Chapter: Security in Computing : Security in Networks
Threats in Transit: Eavesdropping and Wiretapping
Threats in Transit: Eavesdropping and Wiretapping
By now, you can see that an
attacker can gather a significant amount of information about a victim before
beginning the actual attack. Once the planning is done, the attacker is ready
to proceed. In this section we turn to the kinds of attacks that can occur.
Recall from Chapter 1 that an attacker
has many ways by which to harm in a computing environment: loss of
confidentiality, integrity, or availability to data, hardware or software,
processes, or other assets. Because a network involves data in transit, we look
first at the harm that can occur between a sender and a receiver. Sidebar 7-5 describes the ease of interception.
The easiest way to attack is
simply to listen in. An attacker can pick off the content of a communication
passing in the clear. The term eavesdrop
implies overhearing without expending any extra effort. For example, we
might say that an attacker (or a system administrator) is eavesdropping by monitoring all traffic passing through a node.
The administrator might have a legitimate purpose, such as watching for
inappropriate use of resources (for instance, visiting non-work-related web
sites from a company network) or communication with inappropriate parties (for
instance, passing files to an enemy from a military computer).
A more hostile term is
wiretap, which means intercepting communications through some effort. Passive wiretapping is just
"listening," much like eavesdropping. But active wiretapping means injecting something into the
communication. For example, Marvin could replace Manny's communications with
his own or create communications purported to be from Manny. Originally derived
from listening in on telegraph and telephone communications, the term
wiretapping usually conjures up a physical act by which a device extracts
information as it flows over a wire. But in fact no actual contact is
necessary. A wiretap can be done covertly so that neither the sender nor the
receiver of a communication knows that the contents have been intercepted.
Wiretapping works differently
depending on the communication medium used. Let us look more carefully at each
possible choice.
Cable
At the most local level, all
signals in an Ethernet or other LAN are available on the cable for anyone to
intercept. Each LAN connector (such as a computer board) has a unique address;
each board and its drivers are programmed to label all packets from its host
with its unique address (as a sender's "return address") and to take
from the net only those packets addressed to its host.
But removing only those
packets addressed to a given host is mostly a matter of politeness; there is
little to stop a program from examining each packet as it goes by. A device
called a packet sniffer can retrieve
all packets on the LAN. Alternatively, one of the interface cards can be
reprogrammed to have the supposedly unique address of another existing card on
the LAN so that two different cards will both fetch packets for one address.
(To avoid detection, the rogue card will have to put back on the net copies of
the packets it has intercepted.) Fortunately (for now), LANs are usually used
only in environments that are fairly friendly, so these kinds of attacks occur
infrequently.
Clever attackers can take
advantage of a wire's properties and read packets without any physical
manipulation. Ordinary wire (and many other electronic components) emit
radiation. By a process called inductance
an intruder can tap a wire and read radiated signals without making physical
contact with the cable. A cable's signals travel only short distances, and they
can be blocked by other conductive materials. The equipment needed to pick up
signals is inexpensive and easy to obtain, so inductance threats are a serious
concern for cable-based networks. For the attack to work, the intruder must be
fairly close to the cable; this form of attack is thus limited to situations
with reasonable physical access.
If the attacker is not close
enough to take advantage of inductance, then more hostile measures may be
warranted. The easiest form of intercepting a cable is by direct cut. If a
cable is severed, all service on it stops. As part of the repair, an attacker
can easily splice in a secondary cable that then receives a copy of all signals
along the primary cable. There are ways to be a little less obvious but
accomplish the same goal. For example, the attacker might carefully expose some
of the outer conductor, connect to it, then carefully expose some of the inner
conductor and connect to it. Both of these operations alter the resistance, called
the impedance, of the cable. In the
first case, the repair itself alters the impedance, and the impedance change
can be explained (or concealed) as part of the repair. In the second case, a
little social engineering can explain the change. ("Hello, this is Matt, a
technician with Bignetworks. We are changing some equipment on our end, and so
you might notice a change in impedance.")
Signals on a network are multiplexed, meaning that more than one
signal is transmitted at a given time. For example, two analog (sound) signals
can be combined, like two tones in a musical chord, and two digital signals can
be combined by interleaving, like playing cards being shuffled. A LAN carries
distinct packets, but data on a WAN may be heavily multiplexed as it leaves its
sending host. Thus, a wiretapper on a WAN needs to be able not only to
intercept the desired communication but also to extract it from the others with
which it is multiplexed. While this can be done, the effort involved means it
will be used sparingly.
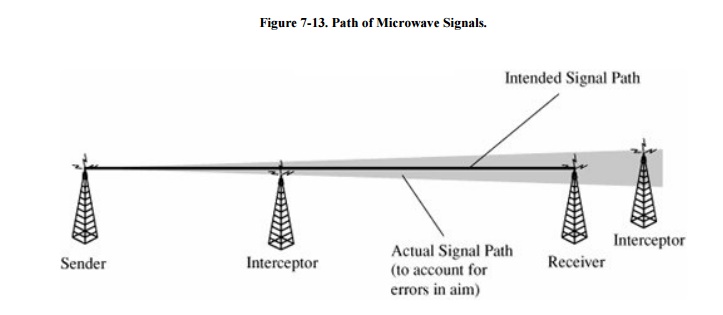
Microwave
Microwave signals are not carried along a wire;
they are broadcast through the air, making them more accessible to outsiders.
