Chapter: Information Security : Physical Design
Information Security: Cryptography
CRYPTOGRAPHY
Security goals
We will first discuss three security goals: confidentiality, integrity and availability (Figure 16.1).
Confidentiality
Confidentiality, keeping information secret from unauthorized access, is probably the most common aspect of information security: we need to protect confidential information. An organization needs to guard against those malicious actions that endanger the confidentiality of its information.
Integrity
Information needs to be changed constantly. In a bank, when a customer deposits or withdraws money, the balance of their account needs to be changed. Integrity means that changes should be done only by authorized users and through authorized mechanisms.
Availability
The third component of information security is availability. The information created and stored by an organization needs to be available to authorized users and applications. Information is useless if it is not available. Information needs to be changed constantly, which means that it must be accessible to those authorized to access it. Unavailability of information is just as harmful to an organization as a lack of confidentiality or integrity. Imagine what would happen to a bank if the customers could not access their accounts for transactions.
Attacks
The three goals of security—confidentiality, integrity and availability—can be threatened by security attacks. Figure relates the taxonomy of attack types to security goals.
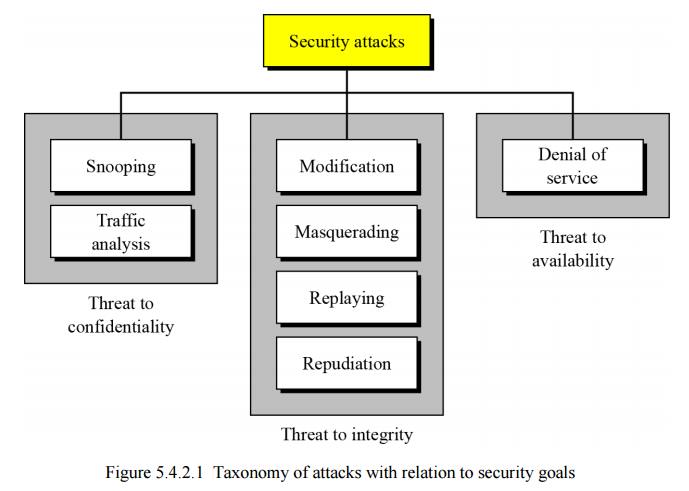
Attacks threatening confidentiality
In general, two types of attack threaten the confidentiality of information: snooping and traffic analysis. Snooping refers to unauthorized access to or interception of data. Traffic analysis refers other types of information collected by an intruder by monitoring online traffic.
The integrity of data can be threatened by several kinds of attack: modification, masquerading, replaying and repudiation.
Attacks threatening availability
Denial of service (DoS) attacks may slow down or totally interrupt the service of a system. The attacker can use several strategies to achieve this. They might make the system so busy that it collapses, or they might intercept messages sent in one direction and make the sending system believe that one of the parties involved in the communication or message has lost the message and that it should be resent.
Security services
Standards have been defined for security services to achieve security goals and prevent security attacks. Figure 16.3 shows the taxonomy of the five common services.
Techniques
The actual implementation of security goals needs some help from mathematics. Two techniques are prevalent today: one is very general—cryptography—and one is specific—steganography.
Cryptography
Some security services can be implemented using cryptography. Cryptography, a word with Greek origins, means “secret writing”.
Steganography
The word steganography, with its origin in Greek, means “covered writing”, in contrast to cryptography, which means
“secret writing”.
