Chapter: Computer Networks : Application Layer
Electronic Mail
Electronic Mail
One of
the most popular Internet services is electronic mail (e-mail). The designers
of the Internet probably never imagined the popularity of this application
program. Its architecture consists of several components. At the beginning of
the Internet era, the messages sent by electronic mail were short and consisted
of text only; they let people exchange quick memos.
1. Architecture
To
explain the architecture of e-mail, we give four scenarios. We begin with the
simplest situation and add complexity as we proceed. The fourth scenario is the
most common in the exchange of email.
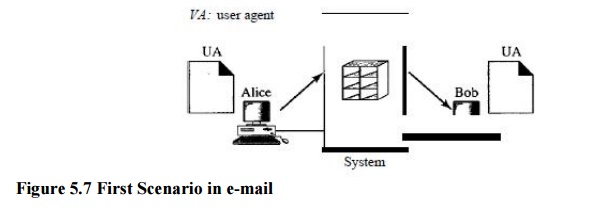
First Scenario
In the
first scenario, the sender and the receiver of the e-mail are users (or
application programs) on the same system; they are directly connected to a
shared system. The administrator has created one mailbox for each user where
the received messages are stored. A mailbox is part of a local hard drive, a
special file with permission restrictions. Only the owner of the mailbox has
access to it. When Alice, a user, needs to send a message to Bob, another user,
Alice runs a user agent (VA) program to prepare the message and store it in
Bob's mailbox. The message has the sender and recipient mailbox addresses
(names of files). Bob can retrieve and read the contents of his mailbox at his
convenience, using a user agent.
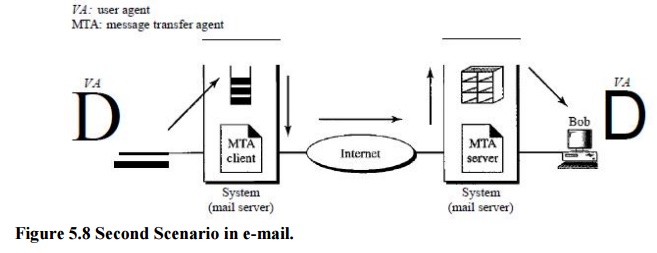
Second Scenario
In the
second scenario, the sender and the receiver of the e-mail are users (or
application programs) on two different systems. The message needs to be sent
over the Internet. Here we need user agents (VAs) and message transfer agents
(MTAs).
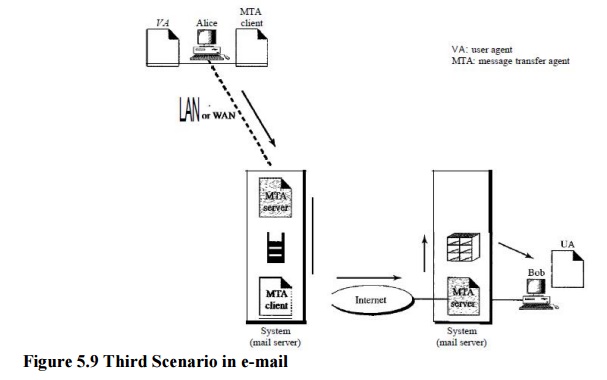
Third Scenario
In the
third scenario, Bob, as in the second scenario, is directly connected to his
system. Alice, however, is separated from her system. Either Alice is connected
to the system via a point-to-point WAN, such as a dial-up modem, a DSL, or a
cable modem; or she is connected to a LAN in an organization that uses one mail
server for handling e-mails-all users need to send their messages to this mail
server.
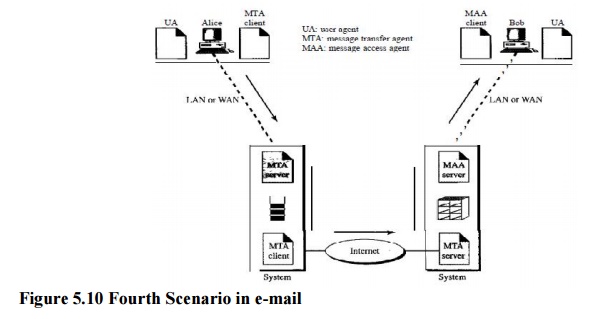
Fourth Scenario
In the
fourth and most common scenario, Bob is also connected to his mail server by a
WAN or a LAN. After the message has arrived at Bob's mail server, Bob needs to
retrieve it. Here, we need another set of client/server agents, which we call
message access agents (MAAs). Bob uses an MAA client to retrieve his messages.
The client sends a request to the MAA server, which is running all the time,
and requests the transfer of the messages.
2. User Agent
The first
component of an electronic mail system is the user agent (VA). It provides
service to the user to make the process of sending and receiving a message
easier.
Services Provided by a User Agent
A user
agent is a software package (program) that composes reads, replies to, and forwards
messages. It also handles mailboxes.
Composing Messages A user
agent helps the user compose the e-mail message to be sent out.Most user agents
provide a template on the screen to be filled in by the user. Some even have a
built-in editor that can do spell checking, grammar checking, and other tasks
expected from a sophisticated word processor. A user, of course, could
alternatively use his or her favourite text editor or word processor to create
the message and import it, or cut and paste it, into the user agent template.
Reading Messages The second duty of the user agent
is to read the incoming messages. When auser invokes a user agent, it first
checks the mail in the incoming mailbox. Most user agents show a one-line
summary of each received mail. Each e-mail contains the following fields.
