Chapter: Security in Computing : Program Security
Homes for Viruses
Homes for Viruses
The virus writer may find
these qualities appealing in a virus:
·
It is hard to detect.
·
It is not easily destroyed or deactivated.
·
It spreads infection widely.
·
It can reinfect its home program or other programs.
·
It is easy to create.
·
It is machine independent and operating system independent.
Few viruses meet all these
criteria. The virus writer chooses from these objectives when deciding what the
virus will do and where it will reside.
Just a few years ago, the challenge for the
virus writer was to write code that would be executed repeatedly so that the
virus could multiply. Now, however, one execution is enough to ensure
widespread distribution. Many viruses are transmitted by e-mail, using either
of two routes. In the first case, some virus writers generate a new e-mail
message to all addresses in the victim's address book. These new messages contain
a copy of the virus so that it propagates widely. Often the message is a brief,
chatty, nonspecific message that would encourage the new recipient to open the
attachment from a friend (the first recipient). For example, the subject line
or message body may read "I thought you might enjoy this picture from our
vacation." In the second case, the virus writer can leave the infected
file for the victim to forward unknowingly. If the virus's effect is not
immediately obvious, the victim may pass the infected file unwittingly to other
victims.
Let us look more closely at
the issue of viral residence.
One-Time Execution
The majority of viruses today
execute only once, spreading their infection and causing their effect in that
one execution. A virus often arrives as an e-mail attachment of a document
virus. It is executed just by being opened.
Boot Sector Viruses
A special case of virus
attachment, but formerly a fairly popular one, is the so-called boot sector virus. When a computer is
started, control begins with firmware that determines which hardware components
are present, tests them, and transfers control to an operating system. A given
hardware platform can run many different operating systems, so the operating
system is not coded in firmware but is instead invoked dynamically, perhaps
even by a user's choice, after the hardware test.
The operating system is
software stored on disk. Code copies the operating system from disk to memory
and transfers control to it; this copying is called the bootstrap (often boot)
load because the operating system figuratively pulls itself into memory by its
bootstraps. The firmware does its control transfer by reading a fixed number of
bytes from a fixed location on the disk (called the boot sector) to a fixed
address in memory and then jumping to that address (which will turn out to
contain the first instruction of the bootstrap loader). The bootstrap loader
then reads into memory the rest of the operating system from disk. To run a
different operating system, the user just inserts a disk with the new operating
system and a bootstrap loader. When the user reboots from this new disk, the
loader there brings in and runs another operating system. This same scheme is
used for personal computers, workstations, and large mainframes.
To allow for change, expansion, and
uncertainty, hardware designers reserve a large amount of space for the
bootstrap load. The boot sector on a PC is slightly less than 512 bytes, but
since the loader will be larger than that, the hardware designers support
"chaining," in which each block of the bootstrap is chained to
(contains the disk location of) the next block. This chaining allows big
bootstraps but also simplifies the installation of a virus. The virus writer
simply breaks the chain at any point, inserts a pointer to the virus code to be
executed, and reconnects the chain after the virus has been installed. This
situation is shown in Figure 3-8.
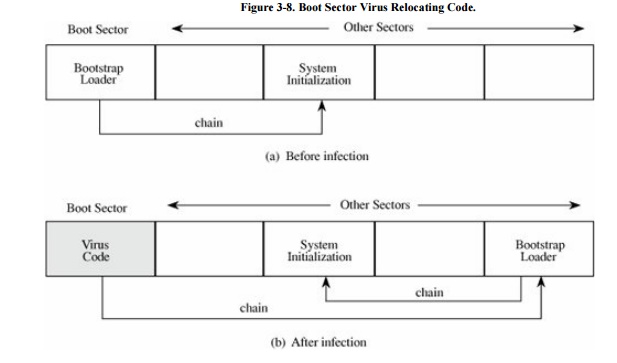
The boot sector is an
especially appealing place to house a virus. The virus gains control very early
in the boot process, before most detection tools are active, so that it can
avoid, or at least complicate, detection. The files in the boot area are
crucial parts of the operating system. Consequently, to keep users from accidentally
modifying or deleting them with disastrous results, the operating system makes
them "invisible" by not showing them as part of a normal listing of
stored files, preventing their deletion. Thus, the virus code is not readily
noticed by users.
Memory-Resident Viruses
Some parts of the operating
system and most user programs execute, terminate, and disappear, with their
space in memory being available for anything executed later. For very
frequently used parts of the operating system and for a few specialized user
programs, it would take too long to reload the program each time it was needed.
Such code remains in memory and is called "resident" code. Examples
of resident code are the routine that interprets keys pressed on the keyboard,
the code that handles error conditions that arise during a program's execution,
or a program that acts like an alarm clock, sounding a signal at a time the
user determines. Resident routines are sometimes called TSRs or "terminate
and stay resident" routines.
Virus writers also like to
attach viruses to resident code because the resident code is activated many
times while the machine is running. Each time the resident code runs, the virus
does too. Once activated, the virus can look for and infect uninfected
carriers. For example, after activation, a boot sector virus might attach
itself to a piece of resident code. Then, each time the virus was activated it
might check whether any removable disk in a disk drive was infected and, if
not, infect it. In this way the virus could spread its infection to all
removable disks used during the computing session.
A virus can also modify the
operating system's table of programs to run. On a Windows machine the registry
is the table of all critical system information, including programs to run at
startup. If the virus gains control once, it can insert a registry entry so
that it will be reinvoked each time the system restarts. In this way, even if
the user notices and deletes the executing copy of the virus from memory, the
virus will return on the next system restart.
Other Homes for Viruses
A virus that does not take up
residence in one of these cozy establishments has to fend more for itself. But
that is not to say that the virus will go homeless.
One popular home for a virus
is an application program. Many applications, such as word processors and
spreadsheets, have a "macro" feature, by which a user can record a
series of commands and repeat them with one invocation. Such programs also
provide a "startup macro" that is executed every time the application
is executed. A virus writer can create a virus macro that adds itself to the
startup directives for the application. It also then embeds a copy of itself in
data files so that the infection spreads to anyone receiving one or more of
those files.
Libraries are also excellent
places for malicious code to reside. Because libraries are used by many
programs, the code in them will have a broad effect. Additionally, libraries
are often shared among users and transmitted from one user to another, a
practice that spreads the infection. Finally, executing code in a library can
pass on the viral infection to other transmission media. Compilers, loaders,
linkers, runtime monitors, runtime debuggers, and even virus control programs
are good candidates for hosting viruses because they are widely shared.
Related Topics