Chapter: Security in Computing : Security in Networks
Traffic Flow Security
Traffic Flow Security
So far, we have looked at
controls that cover the most common network threats: cryptography for
eavesdropping, authentication methods for impersonation, intrusion detection
systems for attacks in progress, architecture for structural flaws. Earlier in
this chapter, we listed threats, including a threat of traffic flow inference.
If the attacker can detect an exceptional volume of traffic between two points,
the attacker may infer the location of an event about to occur.
The countermeasure to traffic
flow threats is to disguise the traffic flow. One way to disguise traffic flow,
albeit costly and perhaps crude, is to ensure a steady volume of traffic
between two points. If traffic between A and B is encrypted so that the
attacker can detect only the number of packets flowing, A and B can agree to
pass recognizable (to them) but meaningless encrypted traffic. When A has much
to communicate to B, there will be few meaningless packets; when communication
is light, A will pad the traffic stream with many spurious packets.
A more sophisticated approach
to traffic flow security is called onion
routing [SYV97]. Consider a message
that is covered in multiple layers, like the layers of an onion. A wants to
send a message to B but doesn't want anyone in or intercepting traffic on the
network to know A is communicating with B. So A takes the message to B, wraps
it in a package for D to send to B. Then, A wraps that package in another
package for C to send to D. Finally, A sends this package to C. This process is
shown in Figure 7-33. The internal
wrappings are all encrypted under a key appropriate for the intermediate
recipient.
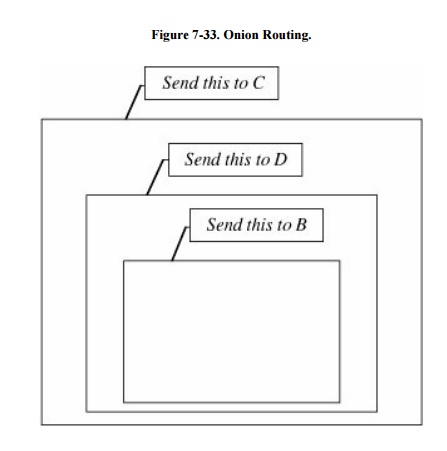
Receiving the package, C
knows it came from A, although C does not know if A is the originator or an
intermediate point. C then unwraps the outer layer and sees it should be sent
to D. At this point, C cannot know if D is the final recipient or merely an
intermediary. C sends the message to D, who unwraps the next layer. D knows
neither where the package originally came from nor where its final destination
is. D forwards the package to B, its ultimate recipient.
With this scheme, any
intermediate recipientsthose other than the original sender and ultimate
receiverknow neither where the package originated nor where it will end up.
This scheme provides confidentiality of content, source, destination, and
routing.
Controls Review
At the end of our earlier
discussion on threats in networks, we listed in Table
7-4 many of the vulnerabilities present in networks. Now that we
have surveyed the controls available for networks, we repeat that table as Table 7-7, adding a column to show the controls
that can protect against each vulnerability. (Note: This table is not
exhaustive; other controls can be used against some of the vulnerabilities.)
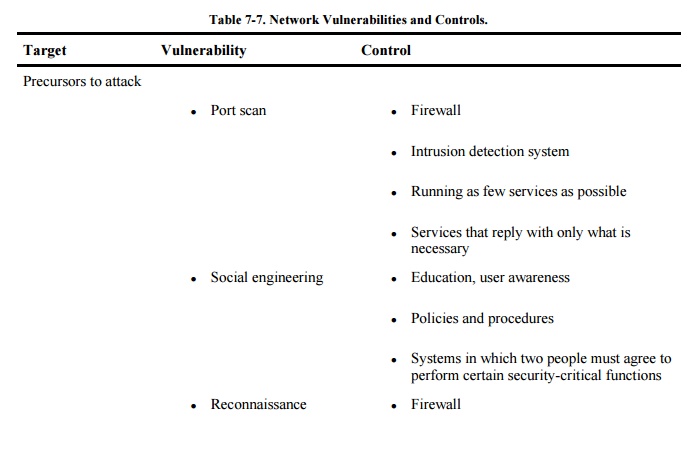



