Chapter: Security in Computing : Program Security
How Viruses Gain Control
How Viruses Gain Control
The virus (V) has to be
invoked instead of the target (T). Essentially, the virus either has to seem to
be T, saying effectively "I am T" or the virus has to push T out of
the way and become a substitute for T, saying effectively "Call me instead
of T." A more blatant virus can simply say "invoke me [you
fool]."
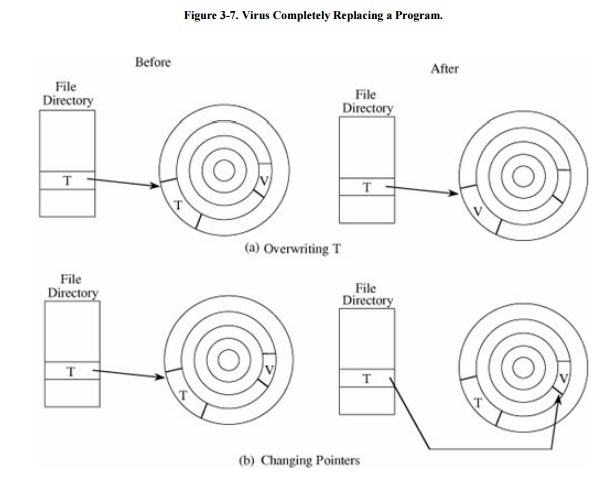
The virus can assume T's name by replacing (or
joining to) T's code in a file structure; this invocation technique is most appropriate
for ordinary programs. The virus can overwrite T in storage (simply replacing
the copy of T in storage, for example). Alternatively, the virus can change the
pointers in the file table so that the virus is located instead of T whenever T
is accessed through the file system. These two cases are shown in Figure 3-7.
The virus can supplant T by
altering the sequence that would have invoked T to now invoke the virus V; this
invocation can be used to replace parts of the resident operating system by
modifying pointers to those resident parts, such as the table of handlers for
different kinds of interrupts.
Related Topics