Chapter: Computer Networks : Fundamentals & Link Layer
Requirements of Computer Networks
REQUIREMENTS
·
Connectivity
·
Cost-Effective Resource Sharing
·
Support for Common Services
·
Performance
Requirements
differ according to the perspective:
1. Application programmer
List the
services that his or her application needs.
Example:
A guarantee that each message it sends will be delivered without error within a
certain amount of time.
2. Network designer
List the
properties of a cost-effective design.
Example:
The network resources efficiently utilized and fairly allocated to different
users.
3. Network provider
List the
characteristics of a system that is easy to administer and manage. Example:
Fault can be easily isolated and it is easy to account for usage.
1 Connectivity
A network
must provide connectivity among a set of computers
·
Links and Nodes
·
Types of Links or Connections
·
Direction of Data Flow
·
Unicast, Broadcast and Multicast
1.1 Links and Nodes
A network
consists of two or more computers directly connected by some physical medium,
such as a coaxial cable or an optical fiber. Such a physical medium is called
as links.
The links
are connected to the computers named as nodes.
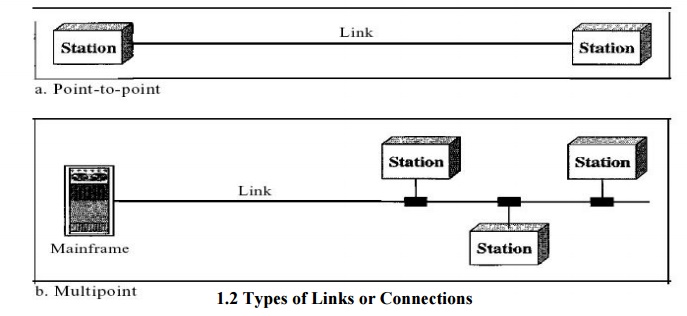
1.2 Types of Links or Connections
Point-to-Point
A
point-to-point connection provides a dedicated link between two devices. The
entire capacity of the link is reserved for transmission between those two
devices.
Multipoint
A
multipoint (also called multidrop) connection is one in which more than two
specific devices share a single link. In a multipoint environment, the capacity
of the channel is shared, either spatially or temporally. If several devices
can use the link simultaneously, it is a spatially
shared connection. If users must take
turns, it is a timeshared connection.
1.3 Direction of Data Flow
Communication between two devices can be simplex, half-duplex, or full-duplex as shown in Figure
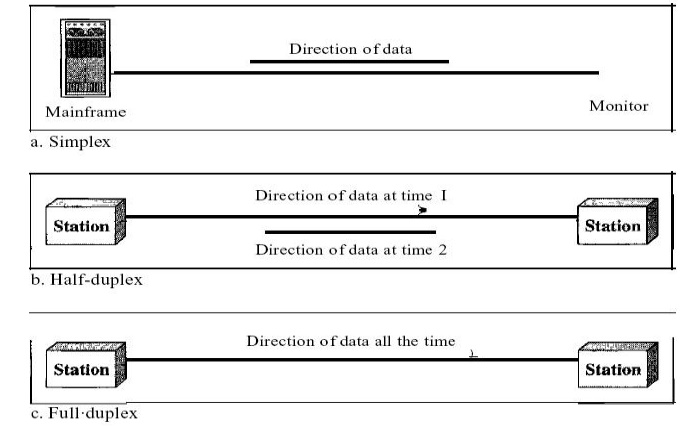
Simplex:
In
simplex mode, the communication is unidirectional, as on a one-way street. Only
one of the two devices on a link can transmit; the other can only receive (Fig
a). Keyboards and traditional monitors are examples of simplex devices.
Half-Duplex:
In
half-duplex mode, each station can both transmit and receive, but not at the
same time. When one device is sending, the other can only receive, and vice
versa(Fig b). The half-duplex mode is like a one-lane road with traffic allowed
in both directions.
Full-Duplex:
In
full-duplex both stations can transmit and receive simultaneously (Fig c)
1.3 Unicast, Broadcast and Multicast
Unicast
Unicast
is the term used to describe communication where a piece of information is sent
from one point to another point. In this case there is just one sender, and one
receiver.
Broadcast
Broadcast
is the term used to describe communication where a piece of information is sent
from one point to all other points. In this case there is just one sender, but
the information is sent to all connected receivers.
Multicast
Multicast
is the term used to describe communication where a piece of information is sent
from one or more points to a set of other points. In this case there is may be
one or more senders, and the information is distributed to a set of receivers
(theer may be no receivers, or any other number of receivers).
2 Cost-Effective Resource Sharing
Multiplexing
is a way that a system resource is shared among multiple users.

Two or
more simultaneous transmissions on a single circuit. Transparent to end user.