1. A number
field.
2. A flag
field that shows the status of the mail such as new, already read but not
replied to, or read and replied to.
3. The size
of the message.
4. The
sender.
5. The
optional subject field.
Replying to Messages After
reading a message, a user can use the user agent to reply to amessage. A user
agent usually allows the user to reply to the original sender or to reply to
all recipients of the message. The reply message may contain the original
message (for quick reference) and the new message.
Forwarding Messages Replying
is defined as sending a message to the sender a message to thesender or
recipients of the copy. Forwarding is defined as sending the message to a third
party. A user agent allows the receiver to forward the message, with or without
extra comments, to a third party.
3. User Agent Types
There are
two types of user agents: command-driven and GUI-based.
Command-Driven
Command-driven
user agents belong to the early days of electronic mail. They are still present
as the underlying user agents in servers. A command-driven user agent normally
accepts a one-character command from the keyboard to perform its task. For
example, a user can type the character r, at the command prompt, to reply to the
sender of the message, or type the character R to reply to the sender and all
recipients. Some examples of command-driven user agents are mail, pine, and
elm.
GUI-Based Modem user agents are GUI-based. They
contain graphical-user interface (GUI)components that allow the user to
interact with the software by using both the keyboard and the mouse. They have
graphical components such as icons, menu bars, and windows that make the
services easy to access. Some examples of GUI-based user agents are Eudora, Microsoft's
Outlook, and Netscape.
Some
examples of GUIĀ·based user agents are Eudora, Outlook, and Netscape.
4. Message Transfer Agent: SMTP
The
actual mail transfer is done through message transfer agents. To send mail, a
system must have the client MTA, and to receive mail, a system must have a
server MTA. The formal protocol that defines the MTA client and server in the
Internet is called the Simple Mail Transfer Protocol (SMTP). As we said before,
two pairs of MTA client/server programs are used in the most common situation
(fourth scenario).
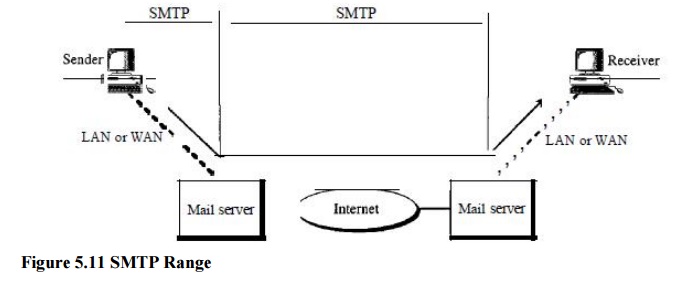
SMTP is
used two times, between the sender and the sender's mail server and between the
two mail servers. As we will see shortly, another protocol is needed between
the mail server and the receiver.
SMTP simply
defines how commands and responses must be sent back and forth. Each network is
free to choose a software package for implementation.
Commands and Responses
SMTP uses
commands and responses to transfer messages between an MTA client and an MTA
server. Each command or reply is terminated by a two-character (carriage return
and line feed) end-of-line token.
Commands: Commands are sent from the client
to the server. It consists of a keyword followedby zero or more arguments. SMTP
defines 14 commands. The first five are mandatory; every implementation must
support these five commands. The next three are often used and highly
recommended. The last six are seldom used.
Responses: Responses are sent from the
server to the client. A response is a three digit code thatmay be followed by
additional textual information.

5. Mail Transfer Phases
The
process of transferring a mail message occurs in three phases: connection
establishment, mail transfer, and connection termination.
Currently
two message access protocols are available: Post Office Protocol, version 3
(POP3) and Internet Mail Access Protocol, version 4 (IMAP4).
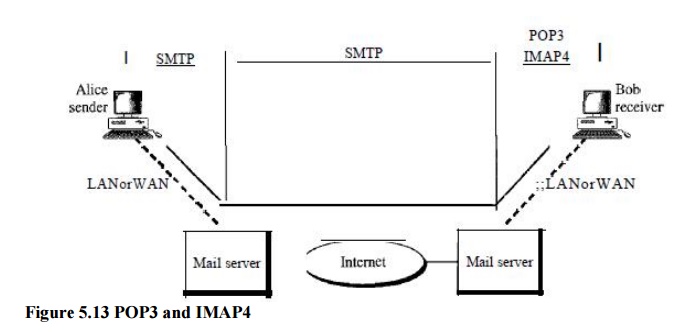
POP3
Post
Office Protocol, version 3 (POP3) is simple and limited in functionality. The
client POP3 software is installed on the recipient computer; the server POP3
software is installed on the mail server. Mail access starts with the client
when the user needs to download e-mail from the mailbox on the mail server.
POP3 has two modes: the delete mode and the keep mode. In the delete mode, the
mail is deleted from the mailbox after each retrieval. In the keep mode, the
mail remains in the mailbox after retrieval. The delete mode is normally used
when the user is working at her permanent computer and can save and organize
the received mail after reading or replying. The keep mode is normally used
when the user accesses her mail away from her primary computer (e.g., a
laptop). The mail is read but kept in the system for later retrieval and
organizing.
IMAP4
Another
mail access protocol is Internet Mail Access Protocol, version 4 (IMAP4). IMAP4
is similar to POP3, but it has more features; IMAP4 is more powerful and more
complex
Related Topics