Chapter: Security in Computing : Program Security
Hazard Analysis
Hazard Analysis
Hazard analysis is a set of systematic
techniques intended to expose potentially hazardous system states. In
particular, it can help us expose
security concerns and then identify prevention or mitigation strategies to
address them. That is, hazard analysis ferrets out likely causes of problems so
that we can then apply an appropriate technique for preventing the problem or
softening its likely consequences. Thus, it usually involves developing hazard
lists, as well as procedures for exploring "what if" scenarios to
trigger consideration of nonobvious hazards. The sources of problems can be
lurking in any artifacts of the development or maintenance process, not just in
the code, so a hazard analysis must be broad in its domain of investigation; in
other words, hazard analysis is a system issue, not just a code issue.
Similarly, there are many kinds of problems, ranging from incorrect code to
unclear consequences of a particular action. A good hazard analysis takes all
of them into account.
Although hazard analysis is
generally good practice on any project, it is required in some regulated and
critical application domains, and it can be invaluable for finding security
flaws. It is never too early to be thinking about the sources of hazards; the
analysis should begin when you first start thinking about building a new system
or when someone proposes a significant upgrade to an existing system. Hazard
analysis should continue throughout the system life cycle; you must identify
potential hazards that can be introduced during system design, installation,
operation, and maintenance.
A variety of techniques support the
identification and management of potential hazards. Among the most effective
are hazard and operability studies (HAZOP),
failure modes and effects analysis (FMEA), and fault tree analysis (FTA). HAZOP is a structured analysis technique originally
developed for the process control and chemical plant industries. Over the last
few years it has been adapted to discover potential hazards in safety-critical
software systems. FMEA is a bottom-up technique applied at the system component
level. A team identifies each component's possible faults or fault modes; the
team then determines what could trigger the fault and what systemwide effects
each fault might have. By keeping system consequences in mind, the team often
finds possible system failures that are not made visible by other analytical
means. FTA complements FMEA. It is a top-down technique that begins with a
postulated hazardous system malfunction. Then, the FTA team works backward to
identify the possible precursors to the mishap. By tracing back from a specific
hazardous malfunction, the team can locate unexpected contributors to mishaps,
and can then look for opportunities to mitigate the risks.
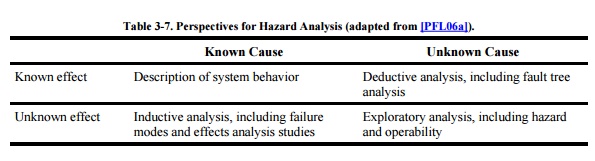
Each of these techniques is clearly useful for finding and
preventing security breaches. We decide which technique is most appropriate by
understanding how much we know about causes and effects. For example, Table 3-7 suggests that when we know the cause
and effect of a given problem, we can strengthen the description of how the
system should behave. This clearer picture will help requirements analysts
understand how a potential problem is linked to other requirements. It also
helps designers understand exactly what the system should do and helps testers
know how to test to verify that the system is behaving properly. If we can
describe a known effect with unknown cause, we use deductive techniques such as
fault tree analysis to help us understand the likely causes of the unwelcome
behavior. Conversely, we may know the cause of a problem but not understand all
the effects; here, we use inductive techniques such as failure modes and
effects analysis to help us trace from cause to all possible effects. For
example, suppose we know that a subsystem is unprotected and might lead to a
security failure, but we do not know how that failure will affect the rest of
the system. We can use FMEA to generate a list of possible effects and then
evaluate the tradeoffs between extra protection and possible problems. Finally,
to find problems about which we may not yet be aware, we can perform an
exploratory analysis such as a hazard and operability study.
We see in Chapter 8
that hazard analysis is also useful for determining vulnerabilities and mapping
them to suitable controls.
Related Topics