Chapter: Information Security
Securing Components
SECURING COMPONENTS
Protecting
the components from potential misuse and abuse by unauthorized users.
ü Subject
of an attack
Computer
is used as an active tool to conduct the attack.
ü Object of
an attack
Computer
itself is the entity being attacked
Two types of attacks:
1. Direct attack
2. Indirect attack
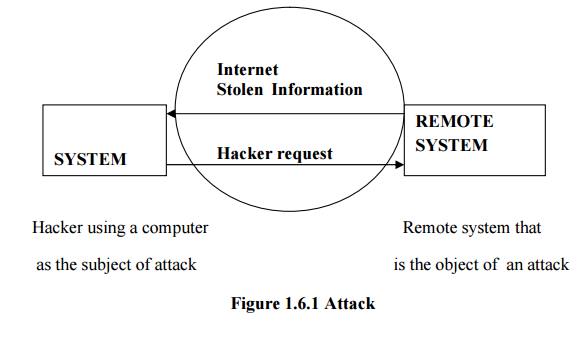
1. Direct
attack
When a Hacker uses his personal computer to break
into a system.[Originate from the threat itself]
2. Indirect
attack
When a
system is compromised and used to attack other system.
[Originate
from a system or resource that itself has been attacked, and is malfunctioning
or working under the control of a threat].
A computer can, therefore, be both the subject and
object of an attack when ,for example, it is first the object of an attack and
then compromised and used to attack other systems, at which point it becomes
the subject of an attack.
BALANCING INFORMATION SECURITY AND ACCESS
Has to provide the security and is also feasible to access the information for its application.
Information Security cannot be an absolute: it is a process, not a goal.
Should balance protection and availability.
Approaches to Information Security Implementation
ü Bottom- up- approach.
ü Top-down-approach
- Has higher probability of success.
- Project is initiated by upper level managers who issue policy & procedures & processes.
- Dictate the goals & expected outcomes of the project.
- Determine who is suitable for each of the required action.
Related Topics