Typically, a transmitter's signal is focused on its corresponding receiver. The
signal path is fairly wide, to be sure of hitting the receiver, as shown in Figure 7-13. From a
security standpoint, the wide swath is an invitation to mischief. Not only can
someone intercept a microwave transmission by interfering with the line of sight between
sender and receiver, someone can also pick up an entire transmission from an
antenna located close to but slightly off the direct focus point.
A microwave signal is usually
not shielded or isolated to prevent interception. Microwave is, therefore, a
very insecure medium. However, because of the large volume of traffic carried
by microwave links, it is unlikelybut not impossiblethat someone will be able
to separate an individual transmission from all the others interleaved with it.
A privately owned microwave link, carrying only communications for one
organization, is not so well protected by volume.
Satellite Communication
Satellite communication has a
similar problem of being dispersed over an area greater than the intended point
of reception. Different satellites have different characteristics, but some
signals can be intercepted in an area several hundred miles wide and a thousand
miles long. Therefore, the potential for interception is even greater than with
microwave signals. However, because satellite communications are generally
heavily multiplexed, the risk is small that any one communication will be
intercepted.
Optical Fiber
Optical fiber offers two
significant security advantages over other transmission media. First, the
entire optical network must be tuned carefully each time a new connection is
made. Therefore, no one can tap an optical system without detection. Clipping
just one fiber in a bundle will destroy the balance in the network.
Second, optical fiber carries
light energy, not electricity. Light does not emanate a magnetic field as
electricity does. Therefore, an inductive tap is impossible on an optical fiber
cable.
Just using fiber, however,
does not guarantee security, any more than does using encryption. The
repeaters, splices, and taps along a cable are places at which data may be
available more easily than in the fiber cable itself. The connections from
computing equipment to the fiber may also be points for penetration. By itself,
fiber is much more secure than cable, but it has vulnerabilities too.
Wireless
Wireless networking is
becoming very popular, with good reason. With wireless (also known as WiFi),
people are not tied to a wired connection; they are free to roam throughout an
office, house, or building while maintaining a connection. Universities,
offices, and even home users like being able to connect to a network without
the cost, difficulty, and inconvenience of running wires. The difficulties of
wireless arise in the ability of intruders to intercept and spoof a connection.
As we noted earlier, wireless
communications travel by radio. In the United States, wireless computer
connections share the same frequencies as garage door openers, local radios
(typically used as baby monitors), some cordless telephones, and other very
short distance applications. Although the frequency band is crowded, few
applications are expected to be on the band from any single user, so contention
or interference is not an issue.
But the major threat is not
interference; it is interception. A wireless signal is strong for approximately
100 to 200 feet. To appreciate those figures, picture an ordinary ten-story
office building, ten offices "wide" by five offices "deep,"
similar to many buildings in office parks or on university campuses. Assume you
set up a wireless base station (receiver) in the corner of the top floor. That
station could receive signals transmitted from the opposite corner of the
ground floor. If a similar building were adjacent, the signal could also be
received throughout that building, too. (See Sidebar
7-5 on how easy it is to make a connection.) Few people would care
to listen to someone else's baby monitor, but many people could and do take
advantage of a passive or active wiretap of a network connection.
A strong signal can be picked
up easily. And with an inexpensive, tuned antenna, a wireless signal can be
picked up several miles away. In other words, someone who wanted to pick up
your particular signal could do so from several streets away. Parked in a truck
or van, the interceptor could monitor your communications for quite some time
without arousing suspicion.
Interception
Interception of wireless
traffic is always a threat, through either passive or active wiretapping. Sidebar 7-6 illustrates how software faults may
make interception easier than you might think. You may react to that threat by
assuming that encryption will address it. Unfortunately, encryption is not
always used for wireless communication, and the encryption built into some
wireless devices is not as strong as it should be to deter a dedicated
attacker.
Theft of Service
Wireless also admits a second
problem: the possibility of rogue use of a network connection. Many hosts run
the Dynamic Host Configuration Protocol (DHCP), by which a client negotiates a
one -time IP address and connectivity with a host. This protocol is useful in
office or campus settings, where not all users (clients) are active at any
time. A small number of IP addresses can be shared among users. Essentially the
addresses are available in a pool. A new client requests a connection and an IP
address through DHCP, and the server assigns one from the pool.
This scheme admits a big
problem with authentication. Unless the host authenticates users before
assigning a connection, any requesting client is assigned an IP address and
network access. (Typically, this assignment occurs before the user on the
client workstation actually identifies and authenticates to a server, so there
may not be an authenticatable identity that the DHCP server can demand.) The
situation is so serious that in some metropolitan areas a map is available,
showing many networks accepting wireless connections.
