Chapter: Cryptography and Network Security
Simplified Data Encryption Standard (S-DES)
SIMPLIFIED DATA ENCRYPTION
STANDARD (S-DES)
The
overall structure of the simplified DES. The S-DES encryption algorithm takes
an 8-bit block of plaintext (example: 10111101) and a 10-bit key as input and
produces an 8-bit block of ciphertext as output. The S-DES decryption algorithm
takes an 8-bit block of ciphertext and the same 10-bit key used to produce that
ciphertext as input and produces the original 8-bit block of plaintext.
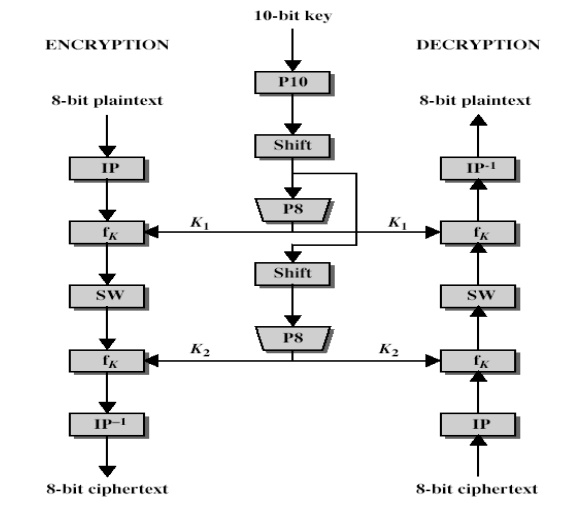
The encryption algorithm involves five functions:
an
initial permutation (IP)
a complex
function labeled fk, which involves both permutation and
substitution operations and depends on a key input
a simple
permutation function that switches (SW) the two halves of the data
the
function fk again
a
permutation function that is the inverse of the initial permutation
The
function fk takes as input not only the data passing through the
encryption algorithm, but also an 8-bit key. Here a 10-bit key is used from
which two 8-bit subkeys are generated. The key is first subjected to a
permutation (P10). Then a shift operation is performed. The output of the shift
operation then passes through a permutation function that produces an 8-bit
output (P8) for the first subkey (K1). The output of the shift operation also
feeds into another shift and another instance of P8 to produce the second
subkey (K2).
The
encryption algorithm can be expressed as a composition composition1 of
functions: IP-1 ο fK2 ο SW ο fk1 ο IP
Which can
also be written as
Ciphertext
= IP-1 (fK2 (SW (fk1 (IP (plaintext)))))
Where
K1 = P8
(Shift (P10 (Key)))
K2 = P8
(Shift (shift (P10 (Key))))
Decryption
can be shown as
Plaintext
= IP-1 (fK1 (SW (fk2 (IP (ciphertext)))))
1. S-DES key generation
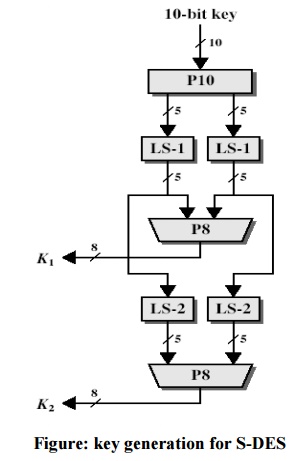
S-DES depends on the use of a 10-bit key shared between sender and receiver. From this key, two 8-bit subkeys are produced for use in particular stages of the encryption and decryption algorithm. First, permute the key in the following fashion. Let the 10-bit key be designated as (k1, K2, k3, k4, k5, k6, k7, k8, k9, k10). Then the permutation P10 is defined as:
P10 (k1,
K2, k3, k4, k5, k6, k7, k8, k9, k10) = (k3, k5, K2, k7, k4, k10 10, k1, k9, k8,
k6) P10 can be concisely defined by the display:
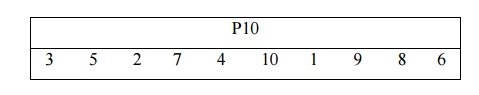
This
table is read from left to right; each position in the table gives the identity
of the input bit that produces the output bit in that position. So the first
output bit is bit 3 of the input; the second output bit is bit 5 of the input,
and so on. For example, the key (1010000010) is permuted to (10000 01100).
