Chapter: Cryptography and Network Security
Network Virus Countermeasures
VIRUS COUNTERMEASURES
Antivirus Approaches
The ideal
solution to the threat of viruses is prevention: The next best approach is to
be able to do the following:
·
Detection:
Once the
infection has occurred, determine that it has occurred and locate the virus.
·
Identification: Once
detection has been achieved, identify the specific virus that has infected a program.
·
Removal: Once
the specific virus has been identified, remove all traces of the virus from the infected program and restore it to
its original state. Remove the virus from all infected systems so that the
disease cannot spread further.
If
detection succeeds but either identification or removal is not possible, then
the alternative is to discard the infected program and reload a clean backup version.
There are
four generations of antivirus software:
·
First generation: simple scanners
·
Second generation: heuristic scanners
·
Third generation: activity traps
·
Fourth generation: full-featured protection
A first-generation scanner requires
a virus signature to identify a virus.. Such signature-specific scanners are limited to the detection
of known viruses. Another type of first-generation scanner maintains a record
of the length of programs and looks for changes in length.
A second-generation scanner does not
rely on a specific signature. Rather, the scanner uses heuristic rules to search for probable virus infection. One class
of such scanners looks for fragments of code that are often associated with
viruses.
Another
second-generation approach is integrity checking. A checksum can be appended to
each program. If a virus infects the program without changing the checksum,
then an integrity check will catch the change. To counter a virus that is
sophisticated enough to change the checksum when it infects a program, an
encrypted hash function can be used. The encryption key is stored separately
from the program so that the virus cannot generate a new hash code and encrypt
that. By using a hash function rather than a simpler checksum, the virus is
prevented from adjusting the program to produce the same hash code as before.
Third-generation programs are
memory-resident programs that identify a virus by its actions rather than its structure in an
infected program. Such programs have the advantage that it is not necessary to
develop signatures and heuristics for a wide array of viruses. Rather, it is
necessary only to identify the small set of actions that indicate an infection
is being attempted and then to intervene.
Fourth-generation products are
packages consisting of a variety of antivirus techniques used in conjunction. These include scanning
and activity trap components. In addition, such a package includes access
control capability, which limits the ability of viruses to penetrate a system
and then limits the ability of a virus to update files in order to pass on the
infection.
The arms
race continues. With fourth-generation packages, a more comprehensive defense
strategy is employed, broadening the scope of defense to more general-purpose
computer security measures.
Advanced Antivirus Techniques
More
sophisticated antivirus approaches and products continue to appear. In this
subsection, we highlight two of the most important.
Generic
Decryption
Generic
decryption (GD) technology enables the antivirus program to easily detect even
the most complex polymorphic viruses, while maintaining fast scanning speeds .
In order to detect such a structure, executable files are run through a GD
scanner, which contains the following elements:
·
CPU emulator:
A
software-based virtual computer. Instructions in an executable file are interpreted by the emulator rather
than executed on the underlying processor. The emulator includes software
versions of all registers and other processor hardware, so that the underlying
processor is unaffected by programs interpreted on the emulator.
·
Virus
signature scanner: A module that scans the target code looking for
known virus signatures.
·
Emulation
control module: Controls the execution of the target code.
Digital
Immune System
The
digital immune system is a comprehensive approach to virus protection developed
by IBM]. The motivation for this development has been the rising threat of
Internet-based virus propagation.Two major trends in Internet technology have
had an increasing impact on the rate of virus propagation in recent years:
Integrated
mail systems: Systems such as Lotus Notes and Microsoft Outlook make it very
simple to send anything to anyone and to work with objects that are received.
Mobile-program
systems: Capabilities such as Java and ActiveX allow programs to move on their
own from one system to another.
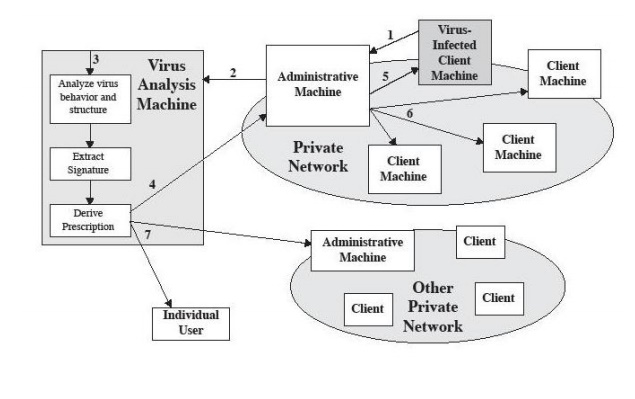
·
A monitoring program on each PC uses a variety of
heuristics based on system behavior, suspicious changes to programs, or family
signature to infer that a virus may be present. The monitoring program forwards
a copy of any program thought to be infected to an administrative machine
within the organization.
·
The administrative machine encrypts the sample and
sends it to a central virus analysis machine.
·
This machine creates an environment in which the
infected program can be safely run for analysis. Techniques used for this
purpose include emulation, or the creation of a protected environment within
which the suspect program can be executed and monitored. The virus analysis
machine then produces a prescription for identifying and removing the virus.
·
The resulting prescription is sent back to the
administrative machine.
·
The administrative machine forwards the
prescription to the infected client.
·
The prescription is also forwarded to other clients
in the organization.
·
Subscribers around the world receive regular
antivirus updates that protect them from the new virus.
The
success of the digital immune system depends on the ability of the virus
analysis machine to detect new and innovative virus strains. By constantly
analyzing and monitoring the viruses found in the wild, it should be possible
to continually update the digital immune software to keep up with the threat.
Behavior-Blocking Software
Unlike
heuristics or fingerprint-based scanners, behavior-blocking software integrates
with the operating system of a host computer and monitors program behavior in
real-time for malicious actions. Monitored behaviors can include the following:
·
Attempts to open, view, delete, and/or modify
files;
·
Attempts to format disk drives and other unrecoverable
disk operations;
·
Modifications to the logic of executable files or
macros;
·
Modification of critical system settings, such as
start-up settings;
·
Scripting of e-mail and instant messaging clients
to send executable content; and
·
Initiation of network communications.
If the
behavior blocker detects that a program is initiating would-be malicious
behaviors as it runs, it can block these behaviors in real-time and/or
terminate the offending software. This gives it a fundamental advantage over
such established antivirus detection techniques as fingerprinting or
heuristics.
Related Topics