Chapter: Cryptography and Network Security Principles and Practice : One Symmetric Ciphers : Block Cipher Operation
Counter Mode
COUNTER MODE
Although interest in the counter (CTR) mode has increased recently with applica- tions to ATM (asynchronous transfer mode) network security and IP sec
(IP security), this mode
was proposed early
on (e.g., [DIFF79]).
Figure 6.7 depicts
the CTR mode. A counter equal
to the plaintext block size is
used. The only requirement stated in SP 800-38A is that the counter value
must be
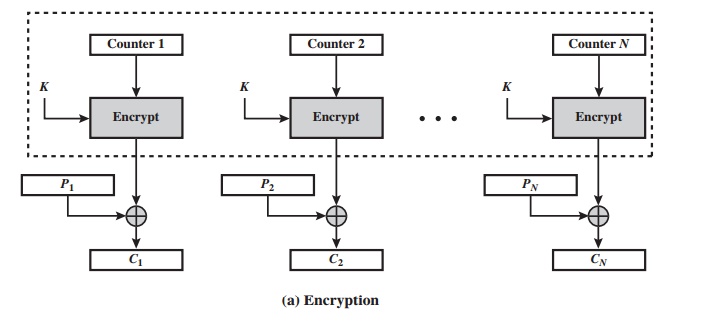
different for each plaintext block that is encrypted. Typically, the counter is initialized
to some value and then incremented by 1 for each subsequent block (modulo 2b, where b is
the block size).
For encryption, the counter
is encrypted and
then XORed with the plaintext block
to produce the ciphertext block;
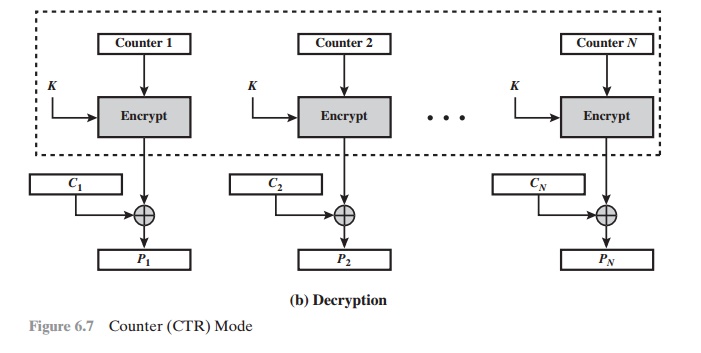
there is no chaining. For decryption, the same sequence
of counter values
is used, with
each encrypted counter XORed with a ciphertext block to recover
the corresponding plaintext block. Thus, the initial counter value
must be made available for decryption. Given
a sequence of counters T1, T2, ......., TN, we can define
CTR mode as follows.

For the last plaintext block,
which may be a partial
block of u bits, the most sig- nificant u bits of the
last output block
are used for
the XOR operation; the remaining b -u bits are discarded. Unlike
the ECB, CBC, and CFB modes, we do not need to use
padding because of the structure of the CTR mode.
As
with the OFB mode, the initial
counter value must be a nonce; that is, T1 must
be different for all of the messages
encrypted using the same key. Further, all Ti values across all messages must be unique.
If, contrary to this requirement, a counter
value is used multiple times, then the confidentiality of all of the plaintext
blocks corresponding to that counter value
may be compromised. In particular, if any plain- text block that is encrypted using a given counter value is known,
then the output of
the encryption function can be determined easily from the associated ciphertext
block. This output allows any other plaintext blocks that are encrypted using
the same counter value
to be easily recovered from their associated ciphertext blocks.
One
way to ensure the uniqueness of counter values is to continue to incre- ment
the counter value by 1 across messages. That
is, the first counter value of the
each message is one more than the last counter
value of the preceding message.
[LIPM00]
lists the following advantages of CTR mode.
•
Hardware efficiency: Unlike
the three chaining modes, encryption (or decryption)
in CTR mode can be done in parallel on multiple blocks of plain- text or ciphertext. For the chaining modes, the algorithm must
complete the computation on one block before
beginning on the next block.