Multiplexing cost less.
Multiple
telephone channels may share a transmission link by means of multiplexing –
this sharing is static
–FDM
(Frequency Division Multiplexing) is used in analogue systems (a telephone
analogue channel has a nominal bandwidth of 4 kHz)
– STDM
(Synchronous Time Division Multiplexing) is used in digital systems (the basic
telephone digital channel has a capacity of 64 kbit/s)
3 Support for Common Services
A
computer network provides more than packet delivery between nodes. We don’t
want application developers to rewrite for each application higher layer
networking services.
The
channel is a pipe connecting two applications. How to fill the gap between the
underlying network capability and applications requirements? a set of common
services– Delivery guarantees, security, delay.
3.1 Types of Applications
Interactive
terminal and computer sessions:– Small packet length, small delay, high
reliability.
·
File transfer:– High packet length, high delay,
high reliability
·
Voice application:– Small packet length, small
delay, small reliability, high arrival rate
·
Video-on-demand:– Variable/high packet length,
fixed delay, small reliability
·
Video-conferencing– Variable/high packet length, small delay, small
reliability
4. NETWORK CRITERIA
A network
must be able to meet a certain number of criteria. The most important of these
are
performance,
reliability, and security.
Performance:
Performance
can be measured in many ways, including transit time and response time. Transit
time is the amount of time required for a message to travel from one device to
another. Response time is the elapsed time between an inquiry and a response.
The performance of a network depends on a number of factors, including the
number of users, the type of transmission medium, the capabilities of the
connected hardware, and the efficiency of the software. Performance is often
evaluated by two networking metrics: throughput and delay. We often need more
throughputs and less delay. However, these two criteria are often
contradictory. If we try to send more data to the network, we may increase
throughput but we increase the delay because of traffic congestion in the
network.
Reliability:
In
addition to accuracy of delivery, network reliability is measured by the
frequency of failure, the time it takes a link to recover from a failure, and
the network's robustness in a catastrophe.
Security:
Network
security issues include protecting data from unauthorized access, protecting
data from damage and development, and implementing policies and procedures for
recovery from breaches and data losses.
4.1 CATEGORIES OF NETWORK
There are
three primary categories are,
1. Local
area network.
2. Metropolitan
area network.
3. Wide area
network.
1. Local Area Network:
They are
usually privately owned and link the devices in a single office, building and
campus. Currently LAN size is limited to a few kilometers. It may be from two
PC‟s to throughout a company.
The most
common LAN topologies are bus, ring and star. They have data rates from 4 to 16
Mbps. Today the speed is on increasing and can reach 100 mbps.
2. Metropolitan Area Network:
They are
designed to extend over an entire city. It may be a single network or
connecting a number of LANs into a large network. So the resources are shared
between LANs. Example of MAN is, telephone companies provide a popular MAN
service called switched multi megabit data service (SMDS).
3. Wide Area Network:
It
provides a long distance transmission of data, voice, image and video
information over a large geographical are like country, continent or even the
whole world.
4.2 TOPOLOGIES:
Topology
refers to the way a network is laid out either physically or logically. Two or
more devices connect to a link; two or more links form a topology. It is the
geographical representation of the relationship of all the links and linking
devices to each other.
1. Mesh
2. Star
3. Tree
4. Bus
5. Ring
1. Mesh Topology:
Here every device has a dedicated point to point link to every other
device. A fully connected mesh can have n(n-1)/2 physical channels to link n devices.
It must have n-1 IO ports.
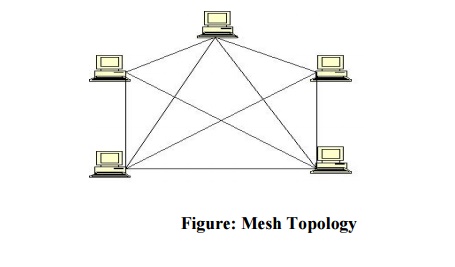
Advantages:
1.
They use dedicated links so each link can only
carry its own data load. So traffic problem can be avoided.
2. It is
robust. If anyone link get damaged it cannot affect others
3. It gives privacy
and security
4. Fault
identification and fault isolation are easy.
5.
Disadvantages:
1. The
amount of cabling and the number IO ports required are very large. Since every
device is connected to each other devices through dedicated links.
2. The sheer
bulk of wiring is larger then the available space
3. Hardware
required to connect each device is highly expensive.
Example:
A mesh
network has 8 devices. Calculate total number of cable links and IO ports
needed.
Solution:
Number of
devices = 8 Number of
links = n
(n-1)/2
= 8(8-1)/2
= 28
Number of
port/device = n-1
= 8-1 = 7
2. STAR TOPOLOGY:
Here each device has a dedicated link to the central „hub‟. There is no direct traffic
between devices. The transmission are occurred only through the central controller
namely hub.
