximately two minutes, which would correspond to a
user who read several headlines and perhaps one news story. Over 60 percent of
visits came from the United States, with approximately 20 percent from other countries
and 20 percent of undeterminable origin. Full statistics are at http://www.worldpress.org/traffic.cfm.
But these
statistics count all traffic, not just the security-relevant activity. The
security company ISS (Internet Security Systems) tracks the status of actual
Internet security risk. Its four-point scale goes from 1 (normal risk from
random malicious attacks experienced by all site administrators) to 4 (actual
or potential catastrophic security event requiring immediate defense). During a
period from April to June 2002, ISS reported 56 days at level 1, 22 at level 2,
and 7 at level 3 [ISS02].
Heterogeneous. Probably at least one of every
kind of commercially available hardware and software is connected to the
Internet. Unix is popular as the operating system at the Internet connection
point, although most other multiuser operating systems could support access.
Physically and logically exposed. Since there
is no global access control, practically any attacker can access the Internet
and, because of its complex connectivity, reach practically any resource on the
net.
Related Topics