Chapter: Cryptography and Network Security
Electronic Mail Security
ELECTRONIC MAIL SECURITY
1 PRETTY GOOD PRIVACY (PGP)
PGP provides the confidentiality and authentication
service that can be used for electronic mail and file storage applications. The steps
involved in PGP are:
o
Select the best available cryptographic algorithms
as building blocks.
o
Integrate these algorithms into a general purpose
application that is independent of operating system and processor and that is
based on a small set of easy-to-use commands.
o
Make the package and its documentation, including
the source code, freely available via the internet, bulletin boards and
commercial networks.
o
Enter into an agreement with a company to provide a
fully compatible, low cost commercial version of PGP.
PGP has grown explosively and is now widely used. A
number of reasons can be cited for this growth.
o
It is available free worldwide in versions that run
on a variety of platform.
o
It is based on algorithms that have survived extensive
public review and are considered extremely secure.
o
e.g., RSA, DSS and Diffie Hellman for public key
encryption CAST-128, IDEA and 3DES for conventional encryption SHA-1 for hash
coding.
o
It has a wide range of applicability.
o
It was not developed by, nor it is controlled by,
any governmental or standards organization.
Operational description
The
actual operation of PGP consists of five services: authentication,
confidentiality, compression, e-mail compatibility and segmentation.
1. Authentication
The
sequence for authentication is as follows:
§
The sender creates the message
§
SHA-1 is used to generate a 160-bit hash code of
the message
§
The hash code is encrypted with RSA using the
sender‟s private key and the result is prepended to the message
§
The receiver uses RSA with the sender‟s public key
to decrypt and recover the hash code.
·
The receiver generates a new hash code for the
message and compares it with the decrypted hash code. If the two match, the
message is accepted as authentic.
2. Confidentiality
Confidentiality
is provided by encrypting messages to be transmitted or to be stored locally as
files. In both cases, the conventional encryption algorithm CAST-128 may be
used. The 64-bit cipher feedback (CFB) mode is used.
In PGP,
each conventional key is used only once. That is, a new key is generated as a
random 128-bit number for each message. Thus although this is referred to as a session key, it is in reality a one time key. To protect the key, it is
encrypted with the receiver‟s public key.
The
sequence for confidentiality is as follows:
o
The sender generates a message and a random 128-bit
number to be used as a session key for this message only.
o
The message is encrypted using CAST-128 with the
session key.
o
The session key is encrypted with RSA, using the
receiver‟s public key and is prepended to the message.
o
The receiver uses RSA with its private key to
decrypt and recover the session key.
o
The session key is used to decrypt the message.
Confidentiality and authentication
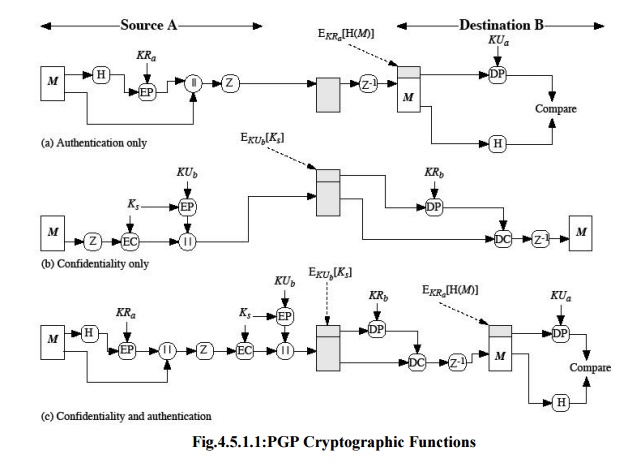
Here both
services may be used for the same message. First, a signature is generated for
the plaintext message and prepended to the message. Then the plaintext plus the
signature is encrypted using CAST-128 and the session key is encrypted using
RSA.
3. Compression
As a
default, PGP compresses the message after applying the signature but before
encryption. This has the benefit of saving space for both e-mail transmission
and for file storage.
The
signature is generated before compression for two reasons:
o
It is preferable to sign an uncompressed message so
that one can store only the uncompressed message together with the signature
for future verification. If one signed a compressed document, then it would be
necessary either to store a compressed version of the message for later
verification or to recompress the message when verification is required.
o
Even if one were willing to generate dynamically a
recompressed message fro verification, PGP‟s compression algorithm presents a
difficulty. The algorithm is not deterministic; various implementations of the
algorithm achieve different tradeoffs in running speed versus compression ratio
and as a result, produce different compression forms.
