Chapter: Mobile Networks : Pervasive Computing
Security in Pervasive Computing
SECURITY:
Identification:
Various identification methods are used in
pervasive devices. One is user have to type the one which is stored in the
device otherwise the user can be identified using certificates.
Authentication:
The most common way of authenticating peers is by
using user name and password. For a client server connection authentication is
ensured by establishing secure socket layer. WTLS is used in WAP phones.
Wireless Authentication Module (WIM) is for smart cards. SIMs will be
authenticating the mobile terminal in GSM network.
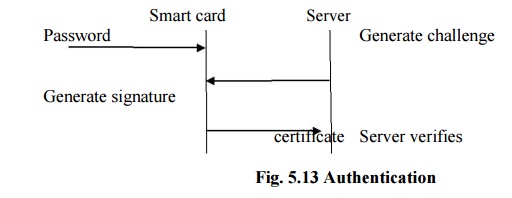
When smart card at the client and authentication
software is installed in the server then the server will produce a challenge to
the client and in return the client gives the signature and the certificate
which will be checked by the server.
Authorization:
Authorization is based on from which device the
user is accessing. In a banking transaction, If the user access from PC using
user identification and password and this will be the same for user from WAP
phone, PDAs but when user is from normal telephone then there is no entry for
user identification and password.
Transaction Authorization:
The applications such as home-banking, placing
orders, brokerage should authorize every individual transaction.
Digital Signature Endorsed by a
Password:
Digital
signature ensures that the particular request or message comes from the
authorized user since the user will be having the unique key from which a token
will be generated and the token generates the required signature which will be
passed to the server for verifying the transaction.
Transaction Authorization Number:
TAN (in blocks) is a secret number generated for
legitimate users in an organization. The users have to acknowledge immediately
after receiving the TAN and the user should ensure that it will be kept secret.
Whenever the user contacts the server, TAN should be entered which will be
compared with the stored one.
Non-Repudiation:
User A denying user B and user B denying user A is
called non-repudiation. This can be avoided by using efficient digital
signature.
2. Device Security
Trojan Horses
A Trojan
horse, or Trojan, is a
non-self-replicating type of malware which gains privileged access to the
operating system while appearing to perform a desirable function but instead
drops a malicious payload, often including a backdoor allowing unauthorized
access to the target's computer. These backdoors tend to be invisible to
average users, but may cause the computer to run slow. Trojans do not attempt
to inject themselves into other files like a computer virus. Trojan horses may
steal information, or harm their host computer systems. Trojans may use
drive-by downloads or install via online games or internet-driven applications
in order to reach target computers.
Security in WAP phones
WTLS is the layer that provides most of the
security functionalities for WAP applications. These functionalities include
client-server mutual authentication, privacy, data integrity, and non-repudiation.
WTLS and TLS: The
design of WTLS is based upon TLS (Transport Layer Security) that is in turn built upon SSL (Secure Socket Layer). TLS has
become de facto security protocol for ensuring end-to-end security for Internet
communications. Similar to TLS, WTLS requires the client and the server
negotiate and agree on a set of security parameters during the handshake before
the communicate channel can be established. Once handshake succeeds, the client
and the server can exchange information using the secrets known to both ends of
the channel. Since WTLS resembles TLS so much, one could consider that the WTLS
provides the same level of security as TLS does. However, due to the
limitations of wireless communications and the modifications WTLS made to
accommodate to these limitations, it has been shown that WTLS is vulnerable to
a variety of known attacks such as plaintext recovery attacks and datagram
truncation attacks.
Security in PDAs
Downloading
and installing arbitrary software makes prone Trojan horse attacks.
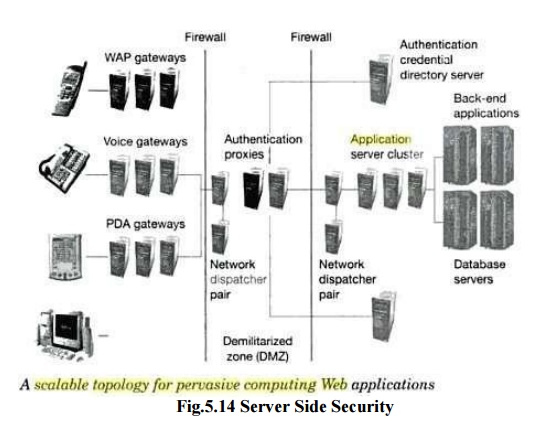
3. Server Side Security
4. Cryptographic Algorithms:
A
cryptographic algorithm, or cipher, is a mathematical function used in the
encryption and decryption process. A cryptographic algorithm works in combination
with a key—a word, number, or phrase—to encrypt the plaintext. The same
plaintext encrypts to different ciphertext with different keys. The security of
encrypted data is entirely dependent on two things: the strength of the
cryptographic algorithm and the secrecy of the key. A cryptographic algorithm,
plus all possible keys and all the protocols that make it work comprise a
cryptosystem
Symmetric cryptographic algorithm:
In secret
key cryptography, a single key is used for both encryption and decryption. The
sender uses the key (or some set of rules) to encrypt the plaintext and sends
the cipher text to the receiver. The receiver applies the same key to decrypt
the message and recover the plaintext. Because a single key is used for both
functions, secret key cryptography is also called symmetric encryption. With
this form of cryptography, it is obvious that the key must be known to both the
sender and the receiver; that, in fact, is the secret. The biggest difficulty
with this approach, of course, is the distribution of the key.
