Chapter: Security in Computing : Security in Networks
Network Concepts
Network Concepts
To study network threats and
controls, we first must review some of the relevant networking terms and
concepts. This review does not attempt to provide the depth of a classic
networking reference, such as [COM04, STE02, GAL99,
or TAN03]. In earlier chapters, our
study of security focused on the individual pieces of a computing system, such
as a single application, an operating system, or a database. Networks involve
not only the pieces but alsoimportantlythe connections among them.
Networks are both fragile and strong. To see why, think about the
power, cable television, telephone, or water network that serves your home. If
a falling tree branch breaks the power line to your home, you are without
electricity until that line is repaired; you are vulnerable to what is called a
single point of failure, because one
cut to the network destroys electrical functionality for your entire home.
Similarly, there may be one telephone trunk line or water main that serves your
home and those nearby; a failure can leave your building, street, or
neighborhood without service. But we have ways to keep the entire network from
failing. If we trace back through the network from your home to the source of
what flows through it, we are likely to see that several main distribution
lines support an entire city or campus. That is, there is more than one way to
get from the source to your neighborhood, enabling engineers to redirect the
flow along alternative paths. Redundancy makes it uncommon for an entire city
to lose service from a single failure. For this reason, we say that such a
network has resilience or fault tolerance.
Complex routing algorithms
reroute the flow not just around failures but also around overloaded segments.
The routing is usually done automatically; the control program is often
supplemented by human supervision or intervention. Many types of networks have
very high reliability by design, not by accident. But because there often is
less redundancy near a network's endpoints than elsewhere, we say that the
network has great strength in the middle and fragility at the perimeter.
From the user's perspective,
a network is sometimes designed so that it looks like two endpoints with a
single connection in the middle. For example, the municipal water supply may
appear to be little more than a reservoir (the source), the pipes (the
transmission or communication medium), and your water faucet (the destination).
Although this simplistic view is functionally correct, it ignores the complex
design, implementation, and management of the "pipes." In a similar
way, we describe computer networks in this chapter in ways that focus on the
security concepts but present the networks themselves in a simplistic way, to
highlight the role of security and prevent the complexity of the networks from
distracting our attention. Please keep in mind that our network descriptions
are often abstractions of a more complex actuality.
The Network
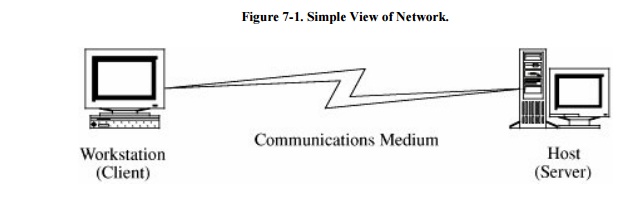
Figure 7-1 shows a network
in its simplest form, as two devices connected across some medium by hardware
and software that enable the communication. In some cases, one device is a computer
(sometimes called a "server")
and the other is a simpler device (sometimes called a "client") enabled only with some
means of input (such as a keyboard) and some means of output (such as a
screen). For example, a powerful computer can be a server, but a handheld
personal digital assistant (PDA) or a cell phone might be a network client. In
fact, because more consumer devices are becoming network-enabled, network
security issues will continue to grow.
Although this model defines a
basic network, the actual situation is frequently significantly more
complicated.
·
The simpler client device, employed for user-to-computer
communication, is often a PC or workstation, so the client has considerable
storage and processing capability.
·
A network can be configured as just a single client connected to a
single server. But more typically, many clients interact with many servers.
·
The network's services are often provided by many computers. As a
single user's communication travels back and forth from client to server, it
may merely pass through some computers but pause at others for significant
interactions.
·
The end user is usually unaware of many of the communications and
computations taking place in the network on the user's behalf.
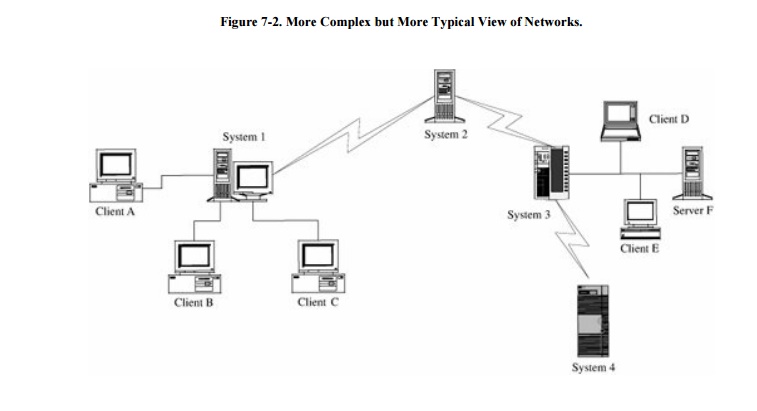
Most real-world situations
are more like Figure 7-2. In this second
view, the user at one of the lettered client machines may send a message to
System 3, unaware that communication is actually passing through the active
Systems 1 and 2. In fact, the user may be unaware that System 3 sometimes
passes work to System 4.
