Chapter: Computer Networks : Application Layer
Digital signatures: Direct, Arbitrated
Digital signatures
Digital Signature is an electronic signature that can be used to authenticate the identity of the sender of a message or document and possibly to ensure that the original content of the message or document that has been sent is unchanged. Digital signature is easily transportable, cannot be imitated by someone else, and can be automatically time-stamped. The ability to ensure that the original signed message arrived means that the sender cannot easily repudiate it later.
Having a sort of digital signature replacing handwritten signatures is essential in the cyber-world This is crucial between two parties who do not trust each other and need protection from each other’s later false claims
Requirements for a digital signature:
· Must authenticate the content of the message at the time of the signature
· Must authenticate the author, date, and time of the signature
· Receiver can verify the claimed identity of the sender
· Sender cannot later repudiate the content of the message
· Receiver cannot possibly have concocted the message himself
· Can be verified by third-parties to resolve disputes
Examples:
· The bank needs to verify the identity of the client placing a transfer order
· The client cannot deny later having sent that order
· It is impossible for the bank to create transfer orders and claim they actually came from the client
Computational requirements
· Must be a bit pattern depending on the message being signed
· Signature must use some information unique to the sender to prevent forgery and denial
· Computationally easy to produce a signature
· Computationally easy to recognize and verify the signature
· Computationally infeasible to forge a digital signature
Either by constructing a new message for an existing digital signature
Or by constructing a fraudulent digital signature for a given message
· Practical to retain a copy of the digital signature in storage
Two general schemes for digital signatures
1. Direct
2. Arbitrated
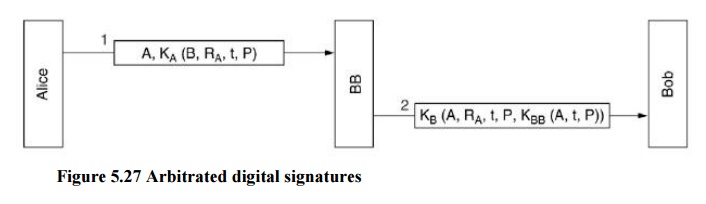
1. Arbitrated digital signatures
Every signed message from A to B goes to an arbiter BB (Big Brother) that everybody trusts BB checks the signature and the timestamp, origin, content, etc. BB dates the message and sends it to B with an indication that it has been verified and it is legitimate.
E.g., every user shares a secret key with the arbiter
· A sends to BB in an encrypted form the plaintext P together with B’s id, a timestamp and a random number RA
· BB decrypts the message and thus makes sure it comes from A; it also checks the timestamp to protect against replays
· BB then sends B the message P, A’s id, the timestamp and the random number RA; he also sends a message encrypted with his own private key (that nobody knows) containing A’s id, timestamp t and the plaintext P (or a hash)
· B cannot check the signature but trusts it because it comes from BB – he knows that because the entire communication was encrypted with KB
· B will not accept old messages or messages containing the same RA to protect against replay
· In case of dispute, B will show the signature he got from BB (only BB may have produced it) and BB will decrypt it
2. Direct digital signatures
· oThis involves only the communicating parties and it is based on public keysoThe sender knows the public key of the receiver
· Digital signature: encrypt the entire message (or just a hash code of the message) with the sender’s private key
· If confidentiality is required: apply the receiver’s public key or encrypt using a shared secret key
· In case of a dispute, the receiver B will produce the plaintext P and the signature E(KRA, P) – the judge will apply KUA and decrypt P and check the match: B does not know KRA and cannot have produced the signature himself
Weaknesses:
The scheme only works as long as KRA remains secret: if it is disclosed (or A discloses it herself), then the argument of the judge does not hold: anybody can produce the signature `
Attack: to deny the signature right after signing, simply claim that the private key has been lost – similar to claims of credit card misuse
If A changes her public-private keys (she can do that often) the judge will apply the wrong public key to check the signature
Attack: to deny the signature change your public-private key pair–this should not workif a PKI is used because they may keep trace of old public keys
A should protect her private key even after she changes the key
Attack: Eve could get hold of an old private key and sign a document with an oldtimestamp.
Any public-key systems may be used – the industry de facto choice is RSA
oThe proposed standard (1991) is the Digital Signature Standard (DSS) based on ElGamal(a public-key system)
o Latest update as a standard in 2009
o ElGamal is based on discrete logarithms
Immediate complains:
· Too secret – NSA was involved in developing the protocol for using ElGamal in DSS
· oToo slow–10 to 40 times slower than RSA-based signatures
· Too new–ElGamal had not yet been thoroughly analyzed
· Too insecure – only 512-bit key (subsequently 1024-bit keys adopted)
Related Topics