Chapter: Computer Networks
Application layer
APPLICATION LAYER
1. DOMAIN NAME SYSTEM (DNS)
There are 3 components:
Name Space:
Specifications
for a structured name space and data associated with the names
Resolvers:
Client
programs that extract information from Name Servers.
Name Servers:
Server programs which hold information about the structure and the
names.
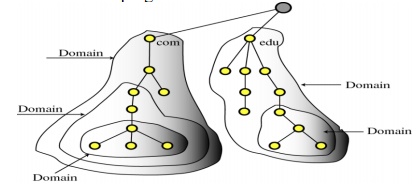
Resolvers
A
Resolver maps a name to an address and vice versa.
Iterative Resolution
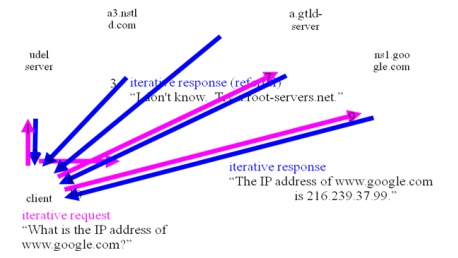
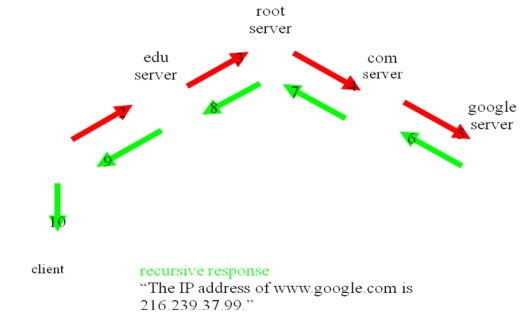
Recursive
Resolution
2. E- MAIL
┬Ę
What is an Email ŌĆō an electronic message
transmitted over a network from one user to another.
┬Ę
Can be as simple as a few lines of text, or include
attachments such as pictures or documents.
┬Ę
Email made up 75% of network traffic soon after the
introduction of the internet.
┬Ę
The Header
Who sent
the email.
To whom
the mail is sent.
When the
email was sent.
The email
subject.
The size
of the email.
┬Ę
The Body
Contains
the message.
May also
contain an attachment.
┬Ę
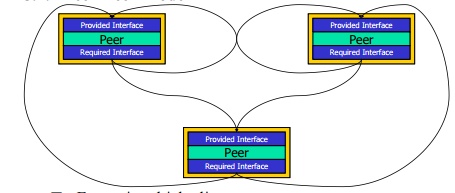
Attachments Different Architectural Models exist
for constructing computer systems.
┬Ę
Some models include:
┬Ę
Peer-Peer
┬Ę
Pipe and Filter
┬Ę
Implicit Invocation
┬Ę
Client-Server
If not embedded within the body, attachments are sent along with the
email. How Email Works
2.1
Peer-Peer Model
Forms in
which clients appear:
┬Ę
Application based - these are installed onto userŌĆÖs
machines and include Microsoft
Outlook and the freely available Outlook Express and Eudora.
┬Ę
Web based - these appear in a web browserŌĆÖs window
and include Hotmail, Yahoo and
Outlook web client.
Clients
vary greatly in functionality, but all provide a basic level of functionality
that assists the user.
Basic
functions include:
┬Ę
Ability to create new emails.
┬Ę
Display and store received emails.
┬Ę
Hold address lists of contacts, a calendar, journal
and other extra functions that help organize the userŌĆÖs working day.
┬Ę
The client is also configured with the account
information and names or IP addresses of the email servers with which it will
be communicating.
An email
server is typically a combination of processes running on a server with a large
storage capacity ŌĆō a list of users and rules, and the capability to receive,
send and store emails and attachments.
These
servers are designed to operate without constant user intervention.