A single computing system in a network is often
called a node, and its processor
(computer) is called a host. A
connection between two hosts is known as a link.
Network computing consists of users, communications media, visible hosts, and
systems not generally visible to end users. In Figure
7-2, Systems 1 through 4 are nodes. In our figure the users are at
the lettered client machines, perhaps interacting with Server F.
Users communicate with
networked systems by interacting directly with terminals, workstations, and
computers. A workstation is an end -
user computing device, usually designed for a single user at a time.
Workstations often have powerful processors and good-sized memory and storage
so that they can do sophisticated data manipulation (such as converting coded
data to a graphical format and displaying the picture). A system is a
collection of processors, perhaps including a mixture of workstations and
independent processors, typically with more processing power and more storage
capacity than a workstation.
Environment of Use
The biggest difference between a network and a
stand-alone device is the environment in which each operates. Although some
networks are located in protected spaces (for example, a local area network in
a single laboratory or office), at least some portion of most networks is
exposed, often to total strangers. The relatively simple network in Figure 7-2 is a good example. Systems 2, 3, and 4
are remote from System 1, and they may be under different ownership or control.
Networks can be described by
several typical characteristics:
Anonymity. You may have seen the cartoon image that shows a dog typing at a
workstation, and saying to another dog, "On the Internet, nobody knows you're a dog." A network removes most
of the clues, such as appearance, voice, or context, by which we recognize
acquaintances.
Automation. In some networks,
one or both endpoints, as well as all intermediate points, involved in a given
communication may be machines with only minimal human supervision.
Distance. Many networks
connect endpoints that are physically far apart. Although not all network
connections involve distance, the speed of communication is fast enough that
humans usually cannot tell whether a remote site is near or far.
Opaqueness. Because the
dimension of distance is hidden, users cannot tell whether a remote host is in the
room next door or in a different country. In the same way, users cannot
distinguish whether they are connected to a node in an office, school, home, or
warehouse, or whether the node's computing system is large or small, modest or
powerful. In fact, users cannot tell if the current communication involves the
same host with which they communicated the last time.
Routing diversity. To
maintain or improve reliability and performance, routings between two endpoints
are usually dynamic. That is, the same interaction may follow one path through
the network the first time and a very different path the second time. In fact,
a query may take a different path from the response that follows a few seconds
later.
Shape and Size
The way a network is configured, in terms of
nodes and connections, is called the network topology. You can think of the topology as the shape of the
network. The topology ranges from very simple, such as two hosts connected by
one path, to very complex, such as the Internet. These two extremes highlight
three dimensions of networks that have particular bearing on a network's
security.
Boundary. The boundary distinguishes an element of the network from an
element outside it. For a simple network, we can easily list all the components and draw an imaginary line around it to
separate what is in the network from what is outside. But listing all the hosts
connected to the Internet is practically impossible. For example, a line
surrounding the Internet would have to surround the entire globe today, and
Internet connections also pass through satellites in orbit around the earth.
Moreover, as people and organizations choose to be connected or not, the number
and type of hosts change almost second by second, with the number generally
increasing over time.
Ownership. It is often difficult to know who owns each host in a network. The
network administrator's organization may own the network infrastructure, including the cable and network devices.
However, certain hosts may be connected to a network for convenience, not
necessarily implying ownership.
Control. Finally, if ownership is uncertain, control must be, too. To see
how, pick an arbitrary host. Is it part of network A? If yes, is it under the control of network A's
administrator? Does that administrator establish access control policies for
the network, or determine when its software must be upgraded and to what
version? Indeed, does the administrator even know what version of software that
host runs?
The truth is that, for many
networks, it is difficult and at times impossible to tell which hosts are part
of that network, who owns the hosts, and who controls them. Even for networks
significantly smaller than the Internet, major corporate, university, or
government networks are hard to understand and are not even well known by their
system administrators. Although it seems contrary to common sense, many
corporations today have no accurate picture of how their networks are
configured. To understand why, consider a network of automated teller machines
for a multinational bank. The bank may have agreements with other banks to
enable customers to withdraw money anywhere in the world. The multinational
bank may understand its own bank's network, but it may have no conception of
how the connecting banks' networks are configured; no "big picture"
shows how the combined networks look or operate. Similarly, a given host may be
part of more than one network. In such a situation, suppose a host has two
network interfaces. Whose rules does that host (and that host's administrator)
have to follow?
Depicting, configuring, and
administering networks are not easy tasks.
Mode of Communication
A computer network implements
communication between two endpoints. Data are communicated either in digital format (in which data items are
expressed as discrete binary values) or analog
(in which data items are expressed as points in a continuous range, using a
medium like sound or electrical voltage). Computers typically store and process
digital data, but some telephone and similar cable communications are in analog
form (because telephones were originally designed to transmit voice). When the
transmission medium expects to transfer analog data, the digital signals must
be converted to analog for transmission and then back to digital for
computation at the receiving end. Some mostly analog networks may even have
some digital segments, so the analog signals are digitized more than once.
These conversions are performed by a modem
(the term is derived from modulator-demodulator), which converts a digital data
stream to tones and back again.
Related Topics