Chapter: Information Security : Security Investigation
Risk Identification
RISK IDENTIFICATION
- IT
professionals to know their organization’s information assets through
identifying, classifying and prioritizing them.
- Assets
are the targets of various threats and threat agents, and the goal is to
protect the assets from the threats.
- Once the
organizational assets have been identified, a threat identification process is
undertaken.
- The
circumstances and settings of each information asset are examined to identify
vulnerabilities.
- When
vulnerabilities are found, controls are identified and assessed as to their
capability to limit possible losses in the eventuality of attack.
- The
process of Risk Identification begins with the identification of the
organization’s information assets and an assessment of their value.
- The
Components of this process are shown in figure
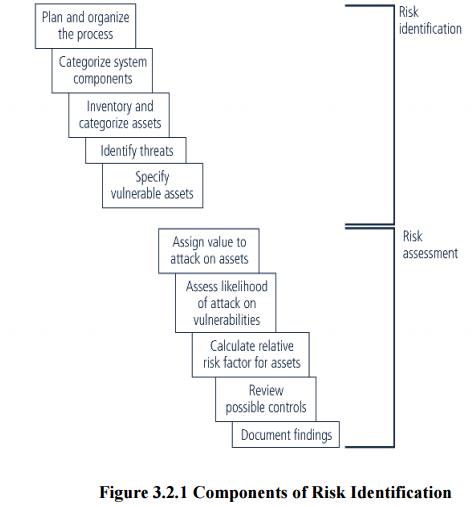
1 Asset Identification & Valuation
ü Includes
all the elements of an organization’s system, such as people, procedures, data
and information, software, hardware, and networking elements.
ü Then, you
classify and categorize the assets, adding details.
1.1 Components of Information System
Table 3.2.2.1 Categorization of IT Components
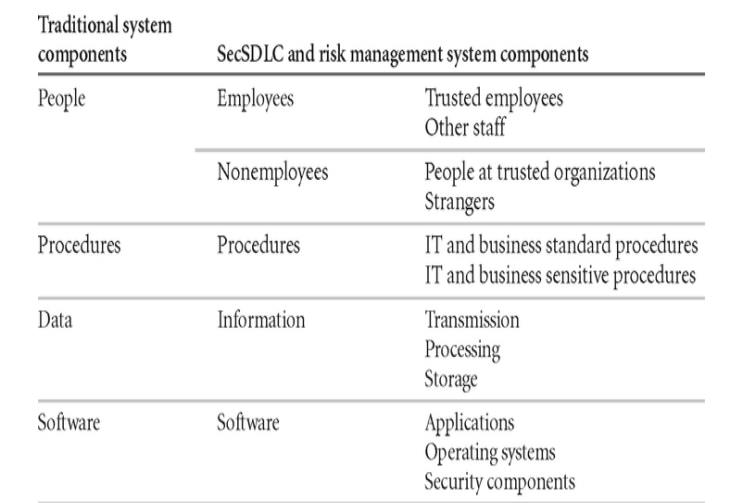
ü People
include employees and nonemployees. There are two categories of employees:
those who hold trusted roles and have correspondingly greater authority and
accountability, and other staff who have assignments without special
privileges. Nonemployees include contractors and consultants, members of other
organizations with which the organization has a trust relationship, and
strangers.
ü Procedures
fall into two categories: IT and business standard procedures, and IT and
business sensitive procedures. The business sensitive procedures are those that
may assist a threat agent in crafting an attack against the organization or
that have some other content or feature that may introduce risk to the
organization.
ü Data
Components have been expanded to account for the management of information in
all stages: Transmission, Processing, and Storage.
ü Software
Components can be assigned to one of three categories: Applications, Operating
Systems, or security components. Software Components that provide security
controls may span the range of operating systems and applications categories,
but are differentiated by the fact that they are the part of the information
security control environment and must be protected more thoroughly than other
system components.
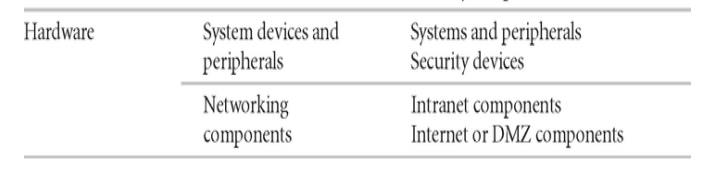
ü Hardware is assigned to one of two
categories: the usual systems devices and their peripherals, and the devices that are part of information security
control systems. The latter must be protected more thoroughly than the former.