Should
process emails for months as sending, receiving and maintenance tasks are
carried out at scheduled times. The client only has to connect to the email
server when it sends and checks/receives new email.
Sometimes
it may be permanently connected to the server to allow access to shared address
books or calendar information ŌĆō this is typical of a LAN-based email server.
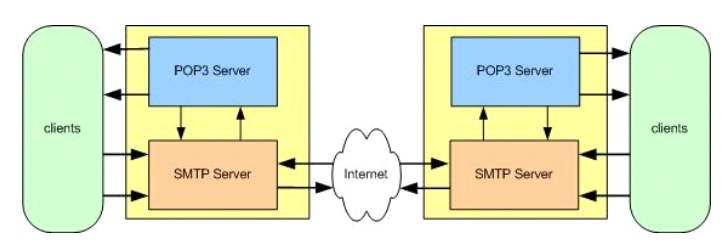
Most
email servers conduct email services by running two separate processes on the
same machine.
One
process is the POP3 (Post Office protocol 3) server, which holds emails in a
queue and delivers emails to the client when they are requested.
The other
is the SMTP (simple mail transfer protocol) server that receives outgoing
emails from clients and sends and receives email from other SMTP servers.
These two
processes are linked by an internal mail delivery mechanism that moves mail
between the POP3 and SMTP servers.
When the
client calls the email server to send or check for mail it connects to the
server on certain TCP/IP ports:
┬Ę
SMTP on port 25
┬Ę
POP3 on port 110.
3. WORLD WIDE WEB
┬Ę
Hypertext documents
Text
Links
┬Ę
Web
billions of documents
authored by millions of diverse people
edited by no one in particular
distributed over millions of computers, connected
by variety of media
┬Ę
Citation,
Hyperlinking
┬Ę
Ramayana, Mahabharata, Talmud
branching, non-linear discourse, nested commentary,
┬Ę
Dictionary, encyclopedia
self-contained networks of textual nodes
joined by referential links
Memex [Vannevar Bush]
stands for ŌĆ£memory extensionŌĆØ
photoelectrical-mechanical storage and computing
device
Aim: to create and help follow hyperlinks across
documents
Hypertext
Coined by Ted Nelson
Xanadu hypertext: system with
robust two-way hyperlinks, version management,
controversy management, annotation and copyright management.
Initiated at CERN (the European Organization for
Nuclear Research)
By Tim Berners-Lee
GUIs
Berners-Lee (1990)
Erwise and Viola(1992), Midas (1993)
Mosaic (1993)
a hypertext GUI for the X-window system
HTML: markup language for rendering hypertext
┬Ę
HTTP: hypertext transport protocol for sending HTML
and other data over the Internet
┬Ę
CERN HTTPD: server of hypertext documents
Hypertext
data
Semi-structured
or unstructured
┬Ę
No schema
Large
number of attributes
Purpose
of crawling and indexing
┬Ę
quick fetching of large number of Web pages into a
local repository
┬Ę
indexing based on keywords
┬Ę
Ordering responses to maximize userŌĆÖs chances of
the first few responses satisfying his information need.
Earliest
search engine: Lycos (Jan 1994)
Followed
byŌĆ”.
Alta
Vista (1995), HotBot and Inktomi, Excite
Yahoo!
directory
┬Ę
to locate useful Web sites
Efforts
for organizing knowledge into ontologies
┬Ę
Centralized: (Yahoo!)
┬Ę
Decentralized: About.COM and the Open Directory
3.2 Clustering and classification
Clustering
┬Ę
discover groups in the set of documents such that
documents within a group are more similar than documents across groups.
┬Ę
Subjective disagreements due to
different
similarity measures
Large
feature sets
Classification
┬Ę
For assisting human efforts in maintaining
taxonomies
┬Ę
E.g.: IBM's Lotus Notes text processing system
& Universal Database text extenders
3.3 Hyperlink analysis
Take
advantage of the structure of the Web graph.
