Chapter: Cryptography and Network Security Principles and Practice : Cryptographic Data Integrity Algorithms : Cryptographic Hash Functions
Cryptographic Hash Functions
PART 3: CRYPTOGRAPHIC
DATA INTEGRITY ALGORITHMS
Chapter 11 CRYPTOGRAPHIC
HASH FUNCTIONS
o Applications of Cryptographic Hash
Functions
·
Message Authentication Digital Signatures Other Applications
o Two Simple
Hash Functions
o Requirements
and Security
·
Security
Requirements for Cryptographic Hash Functions Brute-Force Attacks
·
Cryptanalysis
o Hash Functions Based on Cipher Block Chaining
o Secure Hash
Algorithm (SHA)
·
SHA-512 Logic
·
SHA-512 Round
Function Example
o SHA-3
KEY POINTS
◆ A hash
function maps a variable-length message into a fixed-length hash value, or
message digest.
◆ Virtually
all cryptographic hash functions involve the iterative use of a compression
function.
◆ The
compression function used in secure hash algorithms falls into one of two
categories: a function specifically designed for the hash function or an
algorithm based on a symmetric block cipher. SHA and Whirlpool are examples of
these two approaches, respectively.
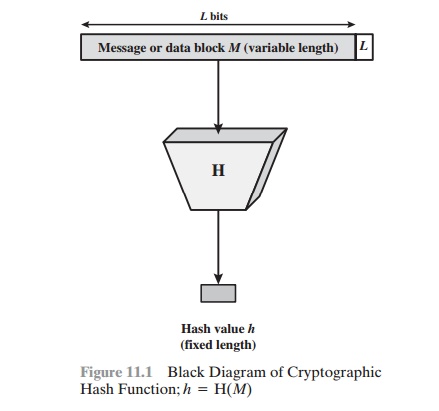
A hash function H accepts a variable-length block
of data M as
input and produces a fixed-size hash value h = H(M). A “good” hash function has the property
that the results of applying the function to a large
set of inputs will produce
outputs that are evenly distributed and apparently random. In general
terms, the principal
object of a hash function is data integrity. A change to any bit or bits in M results, with high probability, in a change to the hash code.
The kind of hash function needed for security applications is
referred to as a cryptographic hash
function. A cryptographic hash function is an algorithm for
which it is computationally infeasible (because no attack
is significantly more efficient
than brute force) to find
either (a) a data object that maps to a pre-specified hash result (the one-way property) or (b) two
data objects that map to the same hash result (the collision-free property). Because of these characteristics, hash functions are often used to determine
whether or not data has changed.
Figure 11.1 depicts the general operation of a cryptographic hash
function. Typically, the input is padded out to an integer multiple of some fixed length (e.g., 1024
bits), and the padding
includes the value of the length of the original message in bits. The length field is a security measure to increase the difficulty for an attacker to produce an
alternative message
with the same hash value.
This chapter begins with a discussion of the wide variety
of applications for cryptographic hash functions. Next, we look at the security
requirements for such functions. Then we look at the use of cipher
block chaining to implement a crypto-
graphic hash function. The remainder
of the chapter is devoted to the most impor- tant
and widely used family of cryptographic
hash functions, the Secure Hash
Algorithm (SHA) family.
Related Topics