Chapter: Cryptography and Network Security
Authentication Procedures
Authentication Procedures
X.509
includes three alternative authentication procedures:
o
One-Way
Authentication
o
Two-Way
Authentication
o
Three-Way
Authentication
o
all use public-key signatures
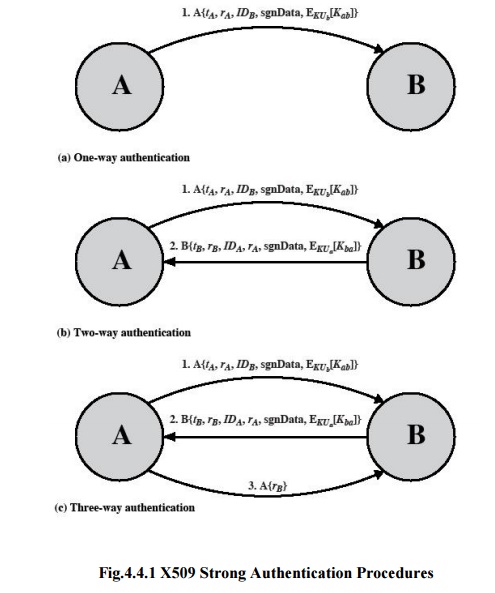
One-Way Authentication
o
1 message ( A->B) used to establish
o
the identity of A and that message is from A
o
message was intended for B
o
integrity & originality of message
o
message must include timestamp, nonce, B's identity
and is signed by A
Two-Way Authentication
1. 2
messages (A->B, B->A) which also establishes in addition:
a. the
identity of B and that reply is from B
b. that
reply is intended for A
c. integrity
& originality of reply
2. reply
includes original nonce from A, also timestamp and nonce from B
Three-Way Authentication
o
3 messages (A->B, B->A, A->B) which
enables above authentication without synchronized clocks
o
has reply from A back to B containing signed copy
of nonce from B
o
means that timestamps need not be checked or relied
upo
Related Topics