Chapter: Security in Computing : Designing Trusted Operating Systems
Security Features of Ordinary Operating Systems
Security Features of Ordinary Operating Systems
A multiprogramming operating system performs several functions
that relate to security. To see how, examine Figure
5-10, which illustrates how an operating
system interacts with users, provides services, and allocates resources.
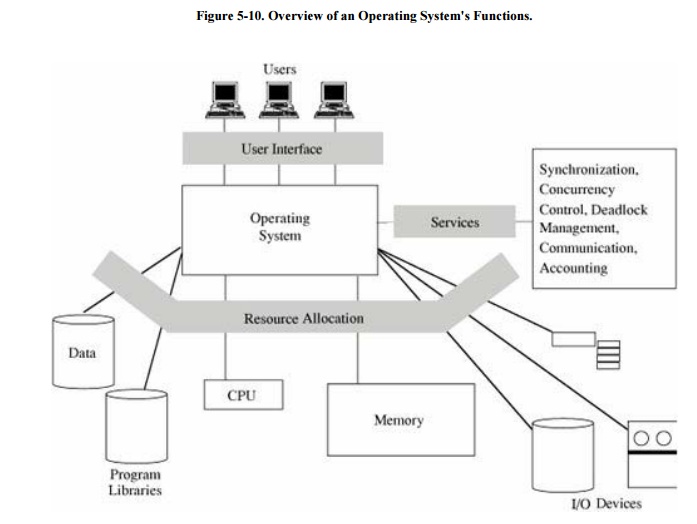
We can see that the system
addresses several particular functions that involve computer security:
User authentication. The operating system must identify each user
who requests access and must ascertain that the user is actually who he or she purports to be. The most
common authentication mechanism is password comparison.
Memory protection. Each user's program must run in a portion of
memory protected against unauthorized accesses. The protection will certainly prevent outsiders'
accesses, and it may also control a user's own access to restricted parts of
the program space. Differential security, such as read, write, and execute, may
be applied to parts of a user's memory space. Memory protection is usually
performed by hardware mechanisms, such as paging or segmentation.
File and I/O device access
control. The operating system must protect user and system files from access by
unauthorized users. Similarly, I/O device use must be protected. Data
protection is usually achieved by table lookup, as with an access control
matrix.
Allocation and access control
to general objects. Users need general objects, such as constructs to permit
concurrency and allow synchronization. However, access to these objects must be
controlled so that one user does not have a negative effect on other users.
Again, table lookup is the common means by which this protection is provided.
Enforced sharing. Resources should be made
available to users as appropriate. Sharing brings about the need to guarantee
integrity and consistency. Table
lookup, combined with integrity controls such as monitors or transaction
processors, is often used to support controlled sharing.
Guaranteed fair service. All users expect CPU usage
and other service to be provided so that no user is indefinitely starved from
receiving service. Hardware clocks combine with scheduling disciplines to
provide fairness. Hardware facilities and data tables combine to provide
control.
Interprocess communication and synchronization. Executing processes
sometimes need to communicate with other processes or to synchronize their accesses to shared resources. Operating systems
provide these services by acting as a bridge between processes, responding to
process requests for asynchronous communication with other processes or synchronization.
Interprocess communication is mediated by access control tables.
Protected operating system
protection data. The operating system must maintain data by which it can
enforce security. Obviously if these data are not protected against unauthorized
access (read, modify, and delete), the operating system cannot provide
enforcement. Various techniques, including encryption, hardware control, and
isolation, support isolation of operating system protection data.
Related Topics