Chapter: Security in Computing : Is There a Security Problem in Computing?
What Does "Secure" Mean?
Chapter 1
Is There a Security Problem in Computing?
What Does "Secure" Mean?
How do we protect our most
valuable assets? One option is to place them in a safe place, like a bank. We
seldom hear of a bank robbery these days, even though it was once a fairly
lucrative undertaking. In the American Wild West, banks kept large amounts of
cash on hand, as well as gold and silver, which could not be traced easily. In
those days, cash was much more commonly used than checks. Communications and
transportation were primitive enough that it might have been hours before the
legal authorities were informed of a robbery and days before they could
actually arrive at the scene of the crime, by which time the robbers were long
gone. To control the situation, a single guard for the night was only
marginally effective. Should you have wanted to commit a robbery, you might
have needed only a little common sense and perhaps several days to analyze the
situation; you certainly did not require much sophisticated training. Indeed,
you usually learned on the job, assisting other robbers in a form of
apprenticeship. On balance, all these factors tipped very much in the favor of
the criminal, so bank robbery was, for a time, considered to be a profitable
business. Protecting assets was difficult and not always effective.
Today, however, asset
protection is easier, with many factors working against the potential criminal.
Very sophisticated alarm and camera systems silently protect secure places like
banks whether people are around or not. The techniques of criminal
investigation have become so effective that a person can be identified by
genetic material (DNA), fingerprints, retinal patterns, voice, a composite
sketch, ballistics evidence, or other hard-to-mask characteristics. The assets
are stored in a safer form. For instance, many bank branches now contain less
cash than some large retail stores because much of a bank's business is
conducted with checks, electronic transfers, credit cards, or debit cards.
Sites that must store large amounts of cash or currency are protected with many
levels of security: several layers of physical systems, complex locks,
multiple-party systems requiring the agreement of several people to allow
access, and other schemes. Significant improvements in transportation and
communication mean that police can be at the scene of a crime in minutes;
dispatchers can alert other officers in seconds about the suspects to watch
for. From the criminal's point of view, the risk and required sophistication
are so high that there are usually easier ways than bank robbery to make money.
Protecting Valuables
This book is about protecting
our computer -related assets, not about protecting our money and gold bullion.
That is, we plan to discuss security for computing systems, not banks. But we
can learn from our analysis of banks because they tell us some general
principles about protection. In other words, when we think about protecting
valuable information, we can learn a lot from the way we have protected other
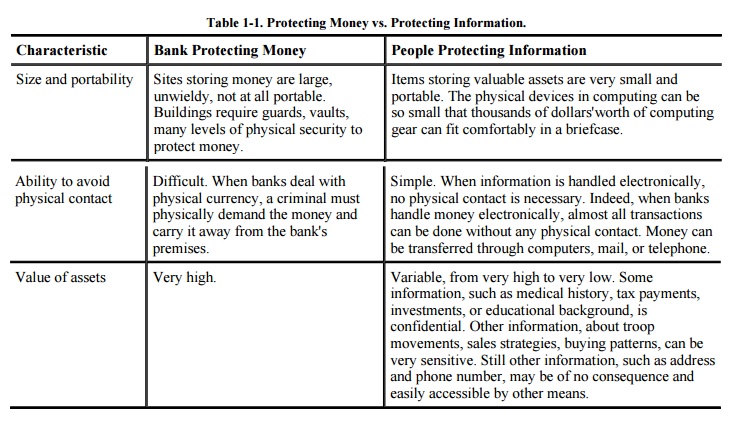
valuables in the past. For example, Table 1-1
presents the differences between how people protect computing systems and how
banks protect money. The table reinforces the point that we have many
challenges to address when protecting computers and data, but the nature of the
challenges may mean that we need different and more effective approaches than
we have used in the past.
Protecting our valuables,
whether they are expressed as information or in some other way, ranges from
quite unsophisticated to very sophisticated. We can think of the Wild West days
as an example of the "unsophisticated" end of the security spectrum.
And even today, when we have more sophisticated means of protection than ever
before, we still see a wide range in how people and businesses actually use the
protections available to them.
In fact, we can find far too
many examples of computer security that seem to be back in the Wild West days.
