Chapter: Cryptography and Network Security
Trusted systems
Trusted systems
One way
to enhance the ability of a system to defend against intruders and malicious
programs is to implement trusted system technology.
1. Data access control
Following
successful logon, the user has been granted access to one or set of hosts and
applications. This is generally not sufficient for a system that includes sensitive
data in its database. Through the user access control procedure, a user can be
identified to the system. Associated with each user, there can be a profile
that specifies permissible operations and file accesses. The operating system
can then enforce rules based on the user profile. The database management
system, however, must control access to specific records or even portions of
records. The operating system may grant a user permission to access a file or
use an application, following which there are no further security checks, the
database management system must make a decision on each individual access
attempt. That decision will depend not only on the user‟s identity but also on
the specific parts of the data being accessed and even on the information
already divulged to the user.
A general
model of access control as exercised by an file or database management system
is that of an access matrix. The basic elements of the model are as follows:
·
Subject: An
entity capable of accessing objects. Generally, the concept of subject equates with that of process.
·
Object:
Anything to which access is controlled. Examples include files, portion of
files, programs, and segments of memory.
·
Access
right: The way in which the object is accessed by a subject. Examples are read, write and execute.
One axis
of the matrix consists of identified subjects that may attempt data access.
Typically, this list will consist of individual users or user groups. The other
axis lists the objects that may be accessed. Objects may be individual data
fields. Each entry in the matrix indicates the access rights of that subject
for that object. The matrix may be decomposed by columns, yielding access control lists. Thus, for each
object, an access control list lists users and their permitted access rights.
The access control list may contain a default, or public, entry.
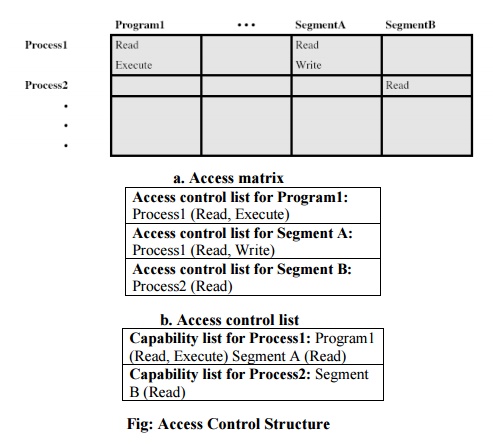
Decomposition
by rows yields capability tickets. A
capability ticket specifies authorized objects and operations for a user. Each
user has a number of tickets and may be authorized to loan or give them to
others. Because tickets may be dispersed around the system, they present a
greater security problem than access control lists. In particular, the ticket
must be unforgeable. One way to accomplish this is to have the operating system
hold all tickets on behalf of users. These tickets would have to be held in a
region of memory inaccessible to users.
2. The concept of Trusted Systems
When
multiple categories or levels of data are defined, the requirement is referred
to as multilevel security. The general statement of the requirement for
multilevel security is that a subject at a high level may not convey
information to a subject at a lower or noncomparable level unless that flow accurately
reflects the will of an authorized user. For implementation purposes, this
requirement is in two parts and is simply stated. A multilevel secure system
must enforce:
·
No read
up: A subject
can only read an object of less or equal security level. This is referred to as simple security property.
·
No write
down: A subject can only write into an object of greater or equal security
level.
This is
referred to as *-property (star
property).
These two
rules, if properly enforced, provide multilevel security.
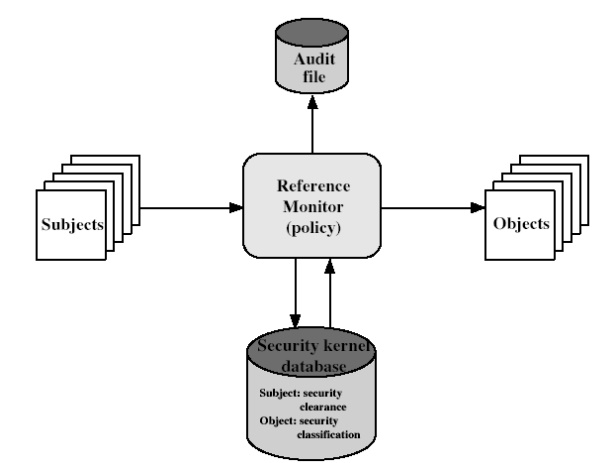
3. Reference Monitor concept
The
reference monitor is a controlling element in the hardware and operating system
of a computer that regulates the access of subjects to objects on the basis of
security parameters of the subject and object. The reference monitor has access
to a file, known as the security kernel database that lists the access
privileges (security clearance) of each subject and the protection attributes
(classification level) of each object. The reference monitor enforces the
security rules and has the following properties:
Complete mediation: The security rules are enforced on every access, not just, for example, when a file is opened.
Isolation: The reference monitor and database are protected from unauthorised modification.
Verifiability: The reference monitor‟s correctness must be provable.
That is, it must be
possible to demonstrate mathematically that the reference monitor enforces the
security rules and provides complete mediation and isolation. Important
security events, such as detected security violations and authorized changes to
the security kernel database, are stored in the audit file
Related Topics