Chapter: Security in Computing : Security in Networks
Threats in Networks
Threats in Networks
![]()
Up to now, we have reviewed
network concepts with very little discussion of their security implications.
But our earlier discussion of threats and vulnerabilities, as well as outside
articles and your own experiences, probably have you thinking about the many
possible attacks against networks. This section describes some of the threats
you have already hypothesized and perhaps presents you with some new ones. But
the general thrust is the same: threats aimed to compromise confidentiality,
integrity, or availability, applied against data, software, and hardware by
nature, accidents, nonmalicious humans, and malicious attackers.
What Makes a Network Vulnerable?
An isolated home user or a
stand-alone office with a few employees is an unlikely target for many attacks.
But add a network to the mix and the risk rises sharply. Consider how a network
differs from a stand-alone environment:
·
Anonymity. An attacker can mount an attack from thousands of miles
away and never come into direct contact with the system, its administrators, or
users. The potential attacker is thus safe behind an electronic shield. The
attack can be passed through many other hosts in an effort to disguise the
attack's origin. And computer-to-computer authentication is not the same for
computers as it is for humans; as illustrated by Sidebar
7-2, secure distributed authentication requires thought and
attention to detail.
·
Many points of attackboth targets and origins. A simple computing
system is a self-contained unit. Access controls on one machine preserve the
confidentiality of data on that processor. However, when a file is stored in a
network host remote from the user, the data or the file itself may pass through
many hosts to get to the user. One host's administrator may enforce rigorous
security policies, but that administrator has no control over other hosts in
the network. Thus, the user must depend on the access control mechanisms in
each of these systems. An attack can come from any host to any host, so that a
large network offers many points of vulnerability.
·
Sharing. Because networks enable resource and workload sharing, more
users have the potential to access networked systems than on single computers.
Perhaps worse, access is afforded to more systems, so that access controls for
single systems may be inadequate in networks.
·
Complexity of system. In Chapter 4
we saw that an operating system is a complicated piece of software. Reliable
security is difficult, if not impossible, on a large operating system,
especially one not designed specifically for security. A network combines two
or more possibly dissimilar operating systems. Therefore, a network
operating/control system is likely to be more complex than an operating system
for a single computing system. Furthermore, the ordinary desktop computer today
has greater computing power than did many office computers in the last two
decades. The attacker can use this power to advantage by causing the victim's
computer to perform part of the attack's computation. And because an average
computer is so powerful, most users do not know what their computers are really
doing at any moment: What processes are active in the background while you are
playing Invaders from Mars? This complexity diminishes confidence in the
network's security.
Sidebar 7-2: Distributed Authentication in Windows NT and 2000
Authentication must be handled carefully
and correctly in a network because a network involves authentication not just
of people but of processes, servers, and services only loosely associated with
a person. And for a network, the authentication process
and database are often distributed for performance and reliability. Consider
Microsoft's authentication scheme for its Windows operating systems. In Windows
NT 4.0, the authentication database is distributed among several domain
controllers. Each domain controller is designated as a primary or backup
controller. All changes to the authentication database must be made to the
(single) primary domain controller; then the changes are replicated from the
primary to the backup domain controllers.
In Windows 2000, the concept of primary
and backup domain controllers has been abandoned. Instead, the network views
the controllers as equal trees in a forest, in which any domain controller can
update the authentication database. This scheme reflects Microsoft's notion
that the system is "multimaster": Only one controller can be master
at a given time, but any controller can be a master. Once changes are made to a
master, they are automatically replicated to the remaining domain controllers
in the forest.
This approach is more flexible and robust
than the primary-secondary approach because it allows any controller to take
chargeespecially useful if one or more controllers have failed or are out of
service for some reason. But the multimaster approach introduces a new problem.
Because any domain controller can initiate changes to the authentication
database, any hacker able to dominate a domain controller can alter the
authentication database. And, what's worse, the changes are then replicated
throughout the remaining forest. Theoretically, the hacker could access
anything in the forest that relies on Windows 2000 for authentication.