1.2 People, Procedures,& Data Asset
Identification
ü People : Position name/number/ID: Supervisor; Security clearance level; special
skills. ü Procedures
: Description/intended
purpose/relationship to software / hardware and
networking
elements; storage location for update; storage location for reference.
ü Data : Classification; owner; Creator; Manager; Size of data structure; data
structure used;
online/offline/location/backup procedures employed.
1.3 Hardware, Software, and Network Asset
Identification
Depends
on the needs of the organization and its risk management efforts.
3.2.6 Name: Should adopt naming standards
that do not convey information to potential
system attackers.
3.2.7 IP address: Useful for network devices
& Servers. Many organizations use the dynamic host control protocol (DHCP) within TCP/IP that reassigns IP
numbers to devices as needed, making the use of IP numbers as part of the asset
identification process problematic. IP address use in inventory is usually
limited to those devices that use static IP addresses.
3.2.8 Media Access Control (MAC) address:
Electronic serial numbers or hardware addresses.
All network interface hardware devices have a unique number. The MAC
address
number is used by the network operating system as a means to identify a
specific network device. It is used by the client’s network software to
recognize traffic that it must
process.
3.3.0 Element Type: Document the function of each
Element by listing its type. For hardware,
a list of possible element types, such as servers, desktops, networking
devices or test equipment.
One server
might be listed as
ü Device
class= S (Server)
ü Device
OS= W2K ( Windows 2000)
ü Device
Capacity = AS ( Advanced Server )
3.3.2 Serial Number: For hardware devices, the
serial number can uniquely identify a specific device.
3.3.3 Manufacturer Name: Record the manufacturer of the
device or software component. This
can be useful when responding to incidents that involve these devices or when
certain manufacturers announce specific vulnerabilities.
3.3.4 Manufacturer’s Model No or Part No: Record
the model or part number of the element.
This record of exactly what the element is can be very useful in later analysis
of vulnerabilities, because some vulnerability instances only apply to specific
models of certain devices and software components.
3.3.5 Software Version, Update revision, or FCO number:
Document the specific software or
firmware revision number and, for hardware devices, the current field change
order (FCO) number. An FCO is an authorization issued by an organization for
the repair, modification, or update of a piece of equipment. Documenting the
revision number and FCO is particularly important for networking devices that
function mainly through the software running on them. For example, firewall
devices often have three versions: an operating system (OS) version, a software
version, and a basic input/output system (BIOS) firmware version.
3.3.6 Physical location: Note where this element is
located physically (Hardware)
3.3.7 Logical Location: Note where this element can be found on the organization’s network.
The
logical location is most useful for networking devices and indicates the
logical network where the device is connected.
Controlling Entity:
Identify which organizational unit controls the element.
1.4 Automated Risk Management Tools
ü Automated
tools identify the system elements that make up the hardware, software, &
network components.
ü Many
organizations use automated asset inventory systems.
ü The
inventory listing is usually available in a data base.
ü Once
stored, the inventory listing must be kept current, often by means of a tool
that periodically refreshes the data.
2 Information Asset Classification
ü In
addition to the categories, it is advisable to add another dimension to
represent the sensitivity & Security priority of the data and the devices
that store, transmit & process the data.
ü Eg: Kinds
of classifications are confidential data, internal data and public data.
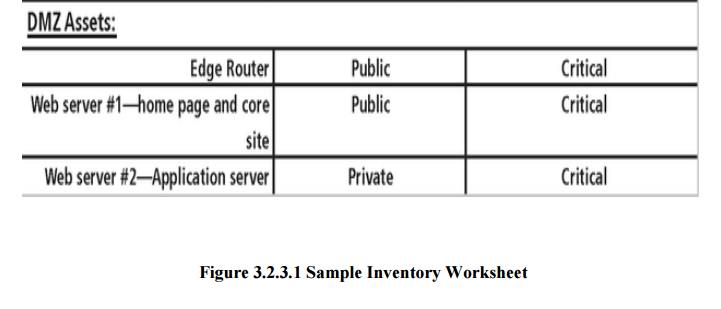
3 Information Asset Valuation
ü As each
asset is assigned to its category, posing a number of questions assists in
developing the weighting criteria to be used for information asset valuation or
impact evaluation. Before beginning the inventory process, the organization
should determine which criteria can best be used to establish the value of the
information assets. Among the criteria to be considered are:
Which information Asset is the most critical to the
success of the organization.