Message
encryption is applied after compression to strengthen cryptographic security.
Because the compressed message has less redundancy than the original plaintext,
cryptanalysis is more difficult. The compression algorithm used is ZIP.
4. e-mail compatibility
Many
electronic mail systems only permit the use of blocks consisting of ASCII
texts. To accommodate this restriction, PGP provides the service of
converting
the raw 8-bit binary stream to a stream of printable ASCII characters. The scheme
used for this purpose is radix-64
conversion. Each group of three octets of binary data is mapped into four
ASCII characters.
e.g.,
consider the 24-bit (3 octets) raw text sequence 00100011 01011100 10010001, we
can express this input in block of 6-bits to produce 4 ASCII characters.

5. Segmentation and reassembly
E-mail
facilities often are restricted to a maximum length. E.g., many of the
facilities accessible through the internet impose a maximum length of 50,000
octets. Any message longer than that must be broken up into smaller segments,
each of which is mailed separately.
To
accommodate this restriction, PGP automatically subdivides a message that is
too large into segments that are small enough to send via e-mail. The
segmentation is done after all the other processing, including the radix-64
conversion. At the receiving end, PGP must strip off all e-mail headers and
reassemble the entire original block before performing the other steps.
2. PGP Operation Summary:
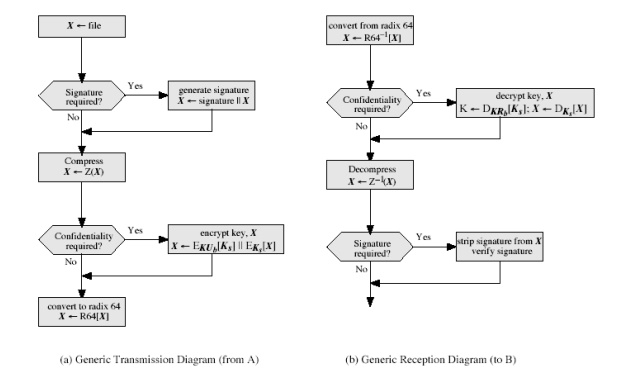
Cryptographic keys and key rings
Three
separate requirements can be identified with respect to these keys:
A means
of generating unpredictable session keys is needed.
It must
allow a user to have multiple public key/private key pairs.
Each PGP
entity must maintain a file of its own public/private key pairs as well as a
file of public keys of correspondents.
We now
examine each of the requirements in turn.
1. Session key generation
Each
session key is associated with a single message and is used only for the
purpose of encryption and decryption of that message. Random 128-bit numbers
are generated using CAST-128 itself. The input to the random number generator
consists of a 128-bit key and two 64-bit blocks that are treated as plaintext
to be encrypted. Using cipher feedback mode, the CAST-128 produces two 64-bit
cipher text blocks, which are concatenated to form the 128-bit session key. The
plaintext input to CAST-128 is itself derived from a stream of 128-bit
randomized numbers. These numbers are based on the keystroke input from the
user.
2. Key identifiers
If
multiple public/private key pair are used, then how does the recipient know
which of the public keys was used to encrypt the session key? One simple
solution would be to transmit the public key with the message but, it is
unnecessary wasteful of space. Another solution would be to associate an
identifier with each public key that is unique at least within each user.
The
solution adopted by PGP is to assign a key ID to each public key that is, with
very high probability, unique within a user ID. The key ID associated with each
public key consists
of its
least significant 64 bits. i.e., the key ID of public key KUa is
(KUa mod 264).
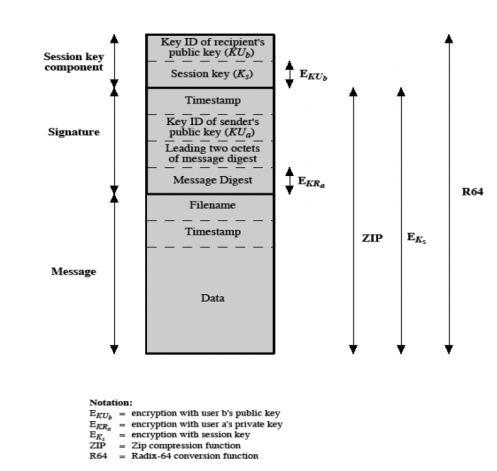
message consists of three components.
Message component – includes actual data to be
transmitted, as well as the filename and a
timestamp that specifies the time of creation.
