Chapter: Information Security : Physical Design
Information Physical Security
PHYSICAL SECURITY
Introduction
Physical
security addresses design, implementation, and maintenance of countermeasures
that protect physical resources of an organization.
Most
controls can be circumvented if attacker gains physical access
Physical
security is as important as logical security
Seven
major sources of physical loss
Extreme
temperature
Gases
Liquids
Living
organisms
Projectiles
Movement
Energy
anomalies
Community
roles
General
management: responsible for facility security
IT
management and professionals: responsible for environmental and access security
Information
security management and professionals: perform risk assessments and
implementation reviews
Physical Access Controls
Secure
facility: physical location engineered with controls designed to minimize risk
of attacks from physical threats
Secure facility can take advantage of natural terrain, traffic flow, and
degree of urban development; can complement these with protection mechanisms
(fences, gates, walls, guards, alarms)
1 Controls for Protecting the Secure Facility
Walls, fencing, and gates
Guards
Dogs
ID Cards and badges
Locks and keys
Mantraps
Electronic monitoring
Alarms and alarm systems
Computer rooms and wiring closets
Interior walls and doors
2 ID Cards and Badges
ID card
is typically concealed
Name
badge is visible
Serve as
simple form of biometrics (facial recognition)
Should
not be only means of control as cards can be easily duplicated, stolen, and
modified
Tailgating
occurs when unauthorized individual follows authorized user through the control
3 Locks and Keys
Two types
of locks: mechanical and electromechanical
Locks can
also be divided into four categories: manual, programmable, electronic,
biometric
Locks
fail and alternative procedures for controlling access must be put in place
Locks
fail in one of two ways
Fail-safe
lock
Fail-secure
lock
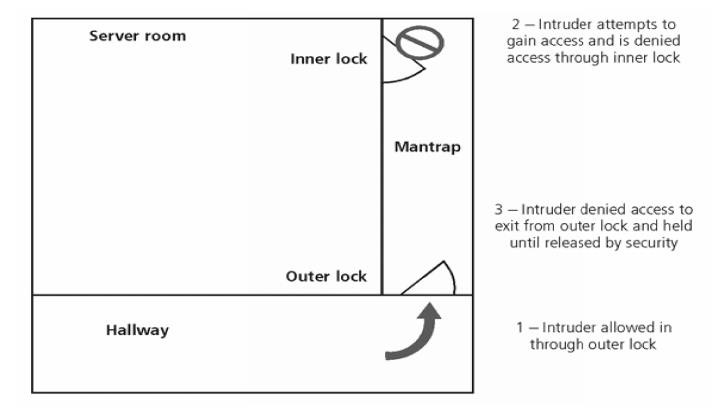
4 Mantraps
Small
enclosure that has entry point and different exit point
Individual
enters mantrap, requests access, and if verified, is allowed to exit mantrap
into facility
Individual
denied entry is not allowed to exit until security official overrides automatic
locks of the enclosure
5 Electronic Monitoring
Records
events where oth er types of physical controls are impractical or incomplete
May use
cameras with vi deo recorders; includes closed-circuit television (CCT) systems
Drawbacks
Reactive;
do not p revent access or prohibited activity
Recordings
often not monitored in real time; must be reviewed to have any value
Alarms
and Alarm Syste ms
Alarm
systems notify when an event occurs
Detect
fire, intrusion, env ironmental disturbance, or an interruption in se rvices
Rely on
sensors that d etect event; e.g., motion detectors, smoke d etectors, thermal
detectors, glass breakage detectors, weight sensors, contact sensors, vibr
ation sensors
6 Computer Rooms and Wiring
Closets
ü Require special attenti on to ensure confidentiality, integrity, and
availability of information
ü Logical controls easily d efeated if attacker gains physical access to
comp uting equipment
Custodial
staff often the least scrutinized persons who have access to offices; are given
greatest degree of unsupervised access
7 Interior Walls and Doors
Information
asset security sometimes compromised by construction of facility walls and
doors
Facility
walls typically either standard interior or firewall
High-security
areas must have firewall-grade walls to provide physical security from
potential intruders and improve resistance to fires
Doors
allowing access to high security rooms should be evaluated
Recommended
that push or crash bars be installed on computer rooms and closets
8 Fire Security and Safety
Most
serious threat to safety of people who work in an organization is possibility
of fire
Fires
account for more property damage, personal injury, and death than any other
threat
Imperative
that physical security plans examine and implement strong measures to detect
and respond to fires
9 Fire Detection and Response
Fire
suppression systems: devices installed and maintained to detect and respond to
a fire
Deny an
environment of heat, fuel, or oxygen
Water and
water mist systems
Carbon
dioxide systems
Soda acid
systems
Gas-based
systems
10 Fire Detection
Fire
detection systems fall into two general categories: manual and automatic
Part of a
complete fire safety program includes individuals that monitor chaos of fire
evacuation to prevent an attacker accessing offices
There are
three basic types of fire detection systems: thermal detection, smoke
detection, flame detection
11 Fire Suppression
Systems
consist of portable, manual, or automatic apparatus
Portable
extinguishers are rated by the type of fire: Class A, Class B, Class C, Class D
Installed
systems apply suppressive agents; usually either sprinkler or gaseous systems
Power Management and Conditioning
Electrical
quantity (voltage level; amperage rating) is a concern, as is quality of power
(cleanliness; proper installation)
Noise
that interferes with the normal 60 Hertz cycle can result in inaccurate time
clocks or unreliable internal clocks inside CPU
Grounding
ensures that returning flow of current is properly discharged to ground
Overloading
a circuit causes problems with circuit tripping and can overload electrical
cable, increasing risk of fire
Inventory Management
Computing
equipment should be inventoried and inspected on a regular basis
Classified
information should also be inventoried and managed
Physical
security of computing equipment, data storage media and classified documents
varies for each organization
Related Topics