Which information asset generates the most revenue?
Which information asset generates the most
probability?
Which Information asset would be the expensive to
replace?
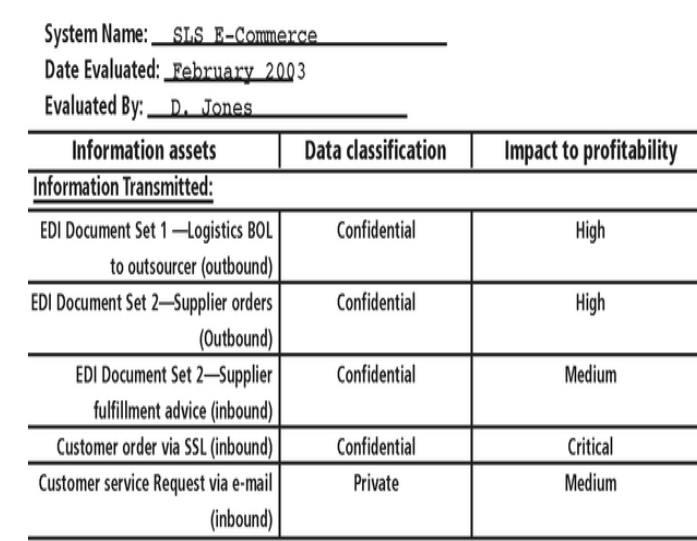
•
Data
Classification
Confidential
Internal
External
\endash
Confidential: Access to information with this
classification is strictly on a need-to-know basis or as required by the terms of a contract.
\endash
Internal: Used for all internal
information that does not meet the criteria for the confidential category and is to be viewed only by authorized
contractors, and other third parties.
\endash
External: All
information that has been approved by management for public release.
The
military uses five level classifications
= Unclassified
data
= Sensitive
But Unclassified data (SBU)
= Confidential
data
= Secret
data
= Top
Secret data
4 Unclassified data:
Information that can generally be distributed to the public without any
threat to U.S. National interests.
1.
Sensitive
But Unclassified data (SBU) : Any information of which the
loss, misuse, or unauthorized access
to, or modification of might adversely affect U.S. national interests, the
conduct of Department of Defense(DoD) programs, or the privacy of DoD
personnel.
2.
Confidential
data: Any
information or material the unauthorized disclosure of which reasonably could be expected to cause
damage to the national security.
3.
Secret: Any
information or material the unauthorized disclosure of which reasonably could be cause serious damage to the
national security.
4.
Top
Secret Data: Any information or material the unauthorized
disclosure of which reasonably could
be expected to cause exceptionally grave damage to the national security.
Organization may have
· Research
data
· Personnel
data
· Customer
data
· General
Internal Communications
Some organization may use
ü Public
data
ü For
office use only
ü Sensitive
data
ü Classified
data
Public: Information for general public
dissemination, such as an advertisement or
public release.
For Official Use Only:
Information that is not particularly sensitive, but not for public release, such as internal communications.
Sensitive: Information important to the
business that could embarrass the company
or cause loss of market share if revealed.
Classified: Information of the utmost
secrecy to the organization, disclosure of
which could severely impact the well-being of the organization.
Security Clearances
- The other
side of the data classification scheme is the personnel security clearance
structure.
- Each user
of data must be assigned a single authorization level that indicates the level
of classification he or she is authorized to view.
Eg: Data entry clerk, development Programmer,
Information Security Analyst, or even CIO.
Most organizations have a set of roles and the
accompanying security clearances associated with each role.
Overriding an employee’s security clearance is the
fundamental principle of “need-to-know”.
Management of classified data
Includes
its storage, distribution, portability, and destruction.
Military
uses color coordinated cover sheets to protect classified information from the
casual observer.
Each
classified document should contain the appropriate designation at the top and
bottom of each page.
A clean
desk policy requires that employees secure all information in appropriate
storage containers at the end of each day.
When
Information are no longer valuable, proper care should be taken to destroy them
by means of shredding, burning or transferring to a service offering authorized
document destruction.
Dumpster divingà to
retrieve information that could embarrass a company or compromise information security.