Signature component – includes the following
o
Timestamp – time at which the signature was made.
o
o Message digest – hash code.
o
Two octets of message digest – to enable the
recipient to determine if the correct public key was used to decrypt the message.
o
Key ID of sender‟s public key – identifies the public key
Session key component – includes session key and the
identifier of the recipient public key.
3. Key rings
PGP
provides a pair of data structures at each node, one to store the
public/private key pair owned by that node and one to store the public keys of
the other users known at that node. These data structures are referred to as
private key ring and public key ring.
3. The general structures of the
private and public key rings are shown below:
Timestamp – the date/time when this entry was made.
Key ID – the least significant bits of the public key.
Public key – public key portion of the pair.
Private key – private key portion of the pair.
User ID – the owner of the key.
Key legitimacy field – indicates the extent to which PGP will
trust that this is a valid public key for this user.
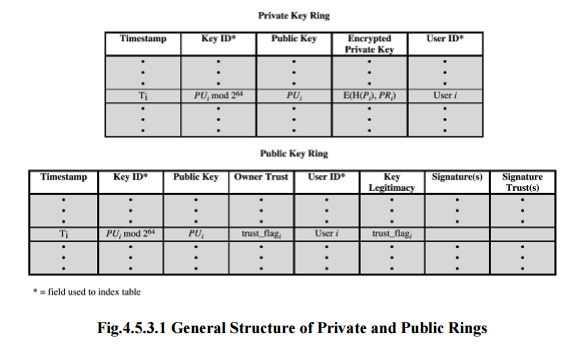
Fig.4.5.3.1 General Structure of
Private and Public Rings
Signature trust field – indicates
the degree to which this PGP user trusts the signer to certify
public
key.
Owner trust field – indicates the degree to which this
public key is trusted to sign other public key
certificates.
PGP message generation
First
consider message transmission and assume that the message is to be both signed
and encrypted. The sending PGP entity performs the following steps:
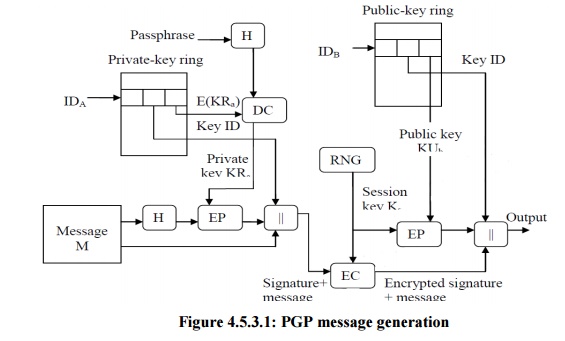
1. Signing the message
o
PGP retrieves the sender‟s private key from the
private key ring using user ID as an index.
o
If user ID was not provided, the first private key
from the ring is retrieved.
o
PGP prompts the user for the passpharse (password)
to recover the unencrypted private key.
o
The signature component of the message is
constructed.
2. Encrypting the message
o
PGP generates a session key and encrypts the
message.
o
PGP retrieves the recipient‟s public key from the
public key ring using user ID as index.
o
The session key component of the message is
constructed.
The
receiving PGP entity performs the following steps
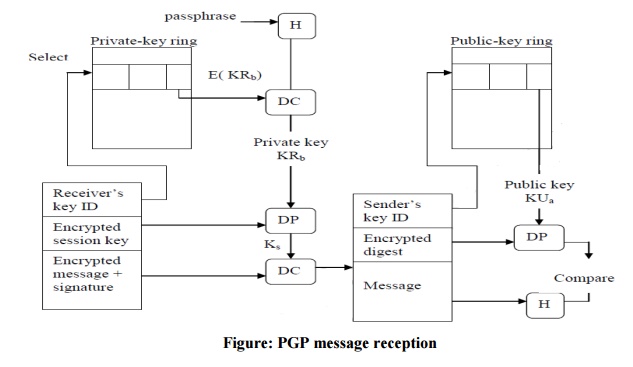
1. Decrypting the message
o
PGP retrieves the receiver‟s private key from the
private key ring, using the key ID field in the session key component of the
message as an index.
o
PGP prompts the user for the passpharse (password)
to recover the unencrypted private key.
o
PGP then recovers the session key and decrypts the
message.
2. Authenticating the message
o
PGP retrieves the sender‟s public key from the
public key ring, using the key ID field in the signature key component of the
message as an index.
o
PGP recovers the transmitted message digest.
o
PGP computes the message digest for the received
message and compares it to the transmitted message digest to authenticate.
Related Topics