┬Ę
Indicators of prestige of a page (E.g. citations)
┬Ę
HITS & PageRank
Bibliometry
┬Ę
bibliographic citation graph of academic papers
Topic
distillation
┬Ę
Adapting to idioms of Web authorship and linking
styles
Federations
of crawling and search services
┬Ę
each specializing in specific topical areas.
Goal-driven
Web resource discovery
┬Ę
language analysis does not scale to billions of
documents
┬Ę
counter by throwing more hardware
4. SNMP
┬Ę
SNMP is a tool (protocol) that allows for remote
and local management of items on the network including servers, workstations,
routers, switches and other managed devices.
┬Ę
Comprised of agents and managers
┬Ę
Agent - process running on each managed node
collecting information about the device it is running on.
┬Ę
Manager - process running on a management
workstation that requests information about devices on the network.
Advantages of using SNMP
Standardized
universally
supported
extendible
portable
allows
distributed management access
lightweight
protocol
SNMP is a
ŌĆ£client pullŌĆØ model
The
management system (client) ŌĆ£pullsŌĆØ data from the agent (server). SNMP is a
ŌĆ£server pushŌĆØ model
The agent
(server) ŌĆ£pushesŌĆØ out a trap message to a (client) management system
Ports & UDP
SNMP uses
User Datagram Protocol (UDP) as the transport mechanism for SNMP messages
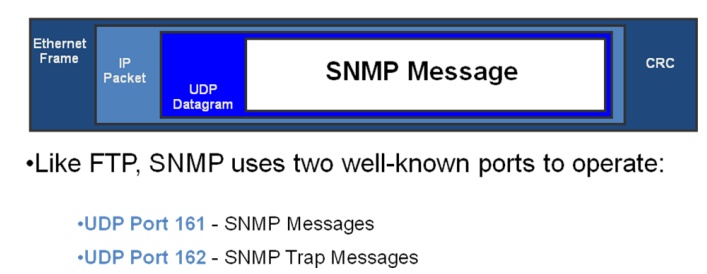
The Three Parts of SNMP
SNMP
network management is based on three parts:
SNMP
Protocol
Defines
format of messages exchanged by management systems and agents.
Specifies
the Get, GetNext, Set, and Trap operations Structure of Management Information
(SMI)
Rules
specifying the format used to define objects managed on the network that the
SNMP protocol accesses
Management
Information Base (MIB)
┬Ę
A map of the hierarchical order of all managed
objects and how they are accessed
Nodes
Items in
an SNMP Network are called nodes. There are different types of nodes.
┬Ę
Managed nodes
┬Ę
Management nodes
┬Ę
Typically a workstation running some network
management & monitoring software Nodes that are not manageable by SNMP
A node
may not support SNMP, but may be manageable by SNMP through a proxy agent
running on another machine
5. FTP
The File
Transfer Protocol (FTP) is a standard network protocol used to transfer computer files from one host to another host over a TCP-based
network, such as the Internet. FTP is
built on a client-server architecture
and uses separate control and data connections between the client and the
server. FTP users may authenticate themselves using a clear-text sign-in protocol, normally in the
form of a username and password, but can connect anonymously if the server is
configured to allow it. For secure transmission that protects the username and
password, and encrypts the content, FTP is often secured with SSL/TLS (FTPS). SSH File Transfer Protocol (SFTP) is
sometimes also used instead, but is technologically different.
The first
FTP client applications were command-line
applications developed before operating systems had graphical user
interfaces, and are still shipped with most Windows, Unix, and Linux operating systems. Many FTP
clients and automation utilities have since been developed for desktops,
servers, mobile devices, and hardware, and FTP has been incorporated into
productivity applications, such as Web page editors.
