Chapter: Mobile Networks : Cellular Wireless Network
Security
SECURITY :
GSM
offers several security services using confidential information stored in the
AuC and in the individual SIM (which is plugged into an arbitrary MS). The SIM
stores personal, secret data and is protected with a PIN against unauthorized
use. (For example, the secret key Ki used for authentication and encryption
procedures is stored in the SIM.) The security services offered by GSM are
explained below:
● ACCESS CONTROL AND AUTHENTICATION: The
first step includes the authentication of a valid user for the SIM. The user
needs a secret PIN to access the SIM. The next step is the subscriber
authentication .
● CONFIDENTIALITY: All user-related data is
encrypted. After authentication, BTS
and MS apply encryption to voice, data, and signaling. This confidentiality
exists only between MS and BTS, but it does not exist end-to-end or within the
whole fixed GSM/telephone network.
● ANONYMITY: To provide user anonymity, all
data is encrypted before transmission,
and user identifiers (which would reveal an identity) are not used over the
air. Instead, GSM transmits a temporary identifier (TMSI), which is newly
assigned by the VLR after each location update. Additionally, the VLR can
change the TMSI at any time. Three algorithms have been specified to provide
security services in GSM. Algorithm A3 is used for authentication, A5 for encryption,
and A8 for the generation of a cipher key. In the GSM standard only algorithm
A5 was publicly available, whereas A3 and A8 were secret, but standardized with
open interfaces. Both A3 and A8 are no longer secret, but were published on the
internet in 1998. This demonstrates that security by obscurity does not really
work. As it turned out, the algorithms are not very strong. However, network
providers can use stronger algorithms for authentication – or users can apply
stronger end-to-end encryption. Algorithms A3 and A8 (or their replacements)
are located on the SIM and in the AuC and can be proprietary. Only A5 which is
implemented in the devices has to be identical for all providers.
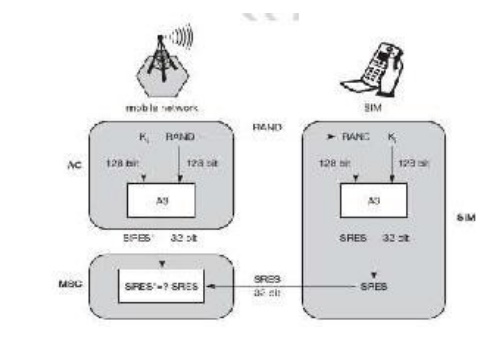
AUTHENTICATION
Before a
subscriber can use any service from the GSM network, he or she must be
authenticated. Authentication is based on the SIM, which stores the individual
authentication key Ki, the user identification IMSI, and the algorithm used for
authentication A3. Authentication uses a challenge-response method: the access
control AC generates a random number RAND as challenge, and the SIM within the
MS answers with SRES (signed response) as response. The AuC performs the basic
generation of random values RAND, signed responses SRES, and cipher keys Kc for
each IMSI, and then forwards this information to the HLR. The current VLR
requests the appropriate values for RAND, SRES, and Kc from the HLR.
For
authentication, For authentication, the VLR sends the random value RAND to the
SIM. Both sides, network and subscriber module, perform the same operation with
RAND and the key Ki, called A3. The MS sends back the SRES generated by the
SIM; the VLR can now compare both values. If they are the same, the VLR accepts
the subscriber, otherwise the subscriber is rejected.
ENCRYPTION :
To ensure
privacy, all messages containing user-related information are encrypted in GSM
over the air interface. After authentication, MS and BSS can start using
encryption by applying the cipher key Kc (the precise location of security
functions for encryption, BTS and/or BSC are vendor dependent). Kc is generated
using the individual key Ki and a random value by applying the algorithm A8.
Note that the SIM in the MS and the network both calculate the same Kc based on
the random value RAND. The key Kc itself is not transmitted over the air
interface.
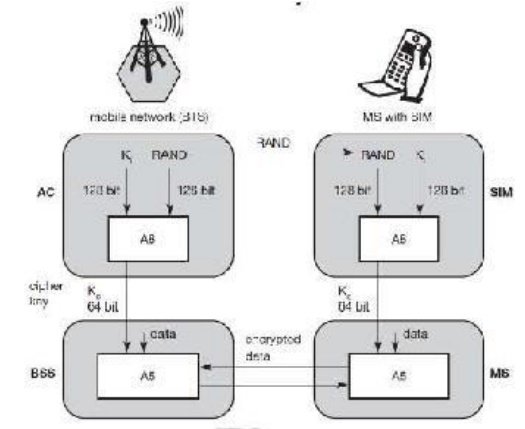
MS and
BTS can now encrypt and decrypt data using the algorithm A5 and the cipher key
Kc. As Figure shows, Kc should be a 64 bit key which is not very strong, but is
at least a good protection against simple eavesdropping. However, the
publication of A3 and A8 on the internet showed that in certain implementations
10 of the 64 bits are always set to 0, so that the real length of the key is
thus only 54 consequently, the encryption is much weaker.
Related Topics