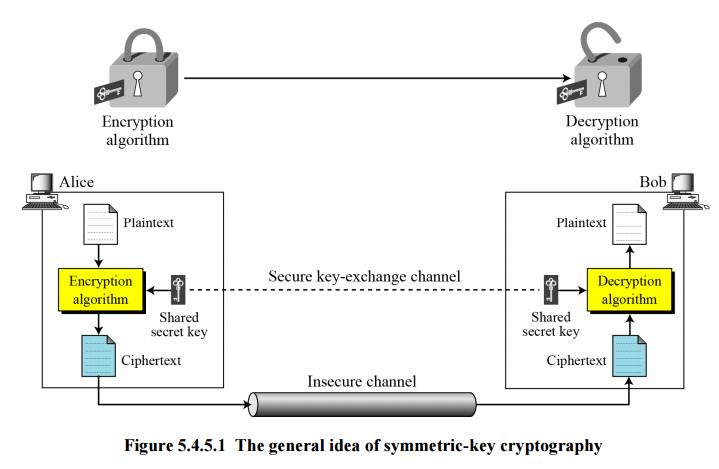
Symmetric-Key Cryptography
Figure 16.4 shows the general idea behind symmetric-key cryptography. Alice can send a message to Bob over an insecure channel with the assumption that an adversary, Eve, cannot understand the contents of the message by simply eavesdropping on the channel.
The original message from Alice to Bob is referred to as plaintext; the message that is sent through the channel is referred to as the ciphertext. Alice uses an encryption algorithm and a shared secret key. Bob uses a decryption algorithm and the same secret key.
Traditional ciphers
Traditional ciphers used two techniques for hiding information from an intruder: substitution and transposition.
Substitution ciphers
A substitution cipher replaces one symbol with another. If the symbols in the plaintext are alphabetic characters, we replace one character with another.
Example 16.1
ü Use the additive cipher with key = 15 to encrypt the message “hello”.
Solution
ü We apply the encryption algorithm to the plaintext, character by character:

ü The ciphertext is therefore “wtaad”.
Transposition ciphers
Example 16.2
Alice needs to send the message “Enemy attacks tonight” to Bob. Alice and Bob have agreed to divide the text into groups of five characters and then permute the characters in each group. The following shows the grouping after adding a bogus character (z) at the end to make the last group the same size as the others.

The key used for encryption and decryption is a permutation key, which shows how the character are permuted. For this message, assume that Alice and Bob used the following key:
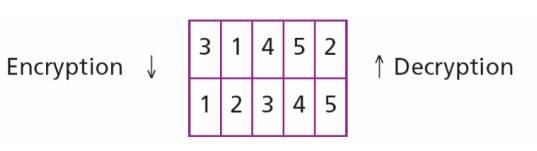
The third character in the plaintext block becomes the first character in the ciphertext block, the first character in the plaintext block becomes the second character in the ciphertext block and so on. The permutation yields:

Alice sends the ciphertext “eemyntaacttkonshitzg” to Bob. Bob divides the ciphertext into five-character groups and, using the key in the reverse order, finds the plaintext.
Modern symmetric-key ciphers
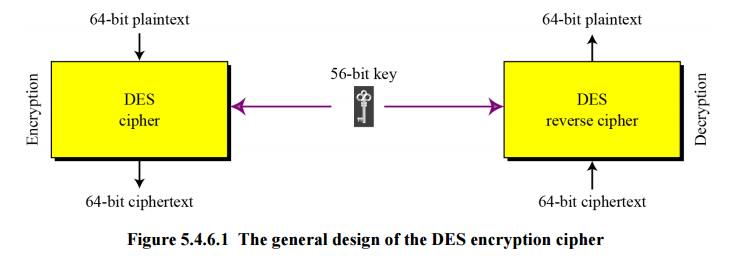
DES
The Data Encryption Standard (DES) is a symmetric-key block cipher published by the National Institute of Standards and Technology (NIST) in 1977. DES has been the most widely used symmetric-key block cipher since its publication.
