Chapter: Computer Networks : Application Layer
Communication Security: Authentication protocols
Authentication protocols
Two approaches are generally used to defend replay attacks
Timestamps: A accepts a message as fresh only if it contains a timestamp that, in A’sjudgment, is close enough to A’s knowledge of current time – clocks need to be synchronized
Challenge/response: A, expecting a fresh message from B, first sends B a randomnumber (challenge) and requires that the subsequent message (response) received from B contains that random number or some agree-upon transformation on it (this is also called hand-shaking sometimes)
Authentication protocols and setting up secret keys
a. A.Direct authentication
1. Based on a shared secret master key
2. Based on a public-key system
3. Diffie-Hellman
b. Mediated authentication
1. Based on key distribution centers
2. Otway-Rees
3. Kerberos
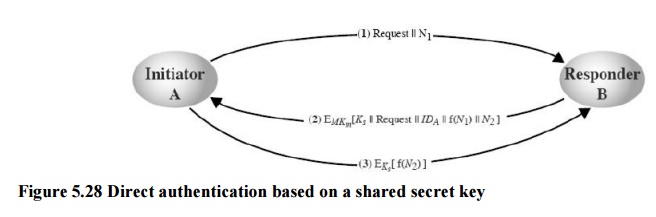
a. 1. Direct authentication based on a shared secret key
Assume here that A and B already share a secret key – this is called sometimes the master key MK because the two will only use this rarely, whenever they need to authenticate each other and establish a session key.
oMaster keys will only be used to establish session keys
oConcentrate here on how to establish session keys
Protocol
o A issues a requests to B for a session key and includes a nonce N1
o B responds with a message encrypted using the shared master key – include there the session key he selects, A’s id, a value f(N1) (say the successor of N1) and another nonce N2
At this point, A is sure of B’s identity: only he knows the master key; B is not sure of anything yet
A knows that the message is fresh: B sends a transformation on N1.
o Using the new session key, A return f(N2) to B
B is sure of A’s identity: only A can read the message he sent, including the session key
B knows that the message is fresh: A sends a transformation on N2
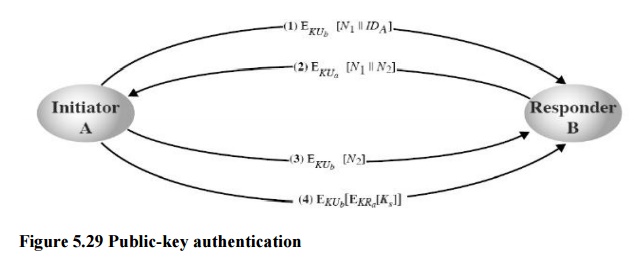
a. 2. A general scheme of public-key authentication (and distribution of secret keys)
o Assume here that A and B know each other’s public key (through a protocol such as those in Lecture 8)
oN1 and N2 in the scheme are random numbers–they ensure the authenticity of A and B(because only they can decrypt the messages and read N1 and N2)
oAfter Step 2, A is sure of B’s identity: right response to its challenge
o After Step 3, B is sure of A’s identity: right response to its challenge
a. 3. A concrete scheme: Diffie-Hellman key exchange
oThis is the first ever published public-key algorithm–used in a number of commercialproducts
o Elegant idea: establish a secret key based on each other’s public keys
Protocol:
oAlice and Bob need to agree on two large numbers n,g, where n is prime, (n-1)/2 is alsoprime and some extra conditions are satisfied by g (to defeat math attacks) – these numbers may be public so Alice could generate this on her own
oAlice picks a large (say, 512-bit) number x and B picks another one, say y
o Alice initiates the key exchange protocol by sending Bob a message containing (n,g,gx mod n)
oBob sends Alice a message containing gymod n
oAlice raises the number Bob sent her to the x-th power mod n to get the secret key:
(gy mod n)x mod n=gxy mod n
oBob raises the number Alice sent to the y-th power modulo n to get the secret key:
(gx mod n)y mod n=gxy mod n
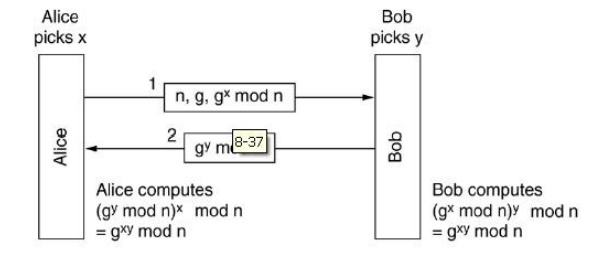
Figure 5.30 Diffie-Hellman key exchange
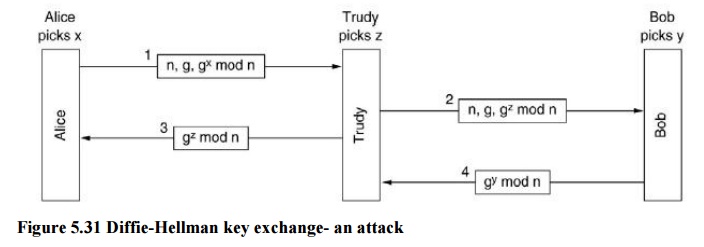
Diffie-Hellman key exchange: an attack
Security of the protocol: Eve has seen both messages A and B have changed–giveng,n, and gx mod n, she must find x.
· In math terms, she needs to compute a discrete logarithm
· Computing discrete logarithms is thought to be infeasible
· Is this enough to secure the protocol?