Next, perform a circular left shift (LS-1), or rotation, separately on the
first five bits and the second five bits. In our example, the result is (00001
11000). Next we apply P8, which picks out and permutes 8 of the 10 bits
according to the following rule:
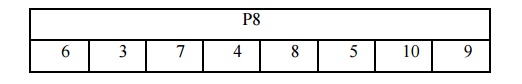
The
result is subkey 1 (K1). In our example, this yields (10100100). We then go
back to the pair of 5-bit strings produced by the two LS-1 functions and
performs a circular left shift of 2 bit positions on each string. In our
example, the value (00001 11000) becomes (00100 00011). Finally, P8 is applied
again to produce K2. In our
example, the result is (01000011).
2 S-DES encryption
Encryption
involves the sequential application of five functions.
Initial and Final Permutations
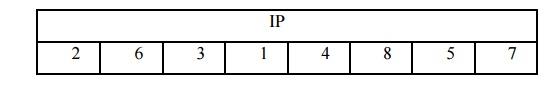
The input
to the algorithm is an 8-bit block of plaintext, which we first permute using
the IP function:
This
retains all 8 bits of the plaintext but mixes them up.
Consider
the plaintext to be 11110011.
Permuted
output = 10111101
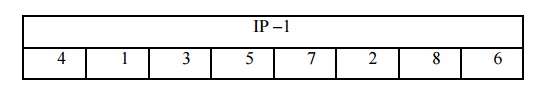
At the
end of the algorithm, the inverse permutation is used:
The Function fk
The most
complex component of S-DES is the function fk, which consists of a
combination of permutation and substitution functions. The functions can be
expressed as follows. Let L and R be the leftmost 4 bits and rightmost 4 bits
of the 8-bit input to f K, and let F be a mapping (not necessarily one to one)
from 4-bit strings to 4-bit strings. Then we let

We now
describe the mapping F. The input is a 4-bit number (n1 n2 n3 n4). The first
operation is an expansion/permutation operation:
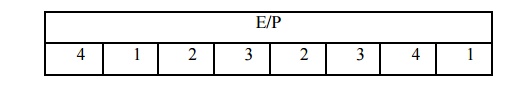
e.g., R= 1101
E/P
output = 11101011
It is
clearer to depict the result in this fashion:
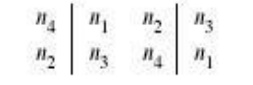
The 8-bit
subkey K1 = (k11, k12 12, k13 13, k14 14, k15 15, k16 16, k17 17, k18) is added to this value using
exclusive-OR:
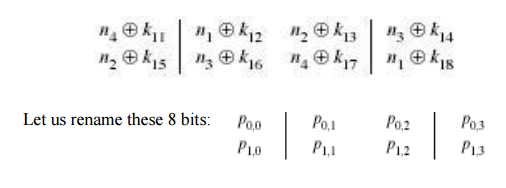
The first
4 bits (first row of the preceding matrix) are fed into the S-box S0 to produce
a 2- bit output, and the remaining 4 bits (second row) are fed into S1 to
produce another 2-bit output.
These two
boxes are defined as follows:
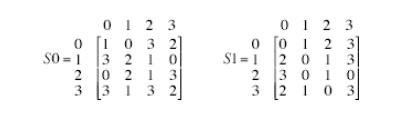
The
S-boxes operate as follows. The first and fourth input bits are treated as a
2-bit number that specify a row of the S-box, and the second and third input
bits specify a column of the S-box. The entry in that row and column, in base
2, is the 2-bit output. For example, if (p0,0 p0,3) = ) (00) and ( p0,1 p0,2) = (10), then the output is from row 0, column 2 of S0, which is 3, or (11) in ) binary. Similarly, (p1,0 p1,3) and ( p1,1 p1,2) are used to index into a row
and column of S1 to produce an additional 2 bits. Next, the 4 bits produced by
S0 and S1 undergo a further permutation as follows:
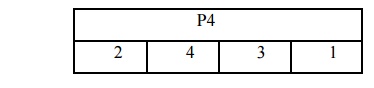
The
output of P4 is the output of the function F.
3 The Switch Function
The
function f K only alters the leftmost 4 bits of the input. The switch function
(SW) interchanges the left and right 4 bits so that the second instance of f K
operates on a different 4 bits. In this second instance, the E/P, S0, S1, and
P4 functions are the same. The key input is K2.
Finally apply inverse permutation to get the ciphertext.
Related Topics