Although some organizations recognize computers and their data as valuable and
vulnerable resources and have applied appropriate protection, others are
dangerously deficient in their security measures. In some cases, the situation
is even worse than that in the Wild West; as Sidebar
1-1 illustrates, some enterprises do not even recognize that their
resources should be controlled and protected. And as software consumers, we
find that the lack of protection is all the more dangerous when we are not even
aware that we are susceptible to software piracy or corruption.
The possibility of crime is
bad enough. But worse yet, in the event of a crime, some organizations neither
investigate nor prosecute for fear that the revelation will damage their public
image. For example, would you feel safe depositing your money in a bank that
had just suffered a several million-dollar loss through computer-related embezzlement?
In fact, the breach of security makes that bank painfully aware of all its
security weaknesses. Once bitten, twice shy; after the loss, the bank will
probably enhance its security substantially, quickly becoming safer than a bank
that had not been recently victimized.
Even when organizations want
to take action against criminal activity, criminal investigation and
prosecution can be hindered by statutes that do not recognize electromagnetic
signals as property. The news media sometimes portrays computer intrusion by
teenagers as a prank no more serious than tipping over an outhouse. But, as we
see in later chapters, computer intrusion can hurt businesses and even take
lives. The legal systems around the world are rapidly coming to grips with the
nature of electronic property as intellectual property critical to
organizational or mission success; laws are being implemented and court
decisions declared that acknowledge the value of information stored or
transmitted via computers. But this area is still new to many courts, and few
precedents have been established.
Throughout this book, we look
at examples of how computer security affects our livesdirectly and indirectly.
And we examine techniques to prevent security breaches or at least to mitigate
their effects. We address the security concerns of software practitioners as
well as those professionals, managers, and users whose products, services, and
well-being depend on the proper functioning of computer systems. By studying
this book, you can develop an understanding of the basic problems underlying
computer security and the methods available to deal with them.
In particular, we do the
following:
examine the risks of security
in computing
consider available
countermeasures or controls
stimulate thought about
uncovered vulnerabilities
identify areas where more
work is needed
In this chapter, we begin by
examining what kinds of vulnerabilities computing systems are prone to. We then
consider why these vulnerabilities are exploited: the different kinds of
attacks that are possible. This chapter's third focus is on who is involved:
the kinds of people who contribute to the security problem. Finally, we
introduce how to prevent possible attacks on systems.
Characteristics of Computer Intrusion
Any part of a computing
system can be the target of a crime. When we refer to a computing system, we mean a collection of hardware, software,
storage media, data, and people that an organization uses to perform computing
tasks. Sometimes, we assume that parts of a computing system are not valuable
to an outsider, but often we are mistaken. For instance, we tend to think that
the most valuable property in a bank is the cash, gold, or silver in the vault.
But in fact the customer information in the bank's computer may be far more
valuable. Stored on paper, recorded on a storage medium, resident in memory, or
transmitted over telephone lines or satellite links, this information can be
used in myriad ways to make money illicitly. A competing bank can use this
information to steal clients or even to disrupt service and discredit the bank.
An unscrupulous individual could move money from one account to another without
the owner's permission. A group of con artists could contact large depositors
and convince them to invest in fraudulent schemes. The variety of targets and
attacks makes computer security very difficult.
Any system is most vulnerable
at its weakest point. A robber intent on stealing something from your house
will not attempt to penetrate a two-inch-thick metal door if a window gives
easier access. Similarly, a sophisticated perimeter physical security system
does not compensate for unguarded access by means of a simple telephone line
and a modem. We can codify this idea as one of the principles of computer
security.
Principle of Easiest Penetration: An intruder must be expected
to use any available means of penetration. The penetration may not necessarily be by the most obvious means, nor
is it necessarily the one against which the most solid defense has been
installed. And it certainly does not have to be the way we want the attacker to
behave.
This principle implies that
computer security specialists must consider all possible means of penetration.
Moreover, the penetration analysis must be done repeatedly, and especially
whenever the system and its security change. People sometimes underestimate the
determination or creativity of attackers. Remember that computer security is a
game with rules only for the defending team: The attackers can (and will) use
any means they can. Perhaps the hardest thing for people outside the security
community to do is to think like the attacker. One group of creative security
researchers investigated a wireless security system and reported a
vulnerability to the system's chief designer, who replied "that would
work, but no attacker would try it" [BON06].
Don't believe that for a minute: No attack is out of bounds.
Strengthening one aspect of a
system may simply make another means of penetration more appealing to
intruders. For this reason, let us look at the various ways by which a system
can be breached.
Related Topics