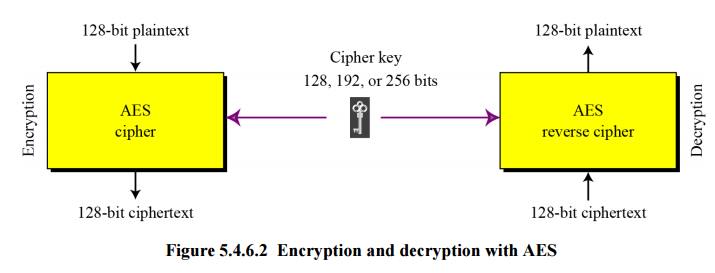
AES
The Advanced Encryption Standard (AES) is a symmetric-key block cipher published by the US National Institute of Standards and Technology (NIST) in 2001 in response to the shortcoming of DES, for example its small key size. See Figure 16.6.
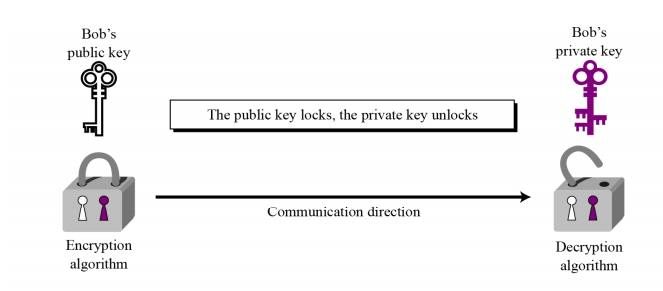
Asymmetric-Key Cryptography
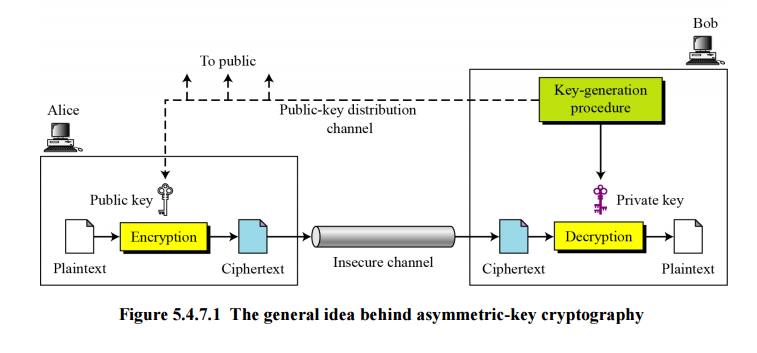
Figure shows the general idea of asymmetric-key cryptography as used for confidentiality. The figure shows that, unlike symmetric-key cryptography, there are distinctive keys in asymmetric-key cryptography: a private key and a public key. If encryption and decryption are thought of as locking and unlocking padlocks with keys, then the padlock that is locked with a public key can be unlocked only with the corresponding private key. Eve should not be able to advertise her public key to the community pretending that it is Bob’s public key.
Example 16.3
Bob chooses p = 7 and q = 11 and calculates n = 7 × 11 = 77. Now he chooses two exponents, 13 and 37, using the complex process mentioned before. The public key is (n = 77 and e = 13) and the private key is (d = 37). Now imagine that Alice wants to send the plaintext 5 to Bob. The following shows the encryption and decryption.

Asymmetric-Key Cryptography
Both symmetric-key and asymmetric-key cryptography will continue to exist in parallel. We believe that they are complements of each other: the advantages of one can compensate for the disadvantages of the other.
The number of secrets
The conceptual differences between the two systems are based on how these systems keep a secret. In symmetric-key cryptography, the secret token must be shared between two parties. In asymmetric-key cryptography, the token is unshared: each party creates its own token.
Symmetric-key cryptography is based on sharing secrecy;
asymmetric-key cryptography is based on personal secrecy.
A need for both systems
There are other aspects of security besides confidentiality that need asymmetric-key cryptography. These include authentication and digital signatures (discussed later). Whereas symmetric-key cryptography is based on substitution and permutation of symbols, asymmetric-key cryptography is based on applying mathematical functions to numbers.
In symmetric-key cryptography, symbols are permuted or substituted:
in asymmetric-key cryptography, numbers are manipulated.
Related Topics