When we think of attackers, we usually
think of threats from outside the system. But in fact the multimaster approach
can tempt people inside the system, too. A domain administrator in any domain
in the forest can access domain controllers within that domain. Thanks to
multimaster, the domain administrator can also modify the authentication
database to access anything else in the forest.
For this reason, system administrators must consider how they define
domains and their separation in a network. Otherwise, we can conjure up scary
but possible scenarios. For instance, suppose one domain administrator is a bad
apple. She works out a way to modify the authentication database to make
herself an administrator for the entire forest. Then she can access any data in
the forest, turn on services for some users, and turn off services for other
users.
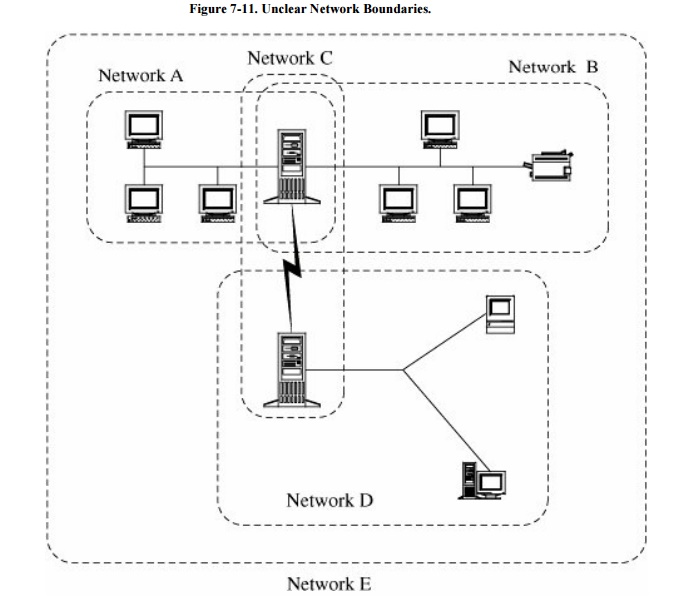
Unknown perimeter. A
network's expandability also implies uncertainty about the network boundary.
One host may be a node on two different networks, so resources on one network
are accessible to the users of the other network as well. Although wide
accessibility is an advantage, this unknown or uncontrolled group of possibly
malicious users is a security disadvantage. A similar problem occurs when new
hosts can be added to the network. Every network node must be able to react to
the possible presence of new, untrustable hosts. Figure
7-11 points out the problems in defining the boundaries of a
network. Notice, for example, that a user on a host in network D may be unaware
of the potential connections from users of networks A and B. And the host in
the middle of networks A and B in fact belongs to A, B, C, and E. If there are
different security rules for these networks, to what rules is that host
subject?
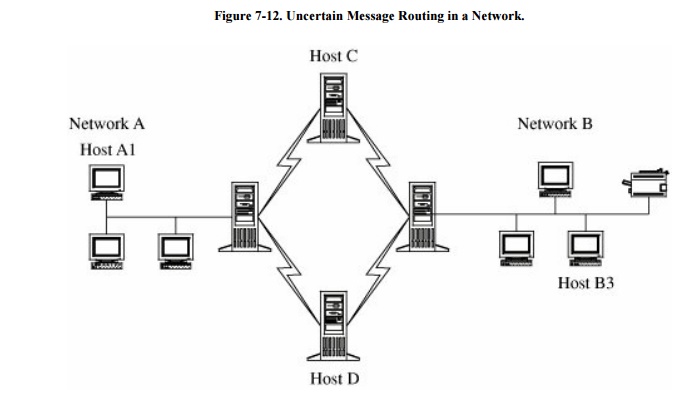
Unknown path. Figure 7-12 illustrates that there may be many
paths from one host to another. Suppose that a user on host A1 wants to send a
message to a user on host B3. That message might be routed through hosts C or D
before arriving at host B3. Host C may provide acceptable security, but not D.
Network users seldom have control over the routing of their messages.
Thus, a network differs
significantly from a stand-alone, local environment. Network characteristics
significantly increase the security risk.
Related Topics