Chapter: Cryptography and Network Security Principles and Practice : One Symmetric Ciphers : Block Cipher Operation
Electronic Code Book
ELECTRONIC CODE BOOK
A block cipher takes a fixed-length block of text of length b bits and a key as input and
produces a b-bit block
of ciphertext. If the amount
of plaintext to be encrypted is greater than b bits, then the block
cipher can still
be used by breaking the plaintext
up into b-bit blocks. When multiple blocks of plaintext
are encrypted using the same key, a number of security issues
arise. To apply
a block cipher
in a variety of applica- tions, five modes of operation have
been defined by NIST (SP 800-38A). In essence,
a mode of operation is a technique for
enhancing the effect of a cryptographic algorithm
or adapting the algorithm for an application, such as applying a block cipher to a sequence
of data blocks
or a data stream. The five modes are intended to cover
a wide variety of applications of encryption for which a block cipher
could be used. These modes are intended
for use with any symmetric
block cipher, including triple DES and AES. The modes are summarized in Table 6.1 and described in this and the following sections.
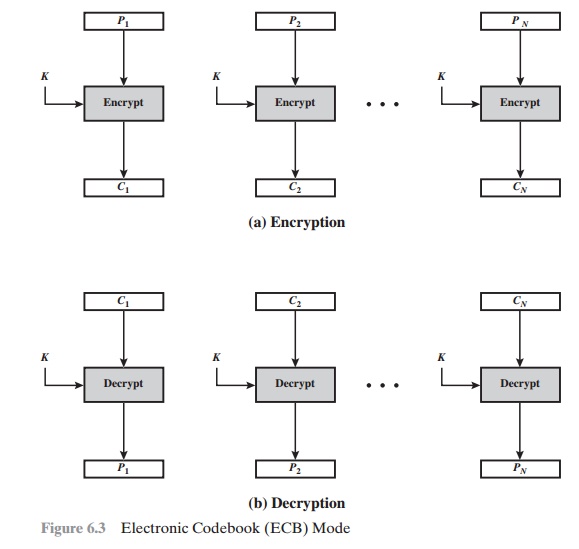
The simplest mode
is the electronic codebook (ECB) mode,
in which plaintext is handled one block at a time
and each block of plaintext is encrypted using the same key (Figure 6.3).
The term codebook
is used because,
for a given key, there
is a unique ciphertext for every b-bit
block of plaintext. Therefore, we can imagine
a gigantic codebook in which there is an entry for every possible b-bit plaintext pattern showing
its corresponding ciphertext.
For
a message longer than b bits, the procedure is simply to break the mes-
sage into b-bit blocks, padding the
last block if necessary. Decryption is per- formed one block at a time,
always using the same key. In Figure
6.3, the plaintext (padded
as necessary) consists of a sequence of b-bit blocks, P1, P2, Á , PN;
the
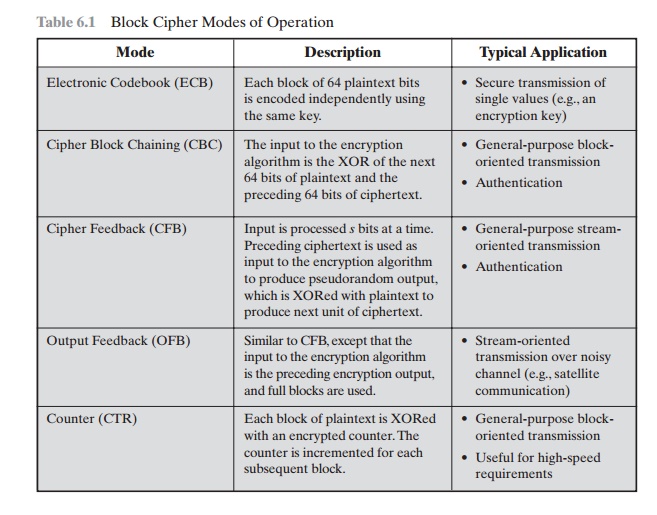
Table 6.1 Block
Cipher Modes of Operation
corresponding
sequence of ciphertext blocks is C1, C2, ......... , CN.
We can define ECB mode as follows.
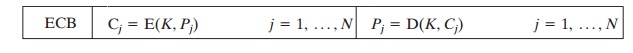
The ECB method is ideal for a short amount of
data, such as an encryption key. Thus, if you want to transmit
a DES or AES key securely,
ECB is the appropri- ate
mode to use.
The
most significant characteristic of ECB is that if the same b-bit block of plaintext appears more than once in the message, it
always produces the same ciphertext.
For lengthy messages, the ECB mode may not be secure. If the message is highly structured, it may be possible
for a cryptanalyst to exploit
these regularities. For exam-
ple, if it is known that the message always starts out with certain
predefined fields, then the cryptanalyst may have a number of known plaintext–ciphertext pairs to work with. If
the message has repetitive elements with a period of repetition a multiple
of b bits, then these elements can be identified by the analyst. This may help in the analysis
or may provide an opportunity for substituting or rearranging blocks.
Related Topics