Chapter: Security in Computing : Program Security
Virus Signatures
Virus Signatures
A virus cannot be completely
invisible. Code must be stored somewhere, and the code must be in memory to
execute. Moreover, the virus executes in a particular way, using certain
methods to spread. Each of these characteristics yields a telltale pattern,
called a signature, that can be
found by a program that looks for it. The virus's signature is important for
creating a program, called a virus scanner, that can detect and, in some cases,
remove viruses. The scanner searches memory and long-term storage, monitoring
execution and watching for the telltale signatures of viruses. For example, a
scanner looking for signs of the Code Red worm can look for a pattern
containing the following characters:
/default.ida?NNNNNNNNNNNNNNNNNNNNNNNNNNNNNNN
NNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNN
NNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNN
NNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNN
NNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNNN
%u9090%u6858%ucbd3 %u7801%u9090%u6858%ucdb3%u7801%u9090%u6858
%ucbd3%u7801%u9090 %u9090%u8190%u00c3%u0003%ub00%u531b%u53ff %u0078%u0000%u00=a
HTTP/1.0
When the scanner recognizes a known virus's
pattern, it can then block the virus, inform the user, and deactivate or remove
the virus. However, a virus scanner is effective only if it has been kept up to
date with the latest information on current viruses. Sidebar 3-5 describes how viruses were the primary security
breach among companies surveyed in 2001.
Sidebar
3-5: The Malware Threat
Security
firm Symantec reports that malicious code threats rose in 2005, as in previous
years. In 2005, they found 21,858 new instances of viruses and worms, compared
to 11,846 for 2004 [SYM06]. Curiously, the number of distinct families
of malicious code decreased from 335 for 2004 to 274 for 2005, perhaps showing
that malicious code writers are becoming more adept at modifying a base attack
code type or that self-modifying malicious code is on the rise. E-mail is still
the preferred medium of delivery, with 92 percent of attacks using that for
delivery. Other popular methods were peer-to -peer sharing protocols at 14
percent and remote exploitation of a system or software vulnerability at 13
percent. (A single malicious code strain could use more than one propagation
method, accounting for the sum of methods exceeding 100 percent.)
Storage Patterns
Most viruses attach to programs that are stored
on media such as disks. The attached virus piece is invariant, so the start of
the virus code becomes a detectable signature. The attached piece is always
located at the same position relative to its attached file. For example, the
virus might always be at the beginning, 400 bytes from the top, or at the
bottom of the infected file. Most likely, the virus will be at the beginning of
the file because the virus writer wants to obtain control of execution before
the bona fide code of the infected program is in charge. In the simplest case,
the virus code sits at the top of the program, and the entire virus does its
malicious duty before the normal code is invoked. In other cases, the virus
infection consists of only a handful of instructions that point or jump to
other, more detailed instructions elsewhere. For example, the infected code may
consist of condition testing and a jump or call to a separate virus module. In
either case, the code to which control is transferred will also have a
recognizable pattern. Both of these situations are shown in Figure 3-9.
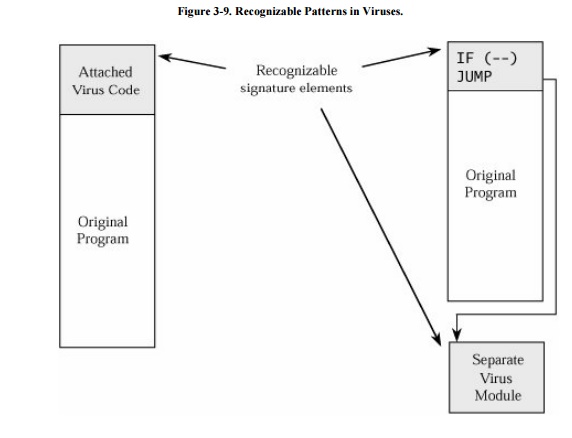
A virus may attach itself to
a file, in which case the file's size grows. Or the virus may obliterate all or
part of the underlying program, in which case the program's size does not
change but the program's functioning will be impaired. The virus writer has to
choose one of these detectable effects.
The virus scanner can use a
code or checksum to detect changes to a file. It can also look for suspicious
patterns, such as a JUMP instruction as the first instruction of a system
program (in case the virus has positioned itself at the bottom of the file but
is to be executed first, as in Figure 3-9).