A user wanting free Internet
access can often get it simply by finding a wireless LAN offering DHCP service.
But is it legal? In separate cases Benjamin Smith III in Florida in July 2005
and Dennis Kauchak in Illinois in March 2006 were convicted of remotely
accessing a computer wirelessly without the owner's permission. Kauchak was
sentenced to a $250 fine. So, even though you are able to connect, it may not
be legal to do so.
On the other hand, some cities or organizations
make wireless access freely available as a community service. Free wireless
cities include Albuquerque and Honolulu in the United States, Oulu in Finland,
and the central districts of cities such as Hamburg, Germany, and Adelaide,
Australia. The cities hope that providing free access will spur IT growth and
attract tourists and business travelers.
Sidebar
7-6: Wireless Vulnerabilities
The New Zealand Herald [GRI02]
reports that a major telecommunications company was forced to shut down its
mobile e-mail service because of a security flaw in its wireless network
software. The flaw affected users on the company's CDMA network who were
sending e-mail on their WAP-enabled (wireless applications protocol) mobile
phones.
The vulnerability occurred when the user
finished an e-mail session. In fact, the software did not end the WAP session
for 60 more seconds. If a second network customer were to initiate an e-mail
session within those 60 seconds and be connected to the same port as the first
customer, the second customer could then view the first customer's message.
The company blamed the third-party
software provided by a mobile portal. Nevertheless, the company was highly
embarrassed, especially because it "perceived security issues with
wireless networks" to be "a major factor threatening to hold the
[wireless] technology's development back." [GRI02]
But perceivedand realsecurity issues
should hold back widespread use of wireless. It is estimated that 85 percent of
wireless users do not enable encryption on their access points, and weaknesses
in the WEP protocol leave many of the remaining 15 percent vulnerable.
Anyone with a wireless network card can
search for an available network. Security consultant Chris O'Ferrell has been
able to connect to wireless networks in Washington D.C. from outside a Senate
office building, the Supreme Court, and the Pentagon [NOG02]; others
join networks in airports, on planes, and at coffee shops. Internet bulletin
boards have maps of metropolitan areas with dots showing wireless access
points. The so-called parasitic grid movement is an underground attempt to
allow strangers to share wireless Internet access in metropolitan areas. A
listing of some of the available wireless access points by city is maintained
at www.guerilla.net/freenets.html. Products like AirMagnet from
AirMagnet, Inc., Observer from Network Instruments, and IBM's Wireless Security
Analyzer can locate open wireless connections on a network so that a security
administrator can know a network is open to wireless access.
And then
there are wireless LAN users who refuse to shut off their service. Retailer
BestBuy was embarrassed by a customer who bought a wireless product. While in
the parking lot, he installed it in his laptop computer. Much to his surprise,
he found he could connect to the store's wireless network. BestBuy subsequently
took all its wireless cash registers offline. But the CVS pharmacy chain
announced plans to continue use of wireless networks in all 4100 of its stores,
arguing "We use wireless technology strictly for internal item management.
If we were to ever move in the direction of transmitting [customer] information
via in-store wireless LANs, we would encrypt the data" [BRE02].
Summary of Wiretapping
There are many points at which network traffic
is available to an interceptor. Figure 7-14
illustrates how communications are exposed from their origin to their
destination.
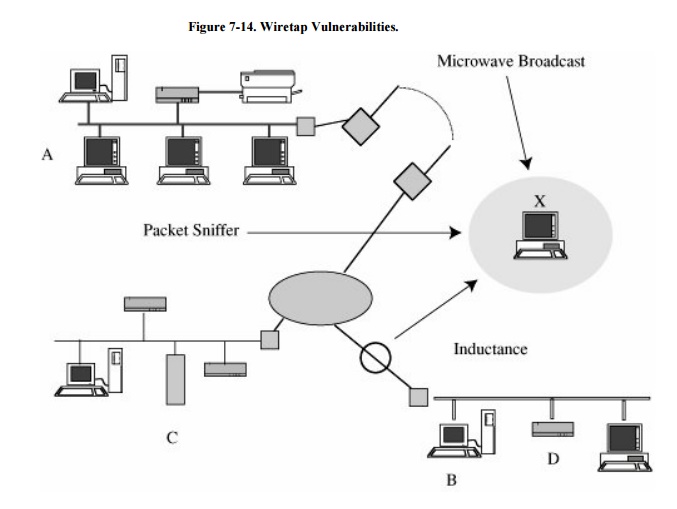
From a security standpoint,
you should assume that all communication links between network nodes can be
broken. For this reason, commercial network users employ encryption to protect
the confidentiality of their communications, as we demonstrate later in this
chapter. Local network communications can be encrypted, although for
performance reasons it may be preferable to protect local connections with
strong physical and administrative security instead.
Related Topics