Chapter: Information Security : Security Analysis
Risk Management
RISK MANAGEMENT
ü
Definition:
The
formal process of identifying and controlling the risks facing an organization
is called risk management. It is the probability of an undesired event causing
damage to an asset. There are three steps
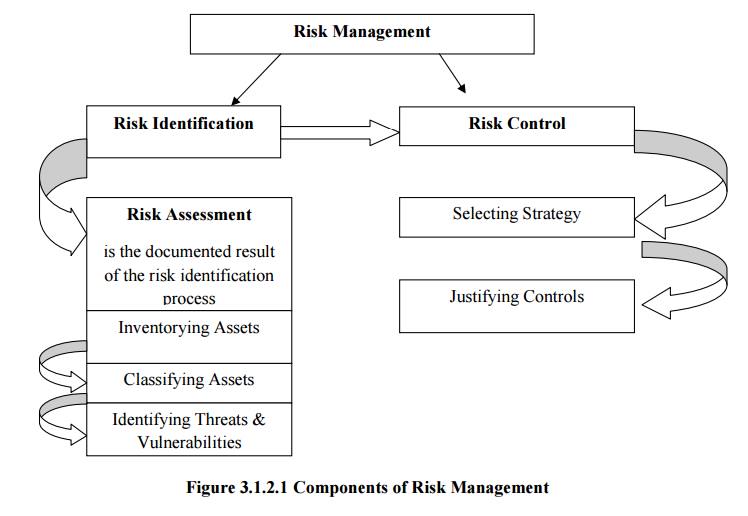
Risk Identification.
Risk Assessment
Risk Control
Risk
Identification: It is the process of examining and documenting
the security posture of an
organization’s information technology and the risk it faces.
Risk
Assessment: It is the documentation of the results of risk identification.
Risk
Control: It is the process of applying controls to reduce the risks to an organization’s data and information
systems.
To keep
up with the competition, organizations must design and create safe environments
in which business process and procedures can function.
These
environments must maintain Confidentiality & Privacy and assure the
integrity of organizational data-objectives that are met through the
application of the principles of risk management
2 Components of Risk Management
3 An Overview of Risk Management
Over
2,400 years ago by Chinese General Sun Tzu said
“1.If you
know the enemy & know yourself, you need not fear the result of a hundred
battles.
ü If you
know yourself but not the enemy, for every victory gained you will also suffer a defeat.
ü If you
know neither the enemy nor yourself, you will succumb in every battle”
Know Yourself
· Identify,
Examine & Understand the information systems.
· To
protect assets, you must understand what they are? How they add value to the
organization, and to which vulnerabilities they are susceptible.
· The
policies, Education and training programs, and technologies that protect
information must be carefully maintained and administered to ensure that they
are still effective.
Know the Enemy
ü Identifying, Examining &
Understanding the threats facing the organization.
The Roles of the Communities of Interest
· It is the
responsibility of each community of interest to manage the risks that
organization encounters.
Information Security
· Understand
the threats and attacks that introduce risk into the organization.
· Take a
leadership role in addressing risk.
Management & Users
· Management
must ensure that sufficient resource are allocated to the information security
& Information technology groups to meet the security needs of the
organization.
· Users
work with the systems and the data and are therefore well positioned to
understand the value of the information assets.
Information Technology
ü Must build secure systems and
operate them safely.
Three
communities of interest are also responsible for the following
· Evaluating
the risk controls.
· Determining
which control options are cost effective.
· Acquiring
or installing the needed controls.
· Overseeing
that the controls remain effective.
1.
Important
Risk Factors of information Security are
ü Understand
the threats and attacks that introduce risk into the organization.
ü Taking
asset inventory.
ü Verify
the threats and vulnerabilities that have been identified as dangerous to the
asset inventory, as well as the current controls and mitigation strategies.
ü Review
the cost effectiveness of various risk control measures.
Related Topics