Chapter: Computer Networks : Application Layer
SMTP –Simple Mail Transfer Protocol
SMTP –SIMPLE MAIL TRANSFER
PROTOCOL
Next we look at SMTP- the protocol
used to transfer messages from one host to
another. To place SMTP in the right context, we need to identify the key
players. First, users interact with a mail reader when they compose ,file
,search, and read their email. There are countless mail readers available ,just
like there are many web browsers now include a mail reader. Second ,there is a
mail daemon running on each host. You can think of this process as playing the
role of a post office :mail readers give the daemon messages they want to send
to others users, the daemon uses SMTP running over TCP to transmit the message
into a daemon running on another machine, and the daemon puts incoming messages
into the user‟s
mailbox. Since SMTP is a protocol that anyone could implement , in theory there
could be many different implementations of the mail daemon. It runs out, though
that the mail daemon running on most hosts is derived from the sendma il
program originally implemented on berkely u nix.
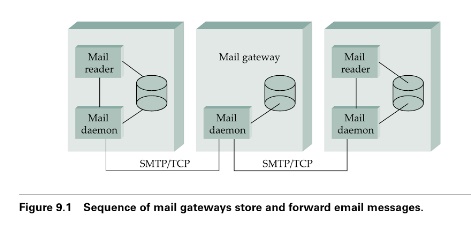
While it is certainly possible that the sendmail program on a s ender‟s machine establishes an SMTP/TCP connection to the sendmail program on the recipient‟s machine, in many cases the mail traverses o ne or more mail gateways on its route from the sender‟s host to the receiver‟s host. Like the end hosts, these gateways also run a send-mail pr ocess. It‟s not an accident that these intermediatee nodes are called “gateways” since their job is to store and forward email messages.
Mail Reader:
The final
step is for the user to actually receive her messages from th e mail box, read
them ,reply to them, and possib ly save a copy for future reference .The user
performs all the actions by interacting with a ma il reader. In many cases
,this reader is just a pro gram running on the same machine as the user‟s mailbox resides, in which case
it simply reads and writes the file that implements the mailbox .I n other
cases ,the user accesses her mailbox from a remote machine using yet another
protocol, such as the Post Office Protocol(POP ) or the Internet Message Access
Control(IMAP).It is beyond the scope of this book to discuss the user interface
aspects of the mail reader but it is definitely within our scope to talk about
the access protocol. We consider IMAP, in particular.
IMAP is
similar to S MTP in many ways .It is a client/server protocol running over TCP,
where the client (running on the user‟s desktop
machine) issues commands in the form of <CRLF> terminated ASCII text
lines and the mail server(running on the machine that maintains the user‟s mailbox) responds in-kind. The
exchange begins with the client authenticating herself, an d identifying the
mailbox she wants to acc ess. This can be represented by the simple state tr
ansaction diagram shown in the figure. In this d iagram, LOGIN, AUTHENTICATE,
SELECT, EXAMINE, CLOSE and LOGOUT are exampl e commands that the client can
issue, while OK is one possible server response. Other common c ommands include
FETCH, STORE, DELETE, an d EXPUNGE, with the obvious meanings. Additional
server responds include NO (client d oes not have permission to perform that
operation) and BAD (command is ill-formed).
When the
user asks to FETCH a message, the server returns it in MIM E format and the
mail reader decodes it. In addition to the message itself, IMAP also defines a
set of message attributes that are exchanged as part of other commands,
independent of transfer ring the message itself. Message attributes include
information like the size of the message, but more interestingly, various flags
associated with a message, such as Seen, Answered, Deleted and Recent. These
flags are used to keep the client and server synchronized, that is, when the
user deletes a message in the mail reader, the client needs to report this fact
to the mail server. Later, should the user decide to expunge all deleted
messages, the client issues an EXPUNGE command to the server, which knows to
actually remove all earlier deleted messages from the mail box.
Finally,
note that when the user replies to a message,or sends a new message, the mail
reader does not forward the message from the client to the mail server using
IMAP ,but it instead uses SMTP .This means that the user‟s mail server is effectively the
first mail gateway traversed along the path from the desktop to the recipient‟s mail box.
TCP/IP
protocol suite specifies a standard for the exchange of mail between machines.
It was derived from the (MTP) Mail Transfer Protocol. it deals with how the
underlying mail delivery system passes messages across a link from one machine
to another. The mail is enclosed in what is called an envelope. The envelope contains t he To and From fields and these
are followed by the mail . The mail consists of two parts namely the Header and
the Data. The Header has the To and From fields. If Headers are defined by us
they should start with X. The standard headers do not start with X. In SMTP
data portion can contain only printable ASCII characters The old method of
sending a binary file was to send it in uuencoded form but there was no way to
distinguish between the many types of binary files possible eg. .tar , .gz ,
.dvi etc.
Related Topics