Chapter: Cryptography and Network Security
Modes of Operation
Modes of Operation
block ciphers encrypt fixed size blocks
eg. DES encrypts 64-bit blocks with 56-bit key
need some way to en/decrypt arbitrary amounts of data in practise
ANSI X3.106-1983 Modes of Use (now FIPS
81) defines 4 possible modes
subsequently 5 defined for AES & DES
have block and stream modes
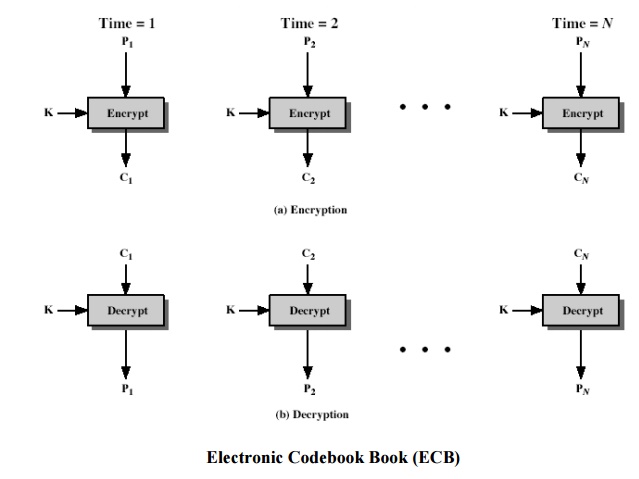
1 Electronic Codebook Book (ECB)
message
is broken into independent blocks which are encrypted
each
block is a value which is substituted, like a codebook, hence name
each
block is encoded independently of the other blocks
Ci = DESK1(Pi)
uses:
secure transmission of single values
Advantages and Limitations of ECB
message
repetitions may show in ciphertext
if aligned with message block
particularly with data such graphics
or with messages that change very little, which become a code-book
analysis problem
weakness
is due to the encrypted message blocks being independent
main use
is sending a few blocks of data
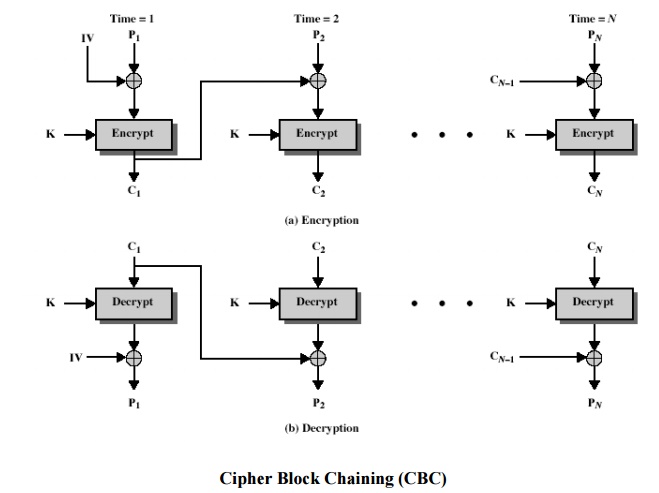
2 Cipher Block Chaining (CBC)
message
is broken into blocks
linked
together in encryption operation
each
previous cipher blocks is chained with current plaintext block, hence name
use
Initial Vector (IV) to start process
Ci = DESK1(Pi XOR Ci-1)
C-1 = IV
uses:
bulk data encryption, authentication
3 Message Padding
at end of
message must handle a possible last short block
which is not as large as blocksize of cipher
pad either with known non-data value (eg nulls)
or pad last block along with count of pad size o eg. [ b1 b2 b3 0 0 0 0 5]
means
have 3 data bytes, then 5 bytes pad+count
this may require an extra entire block over those in message
there are
other, more esoteric modes, which avoid the need for an extra block
Advantages and Limitations of CBC
a
ciphertext block depends on all
blocks before it
any
change to a block affects all following ciphertext blocks
need Initialization Vector (IV)
which must be known to sender & receiver
if sent in clear, attacker can change bits of first block, and change IV
to compensate
hence IV must either be a fixed value (as in EFTPOS)
