Chapter: Security in Computing : Security in Networks
Distributed Denial of Service
Distributed Denial of Service
The denial-of -service
attacks we have listed are powerful by themselves, and Sidebar 7-7 shows us that many are launched. But
an attacker can construct a two-stage attack that multiplies the effect many
times. This multiplicative effect gives power to distributed denial of service.
To perpetrate a distributed denial-of-service (or DDoS) attack, an attacker does
two things, as illustrated in Figure 7 -18.
In the first stage, the attacker uses any convenient attack (such as exploiting
a buffer overflow or tricking the victim to open and install unknown code from
an e-mail attachment) to plant a Trojan horse on a target machine. That Trojan
horse does not necessarily cause any harm to the target machine, so it may not
be noticed. The Trojan horse file may be named for a popular editor or utility,
bound to a standard operating system service, or entered into the list of
processes (daemons) activated at startup. No matter how it is situated within
the system, it will probably not attract any attention.
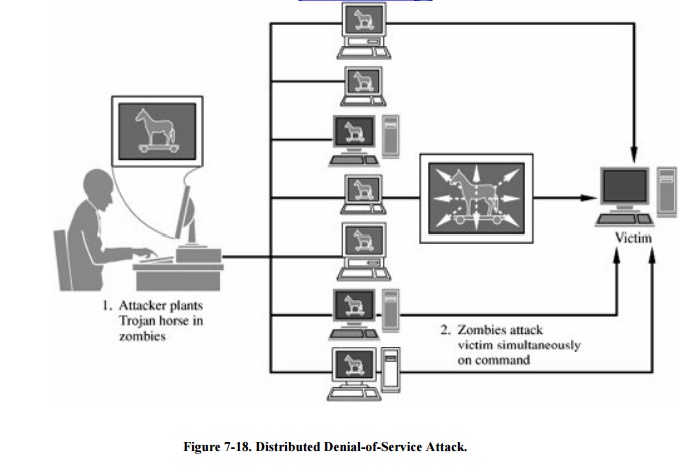
The attacker repeats this process with many
targets. Each of these target systems then becomes what is known as a zombie. The target systems carry out
their normal work, unaware of the resident zombie.
Sidebar
7-7: How Much Denial-of-Service Activity Is There?
Researchers at the University of
California, San Diego (UCSD) studied the amount of denial-of-service activity
on the Internet [UCS01]. Because many DOS attacks use a fictitious
return address, the researchers asserted that traffic to nonexistent addresses
was indicative of the amount of denial-of-service attacking. They monitored a
large, unused address space on the Internet for a period of three weeks. They
found
·
More than 12,000 attacks were
aimed at more than 5,000 targets during the three-week period.
·
Syn floods likely accounted
for more than half of the attacks.
·
Half the attacks lasted less
than ten minutes, and 90 percent of attacks lasted less than an hour.
Steve
Gibson of Gibson Research Corporation (GRC) experienced several
denial-of-service attacks in mid-2001. He collected data for his own forensic
purposes [GIB01]. The first attack lasted 17 hours, at which point he
was able to reconfigure the router connecting him to the Internet so as to
block the attack. During those 17 hours he found his site was attacked by 474
Windows-based PCs. A later attack lasted 6.5 hours before it stopped by itself.
These attacks were later found to have been launched by a 13-year old from
Kenosha, Wisconsin.
At some point the attacker
chooses a victim and sends a signal to all the zombies to launch the attack.
Then, instead of the victim's trying to defend against one denial-of-service
attack from one malicious host, the victim must try to counter n attacks from
the n zombies all acting at once. Not all of the zombies need to use the same
attack; for instance, some could use smurf attacks and others, could use syn
floods to address different potential weaknesses.
In addition to their tremendous multiplying
effect, distributed denial-of-service attacks are a serious problem because
they are easily launched from scripts. Given a collection of denial-of-service
attacks and a Trojan horse propagation method, one can easily write a procedure
to plant a Trojan horse that can launch any or all of the denial- of-service
attacks. DDoS attack tools first appeared in mid-1999. Some of the original
DDoS tools include Tribal Flood Network
(TFN), Trin00 , and TFN2K (Tribal Flood Network, year 2000
edition). As new vulnerabilities are discovered that allow Trojan horses to be
planted and as new denial-of-service attacks are found, new combination tools
appear. For more details on this topic, see [HAN00a].
According to the U.S. Computer
Emergency Response Team (CERT) [HOU01a]
, scanning to find a vulnerable host (potential zombie) is now being included
in combination tools; a single tool now identifies its zombie, installs the
Trojan horse, and activates the zombie to wait for an attack signal. Recent
target (zombie) selection has been largely random, meaning that attackers do
not seem to care which zombies they infect. This revelation is actually bad
news, because it means that no organization or accessible host is safe from attack.
Perhaps because they are so numerous and because their users are assumed to be
less knowledgeable about computer management and protection, Windows-based
machines are becoming more popular targets for attack than other systems. Most
frightening is the CERT finding that the time is shrinking between discovery of
a vulnerability and its widespread exploitation.
Related Topics