Chapter: Computer Networks : Application Layer
Symmetric Key Cryptography
Symmetric-Key Cryptography
Symmetric-key
cryptography started thousands of years ago when people needed to exchange
secrets (for example, in a war). We still mainly use symmetric-key cryptography
in our network security.
Traditional Ciphers
The
traditional ciphers are character-oriented. Although these are now obsolete,
the goal is to show how modern ciphers evolved from them. We can divide
traditional symmetric-key ciphers into two broad categories: substitution
ciphers and transposition ciphers
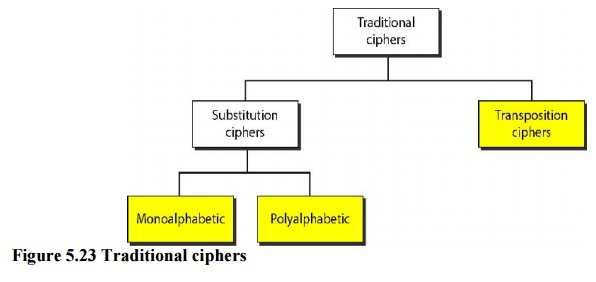
Substitution Cipher
A substitution cipher substitutes
one symbol with another. If the symbols in theplaintext are alphabetic
characters, we replace one character with another. For example, we can replace
character A with D, and character T with Z. If the symbols are digits (0 to 9),
we can replace 3 with 7, and 2 with 6. Substitution ciphers can be categorized
as either monoalphabetic or polyalphabetic ciphers. A substitution cipher
replaces one symbol with another.
In a monoalphabetic cipher, a
character (or a symbol) in the plaintext is alwayschanged to the same character
(or symbol) in the ciphertext regardless of its position in the text. For
example, if the algorithm says that character A in the plaintext is changed to
character D, every character A is changed to character D.
In a polyalphabetic cipher, each
occurrence of a character can have a differentsubstitute. The relationship
between characters in the plaintext to a character in the ciphertext is a
one-to-many relationship. For example, character A could be changed to D in the
beginning of the text, but it could be changed to N at the middle.
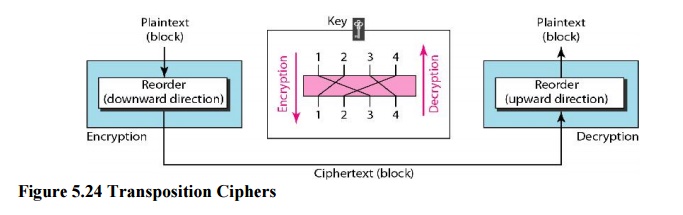
Transposition Ciphers
In a
transposition cipher, there is no substitution of characters; instead, their
locations change. A character in the first position of the plaintext may appear
in the tenth position of the ciphertext. A character in the eighth position may
appear in the first position. In other words, a transposition cipher reorders
the symbols in a block of symbols. A transposition cipher reorders (permutes)
symbols in a block of symbols.
Related Topics