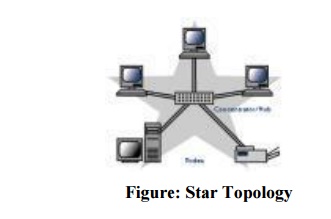
Advantages:
1. Less
expensive then mesh since each device is connected only to the hub.
2. Installation
and configuration are easy.
3. Less
cabling is need then mesh.
4. Robustness.
5. Easy to
fault identification & isolation.
Disadvantages:
1. Even it
requires less cabling then mesh when compared with other topologies it still
large.
TREE TOPOLOGY:
It is a
variation of star. Instead of all devices connected to a central hub here most
of the devices are connected to a secondary hub that in turn connected with
central hub. The central hub is an active hub. An active hub contains a
repeater, which regenerate the received bit pattern before sending.
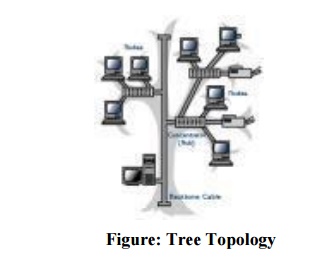
The
secondary hub may be active or passive. A passive hub means it just precedes a
physical connection only.
Advantages:
1. Can
connect more than star.
2. The
distance can be increased.
3. Can
isolate and prioritize communication between different computers.
4. BUS TOPOLOGY:
A bus
topology is multi point. Here one long cable is act as a backbo ne to link all
the devices are connected to the ba ckbone by drop lines and taps. A drop line
is the connection between the devices and the c able. A tap is the splice into
the main cable or puncture the sheathing.

Advantages:
1. Ease of
installation.
2. Less
cabling.
Disadvantages:
1. Difficult
reconfiguration and fault isolation.
2. Difficult
to add new devices.
3. Signal
reflection at top ca n degradation in quality
4. If any
fault in backbone c an stops all transmission.
5. RING TOPOLOGY:
Here each
device has a dedicated connection with two devices on eith er side of it. The
signal is passed in one direction from device to device until it reaches the
des tination and each device have repeater.

Advantages:
1. Easy to
install.
2. Easy to
reconfigure.
3. Fault
identification is easy.
Disadvantages:
1. Unidirectional
traffic.
2. Break in
a single ring can break entire network.
PROTOCOLS AND STANDARDS
Protocols:
In
computer networks, communication occurs between entries in different systems.
An entity is anything capable of sending or receiving information. But two
entities cannot communicate each other as sending or receiving. For
communication occurs the entities must agree on a protocol.
A
protocol is a set of rules that govern data communication. A protocol defines
what is communicated how it is communicated, and when it is communicated. The
key elements of a protocol are syntax, semantics and timing.
Syntax:
Syntax
refers to the structure or format of the data, means to the order how it is
presented.
Semantics:
Semantics
refers to the meaning of each section of bits. How is a particular pattern to
be interpreted, and when action is to be taken based on the interpretation.
Timing:
Timing
refers to two characteristics. They are,
1. When data
should be sent
2. When data
to be received.
Standards:
A
standard provides a model for development of a product, which is going to
develop. Standards are essential to create and maintain a product.
Data
communication products are fall into two categories. They are,
1. De facto
2. De jure
1. De facto:
They are
further classified into
1. Proprietary
2. Non
proprietary
1. Proprietary:
They are
originally invented by a commercial organization as a basis for the
operation
of its product. They are wholly owned by the company, which invented them. They
are
closed
standards.
2. Nonproprietary:
Groups or
committees that have passed them into public domain develop them.
They are
open standards.
2. De jure:
They have
been legislated by an officially recognized body.
STANDARDS ORGANIZATION:
Standards
are developed by,
1. Standards
creation committee
2. Forums
3. Regularity
agencies
1.
Standards
creation committees:
1. International
Standards Organization (ISO)
2. International
Telecommunications Union – Telecommunications Standards Section (ITU-T formally
CCITT)
3. The
American National Standards Institute (ANSI)
4. The
Institute of Electrical and Electronics Engineers (IEEE)
5. The
Electronic Industries Association (EIA)
6. Telcordia
2. Forums:
1. Frame
Relay Forum
2. ATM Forum
& ATM consortium
3. Internet
Society (ISOC) & Internet Engineering Task Force (IETF)
3. Regularity Agencies:
1. Federal
Communication commission
NETWORK ARCHITECTURE
A
computer network must provide general, cost effective, fair and robust among a
large number of computers. It must evolve to accommodate changes in both the
underlying technologies. To help to deal this network designers have developed
general blueprints called network architecture that guide the design and
implementation of networks.
Related Topics