Chapter: Security in Computing : Program Security
Kinds of Malicious Code
Kinds of Malicious Code
Malicious code or rogue program is the
general name for unanticipated or undesired effects in programs or program
parts, caused by an agent intent on
damage. This definition excludes unintentional errors, although they can also
have a serious negative effect. This definition also excludes coincidence, in
which two benign programs combine for a negative effect. The agent is the writer of the program or
the person who causes its distribution. By this definition, most faults found
in software inspections, reviews, and testing do not qualify as malicious code,
because we think of them as unintentional. However, keep in mind as you read
this chapter that unintentional faults can in fact invoke the same responses as
intentional malevolence; a benign cause can still lead to a disastrous effect.
You are likely to have been
affected by a virus at one time or another, either because your computer was
infected by one or because you could not access an infected system while its
administrators were cleaning up the mess one made. In fact, your virus might
actually have been a worm: The terminology of malicious code is sometimes used
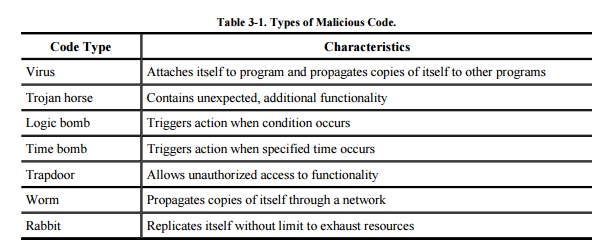
imprecisely. A virus is a program
that can replicate itself and pass on malicious code to other nonmalicious
programs by modifying them. The term "virus" was coined because the
affected program acts like a biological virus: It infects other healthy
subjects by attaching itself to the program and either destroying it or
coexisting with it. Because viruses are insidious, we cannot assume that a
clean program yesterday is still clean today. Moreover, a good program can be
modified to include a copy of the virus program, so the infected good program
itself begins to act as a virus, infecting other programs. The infection
usually spreads at a geometric rate, eventually overtaking an entire computing
system and spreading to all other connected systems.
A virus can be either transient or resident. A transient virus has a life that depends
on the life of its host; the virus runs when its attached program executes and
terminates when its attached program ends. (During its execution, the transient
virus may spread its infection to other programs.) A resident virus locates itself in memory; then it can remain active
or be activated as a stand-alone program, even after its attached program ends.
A Trojan horse is malicious code that, in addition to its primary
effect, has a second, nonobvious malicious effect. As an example of a computer
Trojan horse, consider a login script that solicits a user's identification and
password, passes the identification information on to the rest of the system
for login processing, but also retains a copy of the information for later,
malicious use. In this example, the user sees only the login occurring as
expected, so there is no evident reason to suspect that any other action took
place.
A logic bomb is a class of malicious code that "detonates"
or goes off when a specified condition occurs. A time bomb is a logic bomb whose trigger is a time or date.
A trapdoor or backdoor is
a feature in a program by which someone can access the program other than by
the obvious, direct call, perhaps with special privileges. For instance, an
automated bank teller program might allow anyone entering the number 990099 on
the keypad to process the log of everyone's transactions at that machine. In
this example, the trapdoor could be intentional, for maintenance purposes, or
it could be an illicit way for the implementer to wipe out any record of a
crime.
A worm is a program that spreads copies of itself through a network.
Shock and Hupp [SHO82] are apparently
the first to describe a worm, which, interestingly, was for nonmalicious
purposes. The primary difference between a worm and a virus is that a worm
operates through networks, and a virus can spread through any medium (but
usually uses copied program or data files). Additionally, the worm spreads
copies of itself as a stand-alone program, whereas the virus spreads copies of
itself as a program that attaches to or embeds in other programs.
White et al. [WHI89] also define a rabbit as a virus or worm that self-replicates without bound, with
the intention of exhausting some computing resource. A rabbit might create
copies of itself and store them on disk in an effort to completely fill the
disk, for example.
These definitions match current careful usage.
The distinctions among these terms are small, and often the terms are confused,
especially in the popular press. The term "virus" is often used to
refer to any piece of malicious code. Furthermore, two or more forms of
malicious code can be combined to produce a third kind of problem. For instance,
a virus can be a time bomb if the viral code that is spreading will trigger an
event after a period of time has passed. The kinds of malicious code are
summarized in Table 3-1.
Because "virus" is
the popular name given to all forms of malicious code and because fuzzy lines
exist between different kinds of malicious code, we are not too restrictive in
the following discussion. We want to look at how malicious code spreads, how it
is activated, and what effect it can have. A virus is a convenient term for
mobile malicious code, so in the following sections we use the term
"virus" almost exclusively. The points made apply also to other forms
of malicious code.
Related Topics