This limits the maximum throughput of the algorithm
to the reciprocal of the time for one execution of block encryption or decryption. In CTR mode, the throughput is only limited by the amount
of parallelism that is achieved.
•
Software efficiency: Similarly,
because of the
opportunities for parallel execu- tion in CTR mode, processors that support parallel
features, such as aggressive
pipelining, multiple instruction dispatch per clock
cycle, a large number
of reg- isters, and
SIMD instructions, can
be effectively utilized.
•
Preprocessing: The execution
of the underlying encryption algorithm does
not depend on input of the plaintext or ciphertext. Therefore, if sufficient memory is available and security is
maintained, preprocessing can be used to prepare the output of the encryption
boxes that feed into the XOR functions, as in Figure 6.7. When the plaintext or
ciphertext input is presented, then the only computation is a series of XORs. Such a strategy
greatly enhances throughput.
•
Random
access: The ith block of plaintext or ciphertext can
be processed in random-access fashion. With the chaining modes, block Ci cannot be com-
puted until the i – 1 prior
block are computed. There may be applications in which a ciphertext is stored and it is desired to decrypt just one block;
for such applications, the random access
feature is attractive.
•
Provable
security: It can be shown that CTR is at least as secure as the
other modes discussed in this section.
•
Simplicity: Unlike ECB and CBC modes, CTR mode requires
only the imple- mentation of the encryption algorithm and not the decryption algorithm. This matters most when the decryption algorithm differs substantially from the encryption algorithm, as it does for AES.
In addition, the decryption key scheduling need not be implemented.
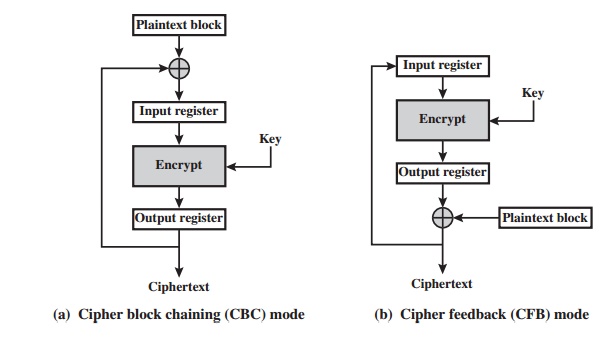
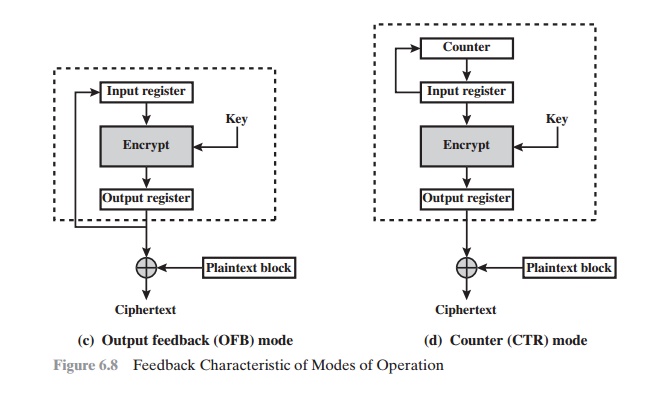
Note
that, with the exception of ECB, all
of the NIST-approved block cipher modes of operation
involve feedback. This is clearly
seen in Figure 6.8. To highlight the feedback mechanism, it is
useful to think of the encryption function as taking input from a input
register whose length equals the encryption block length and with output
stored in an output register. The input
register is updated
one block at a
time by the feedback mechanism. After each update, the encryption algorithm is
executed, producing a result in the output
register. Meanwhile, a block of plaintext
is accessed. Note that both OFB and CTR produce output that is independent of
both the plaintext and the ciphertext. Thus,
they are natural candidates for stream ciphers that encrypt plaintext by XOR one full block
at a time.
Related Topics