Chapter: Cryptography and Network Security
Public-Key Management
Public-Key Management
This
whole business of protecting public keys from tampering is the single most
difficult problem in practical public key applications. PGP provides a
structure for solving this problem, with several suggested options that may be
used.
1. Approaches to Public-Key Management
The
essence of the problem is this: User A must build up a public-key ring
containing the public keys of other users to interoperate with them using PGP.
Suppose that A's key ring contains a public key attributed to B but that the
key is, in fact, owned by C. This could happen if, for example, A got the key
from a bulletin board system (BBS) that was used by B to post the public key
but that has been compromised by C. The result is that two threats now exist.
First, C can send messages to A and forge B's signature, so that A will accept
the message as coming from B. Second, any encrypted message from A to B can be
read by C.
A number
of approaches are possible for minimizing the risk that a user's public-key
ring contains false public keys. Suppose that A wishes to obtain a reliable
public key for B. The following are some approaches that could be used:
o
Physically get the key from B. B could store her
public key (PUb) on a floppy disk and hand it to A..
o
Verify a key by telephone. If A can recognize B on
the phone, A could call B and ask her to dictate the key, in radix-64 format,
over the phone.
o
Obtain B's public key from a mutual trusted
individual D. For this purpose, the introducer, D, creates a signed
certificate. The certificate includes B's public key, the time of creation of
the key, and a validity period for the key.
o
Obtain B's public key from a trusted certifying
authority. Again, a public key certificate is created and signed by the
authority. A could then access the authority, providing a user name and
receiving a signed certificate.
For cases
3 and 4, A would already have to have a copy of the introducer's public key and
trust that this key is valid. Ultimately, it is up to A to assign a level of
trust to anyone who is to act as an introducer.
2. The Use of Trust
Although
PGP does not include any specification for establishing certifying authorities
or for establishing trust, it does provide a convenient means of using trust,
associating trust with public keys, and exploiting trust information.
The basic
structure is as follows. Each entry in the public-key ring is a public-key
certificate.
Associated
with each such entry is a key legitimacy field that indicates the extent to
which PGP will trust that this is a valid public key for this user; the higher
the level of trust, the stronger is the binding of this user ID to this key.
This field is computed by PGP.
Also
associated with the entry are zero or more signatures that the key ring owner
has collected that sign this certificate. In turn, each signature has associated
with it a signature trust field that indicates the degree to which this PGP
user trusts the signer to certify public keys.
The key
legitimacy field is derived from the collection of signature trust fields in
the entry.
Finally,
each entry defines a public key associated with a particular owner, and an
owner trust field is included that indicates the degree to which this public
key is trusted to sign other public-key certificates; this level of trust is
assigned by the user.
The three
fields mentioned in the previous paragraph are each contained in a structure
referred to as a trust flag byte.
Suppose
that we are dealing with the public-key ring of user A. We can describe the
operation of the trust processing as follows:
o
When A inserts a new public key on the public-key
ring, PGP must assign a value to the trust flag that is associated with the
owner of this public key. If the owner is A, and therefore this public key also
appears in the private-key ring, then a value of ultimate trust is automatically
assigned to the trust field. Otherwise, PGP asks A for his assessment of the
trust to be assigned to the owner of this key, and A must enter the desired
level. The user can specify that this owner is unknown, untrusted, marginally
trusted, or completely trusted.
o
When the new public key is entered, one or more
signatures may be attached to it. More signatures may be added later. When a
signature is inserted into the entry, PGP searches the public-key ring to see
if the author of this signature is among the known public-key owners. If so,
the OWNERTRUST value for this owner is assigned to the SIGTRUST field for this
signature. If not, an unknown user value is assigned.
o
The value of the key legitimacy field is calculated
on the basis of the signature trust fields present in this entry. If at least
one signature has a signature trust value of ultimate, then the key legitimacy
value is set to complete.
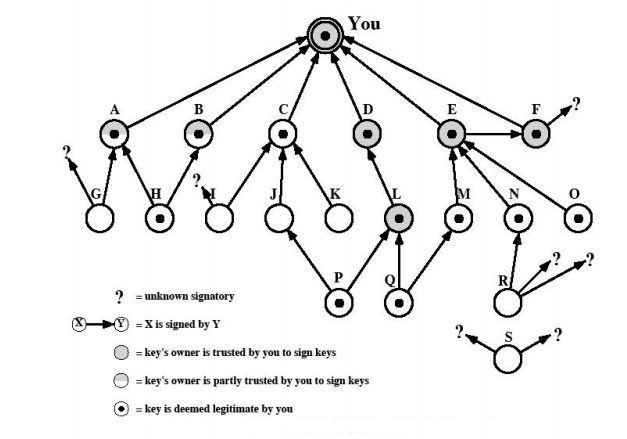
The node
labeled "You" refers to the entry in the public-key ring
corresponding to this user. This key is legitimate and the OWNERTRUST value is
ultimate trust. Each other node in the key ring has an OWNERTRUST value of
undefined unless some other value is assigned by the user. In this example,
this user has specified that it always trusts the following users to sign other
keys: D, E, F, L. This user partially trusts users A and B to sign other keys.
So the
shading, or lack thereof, of the nodes indicates the level of trust assigned by
this user. The tree structure indicates which keys have been signed by which
other users. If a key is signed by a user whose key is also in this key ring,
the arrow joins the signed key to the signatory. If the key is signed by a user
whose key is not present in this key ring, the arrow joins the signed key to a
question mark, indicating that the signatory is unknown to this user.
Related Topics