Asymmetric cryptographic algorithm:
Public or
asymmetric key cryptography involves the use of key pairs: one private key and
one public key. Both are required to encrypt and decrypt a message or
transmission. The private key, not to be confused with the key utilized in
private key cryptography, is just that, private. It is not to be shared with
anyone. The owner of the key is responsible for securing it in such a manner
that it will not be lost or compromised. On the other hand, the public key is
just that, public. Public key cryptography intends for public keys to be
accessible to all users. In fact, this is what makes the system strong. If a
person can access anyone public key easily, usually via some form of directory
service, then the two parties can communicate securely and with little effort,
i.e. without a prior key distribution arrangement.
Data Encryption Standard (DES):
DES is
the archetypal block cipher — an algorithm that takes a fixed-length string of
plaintext bits and transforms it through a series of complicated operations
into another cipher text bit string of the same length. In the case of DES, the
block size is 64 bits. DES also uses a key to customize the transformation, so
that decryption can supposedly only be performed by those who know the
particular key used to encrypt. The key ostensibly consists of 64 bits;
however, only 56 of these are actually used by the algorithm. Eight bits are
used solely for checking parity, and are thereafter discarded. Hence the
effective key length is 56 bits
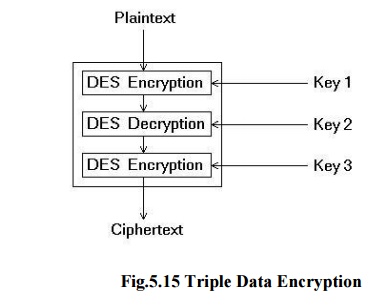
Triple Data Encryption Standard (Triple DES):
AES:
AES is
based on a design principle known as a substitution-permutation network, and is
fast in both software and hardware. Unlike its predecessor DES, AES does not
use a Feistel network. AES is a variant of Rijndael which has a fixed block
size of 128 bits, and a key size of 128, 192, or 256 bits.
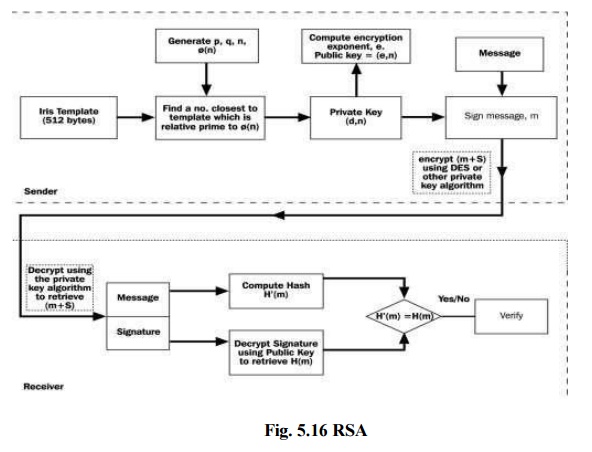
RSA:
Digital Signature:
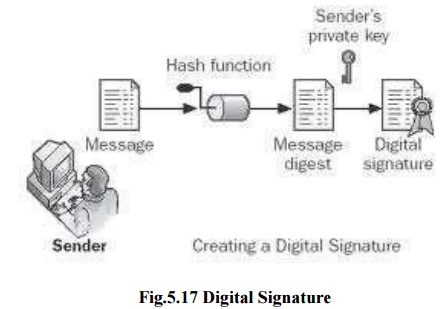
Elliptic Curve Cryptography:
Public-key
cryptography is based on the intractability of certain mathematical problems.
Early public-key systems are secure assuming that it is difficult to factor a
large integer composed of two or more large prime factors. For
elliptic-curve-based protocols, it is assumed that finding the discrete
logarithm of a random elliptic curve element with respect to a publicly known
base point is infeasible. The size of the elliptic curve determines the
difficulty of the problem. The primary benefit promised by ECC is a smaller key
size, reducing storage and transmission requirements—i.e., that an elliptic
curve group could provide the same level of security afforded by an RSA-based
system with a large modulus and correspondingly larger key—e.g., a 256-bit ECC
public key should provide comparable security to a 3072-bit RSA public key.
For current cryptographic purposes, an
elliptic curve is a
plane curve which consists of the
points satisfying the equation
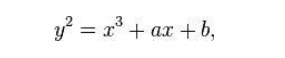
along
with a distinguished point at infinity, denoted ∞. (The coordinates here are to
be chosen from a fixed finite field of characteristic not equal to 2 or 3, or
the curve equation will be somewhat more complicated.)
Related Topics