Execution Patterns
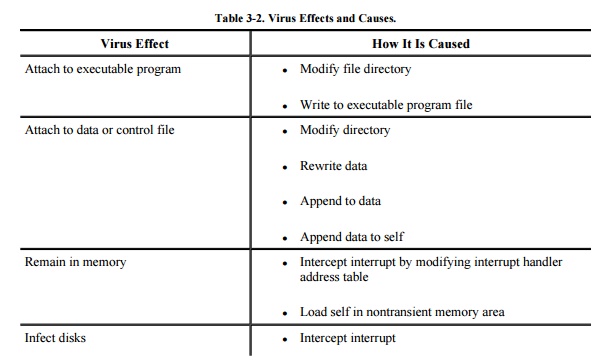
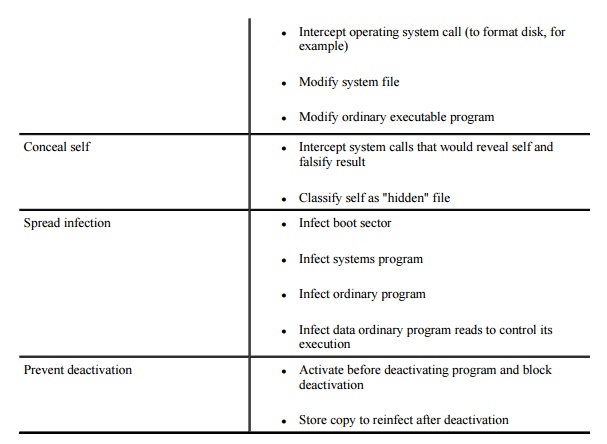
A virus writer may want a virus to do several
things at the same time, namely, spread infection, avoid detection, and cause
harm. These goals are shown in Table 3-2,
along with ways each goal can be addressed. Unfortunately, many of these
behaviors are perfectly normal and might otherwise go undetected. For instance,
one goal is modifying the file directory; many normal programs create files,
delete files, and write to storage media. Thus, no key signals point to the
presence of a virus.
Most virus writers seek to
avoid detection for themselves and their creations. Because a disk's boot
sector is not visible to normal operations (for example, the contents of the
boot sector do not show on a directory listing), many virus writers hide their
code there. A resident virus can monitor disk accesses and fake the result of a
disk operation that would show the virus hidden in a boot sector by showing the
data that should have been in the boot sector (which the virus has moved
elsewhere).
There are no limits to the
harm a virus can cause. On the modest end, the virus might do nothing; some
writers create viruses just to show they can do it. Or the virus can be
relatively benign, displaying a message on the screen, sounding the buzzer, or
playing music. From there, the problems can escalate. One virus can erase
files, another an entire disk; one virus can prevent a computer from booting,
and another can prevent writing to disk. The damage is bounded only by the
creativity of the virus's author.
Transmission Patterns
A virus is effective only if
it has some means of transmission from one location to another. As we have
already seen, viruses can travel during the boot process by attaching to an
executable file or traveling within data files. The travel itself occurs during
execution of an already infected program. Since a virus can execute any
instructions a program can, virus travel is not confined to any single medium
or execution pattern. For example, a virus can arrive on a disk or from a
network connection, travel during its host's execution to a hard disk boot
sector, reemerge next time the host computer is booted, and remain in memory to
infect other disks as they are accessed.
Polymorphic Viruses
The virus signature may be
the most reliable way for a virus scanner to identify a virus. If a particular
virus always begins with the string 47F0F00E08 (in hexadecimal) and has string
00113FFF located at word 12, it is unlikely that other programs or data files
will have these exact characteristics. For longer signatures, the probability
of a correct match increases.
If the virus scanner will
always look for those strings, then the clever virus writer can cause something
other than those strings to be in those positions. Many instructions cause no
effect, such as adding 0 to a number, comparing a number to itself, or jumping
to the next instruction. These instructions, sometimes called no-ops, can be
sprinkled into a piece of code to distort any pattern. For example, the virus
could have two alternative but equivalent beginning words; after being
installed, the virus will choose one of the two words for its initial word.
Then, a virus scanner would have to look for both patterns. A virus that can
change its appearance is called a polymorphic
virus. (Poly means "many" and morph means "form.")
A two -form polymorphic virus can be handled
easily as two independent viruses. Therefore, the virus writer intent on
preventing detection of the virus will want either a large or an unlimited
number of forms so that the number of possible forms is too large for a virus
scanner to search for. Simply embedding a random number or string at a fixed
place in the executable version of a virus is not sufficient, because the signature
of the virus is just the constant code excluding the random part. A polymorphic
virus has to randomly reposition all parts of itself and randomly change all
fixed data. Thus, instead of containing the fixed (and therefore searchable)
string "HA! INFECTED BY A VIRUS," a polymorphic virus has to change
even that pattern sometimes.
Trivially, assume a virus
writer has 100 bytes of code and 50 bytes of data. To make two virus instances
different, the writer might distribute the first version as 100 bytes of code
followed by all 50 bytes of data. A second version could be 99 bytes of code, a
jump instruction, 50 bytes of data, and the last byte of code. Other versions
are 98 code bytes jumping to the last two, 97 and three, and so forth. Just by
moving pieces around, the virus writer can create enough different appearances
to fool simple virus scanners. Once the scanner writers became aware of these
kinds of tricks, however, they refined their signature definitions.
A simple variety of
polymorphic virus uses encryption under various keys to make the stored form of
the virus different. These are sometimes called encrypting viruses. This type of virus must contain three distinct parts:
a decryption key, the (encrypted) object code of the virus, and the
(unencrypted) object code of the decryption routine. For these viruses, the
decryption routine itself, or a call to a decryption library routine, must be
in the clear so that becomes the signature.
To avoid detection, not every
copy of a polymorphic virus has to differ from every other copy. If the virus
changes occasionally, not every copy will match a signature of every other
copy.
Related Topics