Chapter: Security in Computing : Designing Trusted Operating Systems
Separation/Isolation
Separation/Isolation
Recall from Chapter 4 that Rushby and Randell [RUS83] list four ways to separate one process
from others: physical, temporal, cryptographic, and logical separation. With physical separation, two different
processes use two different hardware facilities. For example, sensitive
computation may be performed on a reserved computing system; nonsensitive tasks
are run on a public system. Hardware separation offers several attractive
features, including support for multiple independent threads of execution,
memory protection, mediation of I/O, and at least three different degrees of
execution privilege. Temporal separation
occurs when different processes are run at different times. For instance, some
military systems run nonsensitive jobs between 8:00 a.m. and noon, with
sensitive computation only from noon to 5:00 p.m. Encryption is used for cryptographic separation, so two
different processes can be run at the same time because unauthorized users
cannot access sensitive data in a readable form. Logical separation, also called isolation, is provided when a
process such as a reference monitor separates one user's objects from those of
another user. Secure computing systems have been built with each of these forms
of separation.
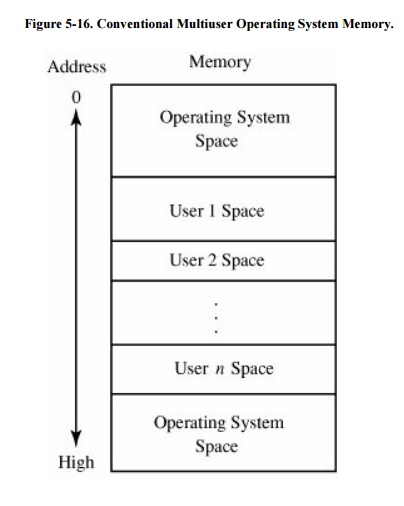
Multiprogramming operating systems should
isolate each user from all others, allowing only carefully controlled
interactions between the users. Most operating systems are designed to provide
a single environment for all. In other words, one copy of the operating system
is available for use by many users, as shown in Figure
5-16. The operating system is often separated into two distinct
pieces, located at the highest and lowest addresses of memory.
Related Topics