Man-in-the-middle attack
· Eve intercepts all communications between A and B – she will impersonate A in communications with B and will impersonate B in communications with A; E may forward a modified message to A and B
· A and B will never know that they are both actually talking to E
Attack can be defeated using signatures – both A and B will sign their messages with their private keys
b. Mediated authentication
1. Based on key distribution centers
2. Otway-Rees
3. Kerberos
Authentication using key distribution centers (KDC)
Setting up a shared key was fairly involved with the previous approaches and perhaps not quite worth doing (“sour grape attack”) Each user has to maintain a secret key (perhaps on some plastic card) for each of his friends – this may be a problem for popular people
Different approach: have a trusted key distribution center (KDC):
Each user maintains one single secret key – the one to communicate with KDC. Authentication and all communications go through KDC. Alice picks Ks and tells KDC that she wants to talk to Bob using Ks – A uses secret key KA used only to communicate with KDC.
KDC decrypts the message and sends Ks to Bob together with Alice’s id – KDC uses key KB used only to communicate with B. Authentication here is for free – key KA is only known to A and KDC
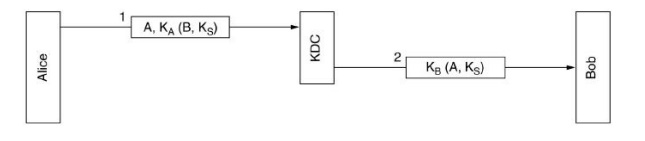
Figure 5.32 Authentication using key distribution centers (KDC)
Replay attack to the KDC-based protocol
Say Eve manages to get a job with Alice and after doing the job, she asks Alice to pay her by bank transfer. Alice establishes a secret key with the banker Bob and then sends Bob a message requesting money to be transferred to Eve’s account. Eve however is back to her old business, snooping on the network – she copies message 2 in the protocol and the request for money that follows Later Eve replays both messages to Bob – Bob will think that Alice has hired again Eve and pays Eve the money. Eve is able to do many iterations of the procedure – replay attack
Solution 1: include a timestamp with the message – any old message will be discarded Problem: clocks are not always exactly synchronized so there will be a period when the message is still valid
Solution 2: include a nonce (random number) with the message Problem: the nonces have to be remembered forever and any old one is discarded
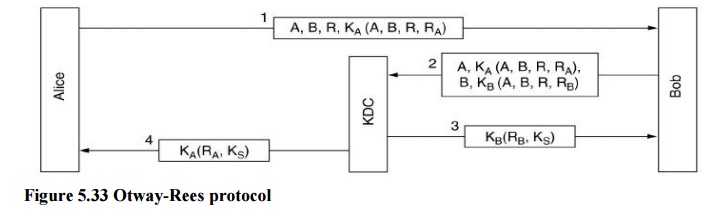
A stronger version of the KDC-based protocol (Otway-Rees protocol)
In the figure below, R, RA are random numbers generated by A, RB is a random number generated by B, KA and KB are as before the keys of A and B to communicate with KDC R is for KDC to check the integrity – KDC has to see R in both messages encrypted with KA and KB; if so, KDC generates the secret key and sends it to both A and B. RA and RB are for A and B to make sure the secret key comes from KDC. Resistant to replay attack: in such a case A and B will get keys they did not ask for or messages that do not match the random numbers they sent
Authentication using Kerberos
Kerberos is an authentication protocol used in many systems, including Windows 2000 and later versions, using the KDC-based approach Kerberos was the name of a multi-headed dog in Greek mythology that used to guard the entrance to Hades. Designed at MIT to allow workstation users to access network resources securely As such, it relies on the assumption that all locks are fairly well synchronized. Kerberos v4 is the most widely used version – the one we discuss here. Includes three servers that communicate with Alice (at the workstation) Authentication server (AS) – verifies the user during login It shares a secret password with each
user (plays the role of the KDC).
Ticket-granting server (TGS) – issues “proof of identity tickets” Tickets will be used by the user to perform various jobs.
oBob the server does the work Alice needs to do, based on the identity ticket Based on theidentity ticket will grant Alice the right she is entitled to
1. A sits down at an arbitrary public workstation and types her name Workstation sends her name to the AS in plaintext.
2. AS sends back a session key KS and a ticket KTGS(A,KS) for TGS – both encrypted with A’s secret key At this point the workstation asks for A’s password.
Password is used to generate the secret key and decrypt the message, obtaining the ticket for TGS.
Password is overwritten immediately to make sure it stays inside just for a few milliseconds, it never leaves the workstation; without the password Eve cannot get the ticket for TGS
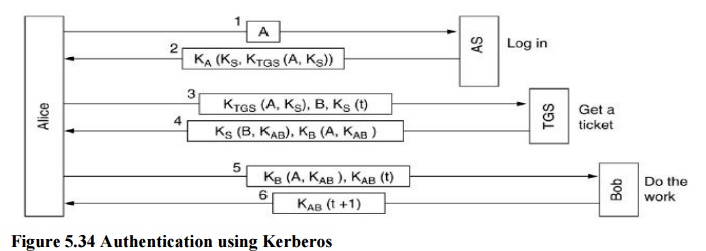
A tells the workstation she needs to contact the file server Bob
3.Workstation sends a message to TGS asking for a ticket to use Bob Key element here is the ticket for TGS received from AS – this proves to TGS that the sender is really A
4.TGS creates and sends back a session key KAB for A to use with B TGS sends a message encrypted with KS so that A can read and get KAB
TGS also includes a message intended only for Bob, sending A’s identity and the key KAB.
If Eve replays message 3 she will be foiled by the timestamp t Even if she replays the message quickly she will only get a copy of message 4 that she cannot read. Alice can now communicate with Bob using KAB
Bob confirms he has received the request and is ready to do the work.
Multiple realms can be accommodated in Kerberos, each with its own AS and TGS To get a ticket for a distant server B, Alice asks her own TGS for a ticket accepted by the distant TGS. She will go through the same protocol with the distant servers. The users of the two realms must trust each other’s TGS.
Related Topics