or must be sent encrypted in ECB mode before rest of Message
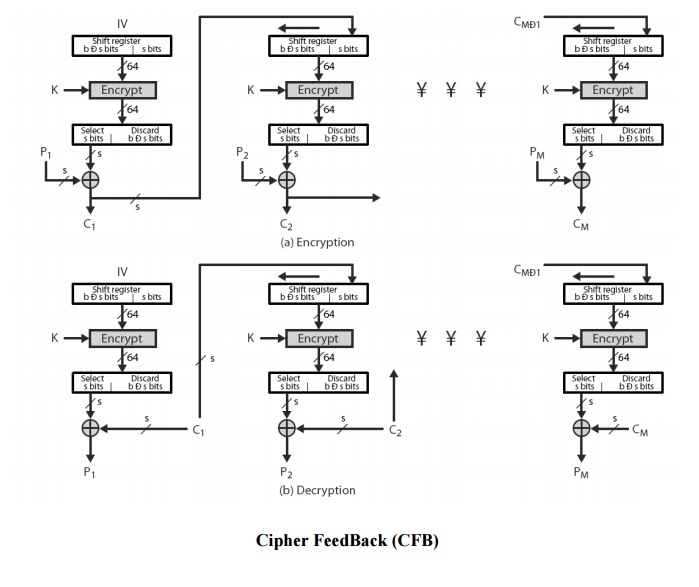
4 Cipher FeedBack (CFB)
message
is treated as a stream of bits
added to
the output of the block cipher
result is
feed back for next stage (hence name)
standard
allows any number of bit (1,8, 64 or 128 etc) to be feed back
ü denoted CFB-1, CFB-8, CFB-64, CFB-128 etc
most
efficient to use all bits in block (64 or 128)
Ci = Pi XOR
DESK1(Ci-1 )
C-1 = IV
uses:
stream data encryption, authentication
Advantages and Limitations of CFB
appropriate
when data arrives in bits/bytes
most
common stream mode
limitation
is need to stall while do block encryption after every n-bits
note that
the block cipher is used in encryption
mode at both ends
errors
propogate for several blocks after the error
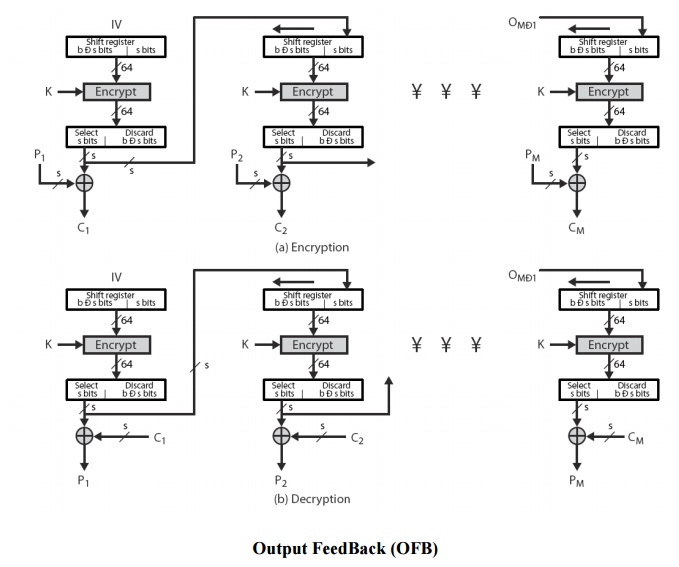
5 Output FeedBack (OFB)
message
is treated as a stream of bits
output of
cipher is added to message
output is
then feed back (hence name)
feedback
is independent of message
can be
computed in advance
Ci = Pi XOR
Oi
Oi = DESK1(Oi-1)
O-1 = IV
uses:
stream encryption on noisy channels
Advantages and Limitations of OFB
bit
errors do not propagate
more
vulnerable to message stream modification
a
variation of a Vernam cipher
hence
must never reuse the same sequence
(key+IV)
sender
& receiver must remain in sync
originally
specified with m-bit feedback
subsequent
research has shown that only full block
feedback (ie CFB-64 or CFB-128) should ever be used
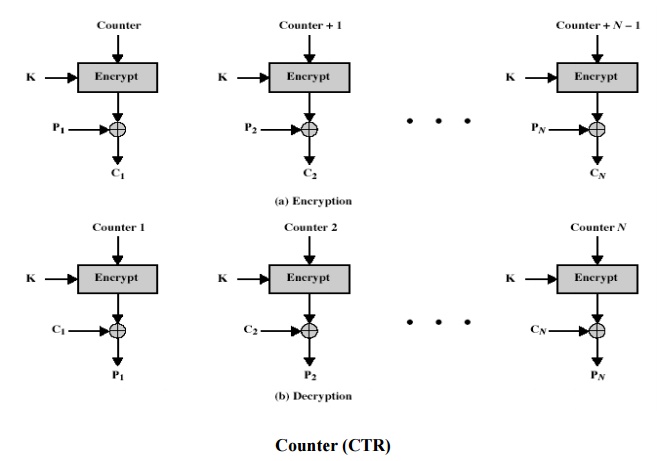
6 Counter (CTR)
a “new”
mode, though proposed early on
similar
to OFB but encrypts counter value rather than any feedback value
must have
a different key & counter value for every plaintext block (never reused)
Ci = Pi XOR
Oi
Oi = DESK1(i)
uses:
high-speed network encryptions
Advantages and Limitations of CTR
efficiency
can do parallel encryptions in h/w or s/w
can preprocess in advance of need
good for bursty high speed links
random access to encrypted data blocks
provable security (good as other modes)
but must ensure never reuse key/counter values, otherwise could break
(cf OFB)
Related Topics