Chapter: Security in Computing : Security in Networks
Networks Complex Attacks
Complex Attacks
As if these vulnerabilities
were not enough, two other phenomena multiply the risk. Scripts let people
perform attacks even if the attackers do not understand what the attack is or
how it is performed. Building blocks let people combine components of an
attack, almost like building a house from prefabricated parts.
Script Kiddies
Attacks can be scripted. A
simple smurf denial -of-service attack is not hard to implement. But an
underground establishment has written scripts for many of the popular attacks.
With a script, attackers need not understand the nature of the attack or even
the concept of a network. The attackers merely download the attack script (no
more difficult than downloading a newspaper story from a list of headlines) and
execute it. The script takes care of selecting an appropriate (that is,
vulnerable) victim and launching the attack.
The hacker community is
active in creating scripts for known vulnerabilities. For example, within three
weeks of a CERT advisory for a serious SNMP vulnerability in February 2002 [CER02], scripts had appeared. These scripts
probed for the vulnerability's existence in specific brands and models of
network devices; then they executed attacks when a vulnerable host was found.
People who download and run
attack scripts are called script kiddies.
As the rather derogatory name implies, script kiddies are not well respected in
the attacker community because the damage they do requires almost no creativity
or innovation. Nevertheless, script kiddies can cause serious damage, sometimes
without even knowing what they do.
Building Blocks
This chapter's attack types
do not form an exhaustive list, but they represent the kinds of vulnerabilities
being exploited, their sources, and their severity. A good attacker knows these
vulnerabilities and many more.
An attacker simply out to
cause minor damage to a randomly selected site could use any of the techniques
we have described, perhaps under script control. A dedicated attacker who
targets one location can put together several pieces of an attack to compound
the damage. Often, the attacks are done in series so that each part builds on
the information gleaned from previous attacks. For example, a wiretapping
attack may yield reconnaissance information with which to form an ActiveX
attack that transfers a Trojan horse that monitors for sensitive data in
transmission. Putting the attack pieces together like building blocks expands
the number of targets and increases the degree of damage.
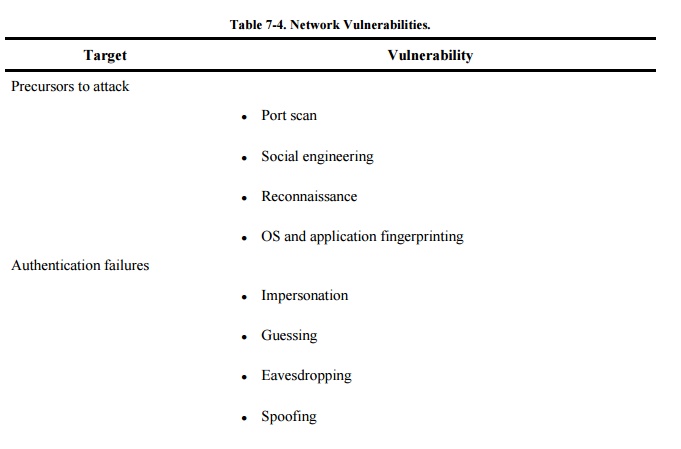
Summary of Network Vulnerabilities
A network has many different vulnerabilities,
but all derive from an underlying model of computer, communications, and
information systems security. Threats are raised against the key aspects of
security: confidentiality, integrity, and availability, as shown in Table 7-4.



Related Topics