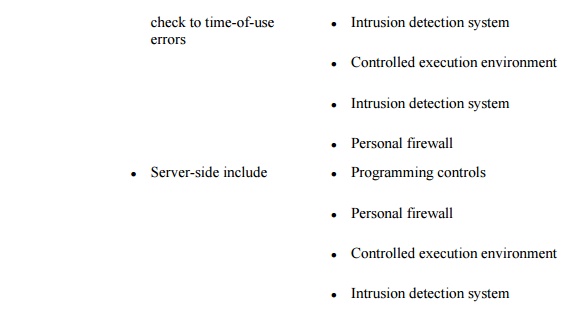
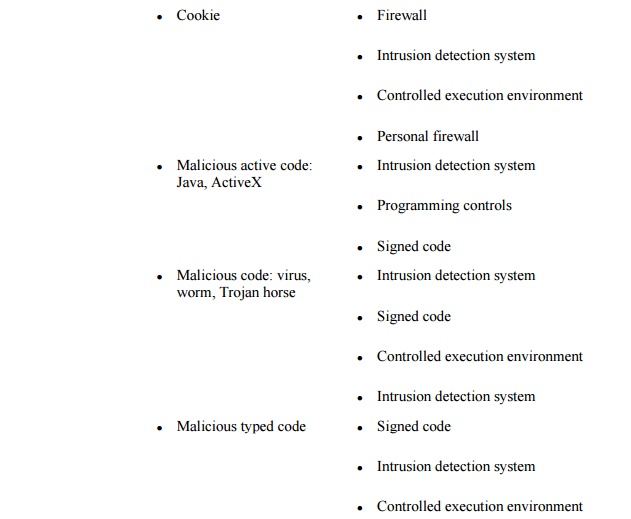
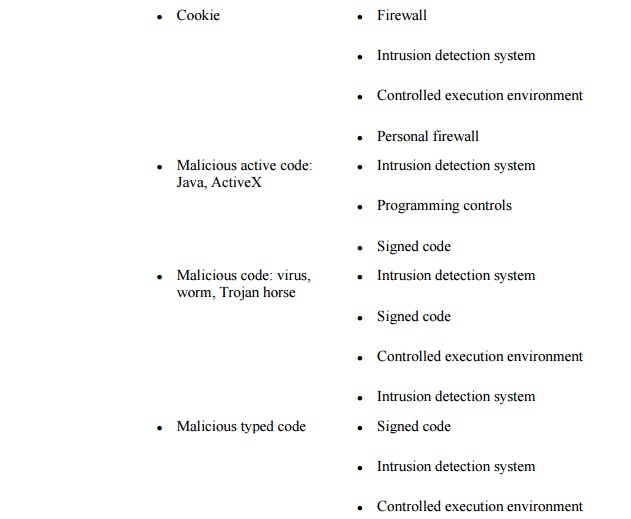


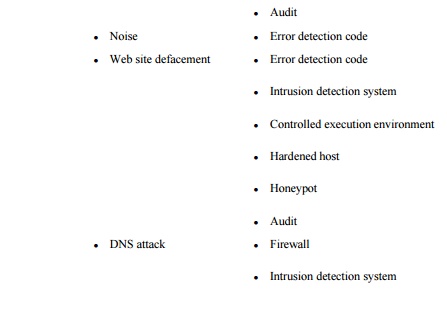

As Table 7-7 shows, network security designers have many
successful tools at their disposal. Some of these, such as encryption, access
control and authentication, and programming controls, are familiar from
previous chapters in this book.
But three are specific to
networked settings, and we explore them now in greater depth: firewalls,
intrusion detection systems, and encrypted e-mail. Firewalls control traffic
flow into and out of protected network segments. Intrusion detection systems
monitor traffic within a network to spot potential attacks under way or about
to occur. And encrypted email uses encryption to enhance the confidentiality or
authenticity of e-mail messages.
Related Topics