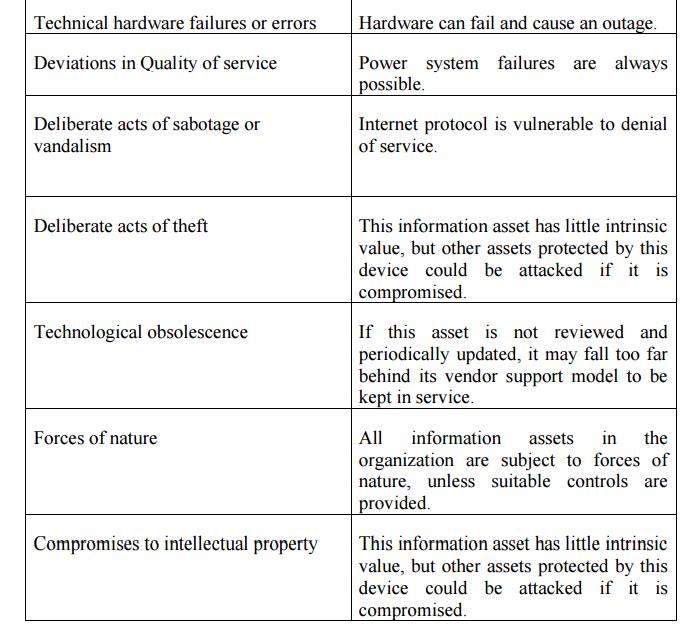
Threat
Identification
After
identifying the information assets, the analysis phase moves on to an
examination of the threats facing the organization.
Identify and Prioritize Threats and Threat Agents
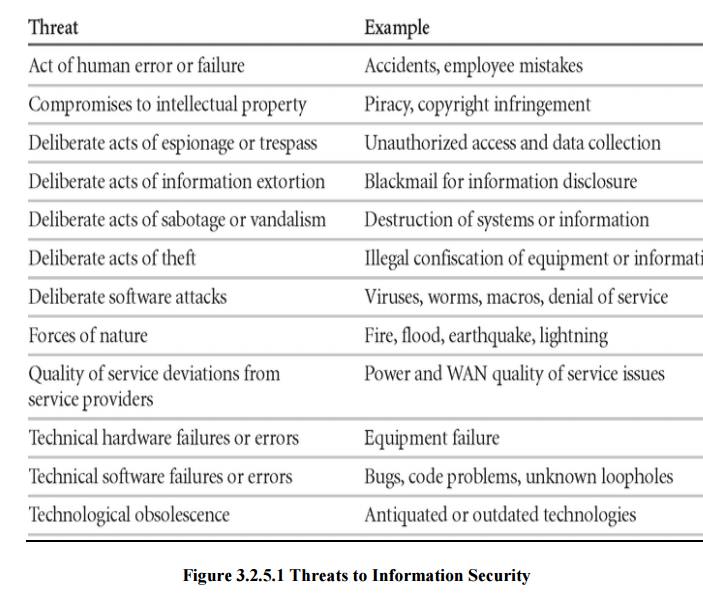
·
ü This
examination is known as a threat assessment. You can address e ach threat with
a few basic questions, as fo llows:
·
Which threats present a danger to an organization’s
assets in the given en vironment?
·
Which threats represent the most danger to the
organization’s information?
·
How much would it cost to recover from a successful
attack?
·
Which of the threats would require the greatest
expenditure to prevent?
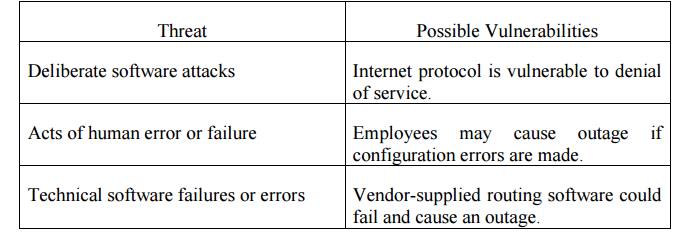
1.
Vulnerability
Identification:
Create a
list of Vulnerabilities for each information asset.
Groups of
people work iteratively in a series of sessions give best result.
At the
end of Identification process, you have a list of assets and their vulnerabilities.
Table 3.2.6.1 Vulnerability Assessment of a
Hypothetical DMZ Router
Related Topics