This
stands for File Transfer Protocol. This is a popular way to transfer files from
machine to machine across a network
Ways to connect to an FTP server
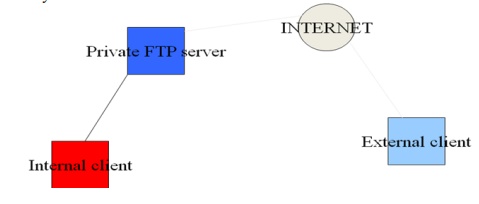
Private user-only site. Allows only system users to
connect via FTP and access their files.
ftp starts the program and connects to the specified site
cd stands for change directory. This command will
change to the spcified directory pwd
Print working directory(tells the user which
directory he/she is in) dir [filespec]
List
details about the file specification At the command prompt type :
ftp
papa.cdrom.com (this will start the ftp and connection to the site)
The
system will respond with the message
>connected
to sunsite.cnlab-switch.ch.
>220
warchive.cdrom.com.FTP server (Version wu-2.4.2(18)
>Thu
nov 26 09:30:12 MET 2001) ready.
>Name
(carchive.cdrom.com:usr):
Use ŌĆśdirŌĆÖ
to find the file:
Type:
dir l*
to get a
listing of all files which start with ŌĆślŌĆÖ. You should see:
-rw-rw-rŌĆō
1 2066 ftp-game 134868 Jun 30 2001 lan.txt
┬Ę
Because there is no ŌĆśdŌĆÖ at the far left, you know
that it is a file, not a directory.
┬Ę
The 134868 is the file size, it is 134,868 bytes
(approx. 134 Kb). It was last modified on the 30th of June 2001.
6. WEB SERVICES
n Web
services provide interoperability between various software applications running
on various platforms.
ŌĆ£vendor,
platform, and language agnosticŌĆØ
Web
services leverage open standards and protocols. Protocols and data formats are
text based where possible
┬Ę
Easy for developers to understand what is going on.
By
piggybacking on HTTP, web services can work through many common firewall
security measures without requiring changes to their filtering rules.
First the
client discovers the service.
┬Ę
More in next lecture!
Typically,
client then binds to the server.
┬Ę
By setting up TCP connection to the discovered
address .
┬Ę
But binding not always needed.
Next
build the SOAP request: (Marshaling)
Fill in
what service is needed, and the arguments. Send it to server side.
┬Ę
XML is the standard for encoding the data (but is
very verbose and results in HUGE overheads)
SOAP
router routes the request to the appropriate server(assuming more than one available
server)
Can do
load balancing here.
Server
unpacks the request, (Demarshaling) handles it, computes result.
Result
sent back in the reverse direction: from the server to the SOAP router back to
the client.
Marshalling Issues
Data
exchanged between client and server needs to be in a platform independent
format.
┬Ę
ŌĆ£EndianŌĆØness differ between machines.
┬Ę
Data alignment issue (16/32/64 bits)
┬Ę
Multiple floating point representations.
┬Ę
Pointers
┬Ę
(Have to support legacy systems too)
Discovery
This is
the problem of finding the ŌĆ£rightŌĆØ service
┬Ę
In our example, we saw one way to do it ŌĆō with a
URL
┬Ę
Web Services community favors what they call a URN:
Uniform Resource Name
But the
more general approach is to use an intermediary: a discovery service
Discovery
and naming
Many
settings, like the big data centers run by large corporations, have rather
standard structure. Can we automate discovery?
How to
debug if applications might sometimes bind to the wrong service?
Delegation
and migration are very tricky
Should a
system automatically launch services on demand?
┬Ę
Client has opinions
ŌĆ£I want
current map data for Disneyland showing line-lengths for the rides right nowŌĆØ
┬Ę
Service has opinions
Amazon.com
would like requests from Ithaca to go to the NJ-3 datacenter, and if possible,
to the same server instance within each clustered service
7. MULTIMEDIA APPLICATIONS
Multimedia
is a combination of text, graphic, sound, animation, and video that is
delivered interactively to the user by electronic or digitally manipulated
means.
There are
a number of fields where multimedia could be of use. Examples are:-
┬Ę
Business
┬Ę
Education
┬Ę
Entertainment
┬Ę
Home
Public
Places
Business
┬Ę
Use and Applications
Sales /
Marketing Presentation
Trade
show production
Staff
Training Application
Company
Kiosk
Education
┬Ę
Use and Applications
Courseware
/ Simulations
E-Learning
/ Distance Learning
Information
Searching
Entertainment
┬Ę
Use and Applications
Games
(Leisure / Educational)
Movies
Video on
Demand
Online
Home
┬Ę
Use and Applications
Television
Satellite
TV
SMS
services (chats, voting, reality TV
Public
Places
┬Ę
Use and Applications
Information
Kiosk
Smart
Cards, Security
Briefing
Products
Reference
Products
Database
Products
Education
and Training Products
Kiosk
Entertainment
and Games
Small,
straightforward, linear products used to present information quickly and
concisely.
Characteristic
of briefing product:
┬Ę
Short Development Cycle
┬Ę
Limited Number of Presentations
┬Ę
Usage of text to present information with limited
use of graphic, audio and video.
┬Ę
Have few navigational controls. (mouse click and
button press to move from one page to another)
Content
and the format are suitable for the audience and fulfill the purpose of the presentation.
Good
briefing presentation depends on:
┬Ę
The understanding of the presented subject.
┬Ę
Seamless integration of content.
┬Ę
Consistent layout
Example:
┬Ę
Corporate Presentation
┬Ę
Sales Presentation
┬Ę
Educational Lectures
Basic
classes of reference product:
┬Ę
Generalized Content (dictionary/encyclopedia)
Broad
treatment of content at a limited depth
┬Ę
Detailed Content
Focus on
specific area and provide extensive information
8. OVERLAY NETWORK
Multicast
improvement over point to point unicast
Embedding
of overlay in native network
Improved
throughput
ŌĆō BGP doesnŌĆÖt find shortest path
ŌĆō Triangle inequality
A logical
network built on top of a physical network
ŌĆō Overlay links are tunnels through the
underlying network
Many
logical networks may coexist at once
ŌĆō Over the same underlying network
ŌĆō And providing its own particular service
Nodes are
often end hosts
ŌĆō Acting as intermediate nodes that forward
traffic
ŌĆō Providing a service, such as access to files
Who
controls the nodes providing service?
ŌĆō The party providing the service (e.g.,
Akamai)
ŌĆō Distributed collection of end users (e.g.,
peer-to-peer)
Alternative
routing strategies
ŌĆō No application-level processing at the
overlay nodes
ŌĆō Packet-delivery service with new routing
strategies
Incremental
enhancements to IP
ŌĆō IPv6
ŌĆō Multicast
ŌĆō Mobility
ŌĆō Security
Revisiting
where a function belongs
ŌĆō End-system multicast: multicast distribution
by end hosts
Customized
path selection
ŌĆō Resilient Overlay Networks: robust packet
delivery
IP tunnel is a virtual point-to-point link
ŌĆō Illusion of a direct link between two
separated nodes
ŌĆō Encapsulation of the packet inside an IP
datagram
ŌĆō Node B sends a packet to node E
ŌĆō ŌĆ” containing another packet as the payload
Routing overlays
ŌĆō Experimental versions of IP (e.g., 6Bone)
ŌĆō Multicast (e.g., MBone and end-system
multicast)
ŌĆō Robust routing (e.g., Resilient Overlay
Networks)
Types of peer-to-peer networks
ŌĆō Directory-based (e.g., original Napster design)
ŌĆō Unstructured (e.g., Gnutella, Kazaa,
BitTorrent)
ŌĆō Structured (e.g., distributed hash tables)
Challenges in peer-to-peer
ŌĆō Legal
issues, free riding, fast response to queries, peers coming and going over
time, reliability, security, ŌĆ”
Related Topics