Chapter: Cryptography and Network Security Principles and Practice : Network and Internet Security : IP Security
Cryptographic Suites
CRYPTOGRAPHIC SUITES
The IPsecv3 and IKEv3 protocols
rely on a variety of types of cryptographic algorithms. As we have seen in this
book, there are many cryptographic algorithms of each type, each with a variety
of parameters, such as key size. To promote
interoper- ability, two RFCs define
recommended suites of cryptographic algorithms and para- meters for various applications.
RFC 4308 defines
two cryptographic suites
for establishing virtual
private net- works. Suite
VPN-A matches the commonly used corporate VPN security used in older IKEv1
implementations at the time of the issuance of IKEv2 in 2005. Suite VPN-B
provides stronger security and is recommended for new VPNs that imple- ment IPsecv3
and IKEv2.
Table 19.4a lists the algorithms and parameters for the two suites. There are several points to note about these two suites. Note that for symmetric
Table 19.4 Cryptographic Suites for IPsec
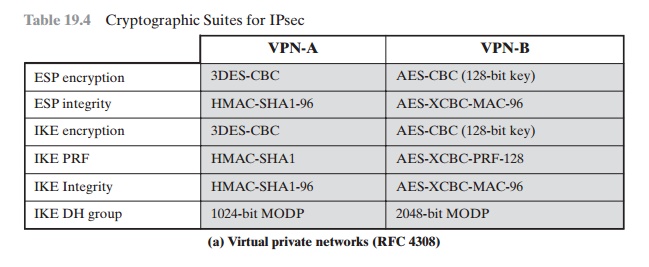
cryptography, VPN-A relies on 3DES and HMAC,
while VPN-B relies exclu- sively on AES. Three types of secret-key algorithms
are used:
•
Encryption: For
encryption, the cipher block chaining
(CBC) mode is used.
•
Message authentication: For message authentication, VPN-A
relies on HMAC with SHA-1
with the output
truncated to 96 bits. VPN-B relies
on a variant of CMAC with the output truncated to 96 bits.
•
Pseudorandom function: IKEv2
generates pseudorandom bits by repeated use of the MAC used for message authentication.
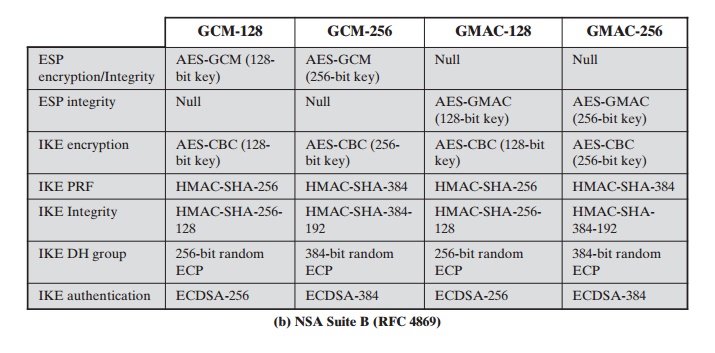
RFC 4869 defines
four optional cryptographic suites that are compatible with the United States National Security
Agency’s Suite B specifications. In 2005, the NSA issued Suite B, which defined the algorithms and
strengths needed to protect both sensitive but unclassified
(SBU) and classified information for use in its
Cryptographic Modernization program [LATT09].
The four suites defined in RFC 4869 provide choices for ESP and IKE.
The four suites are differentiated
by the choice of cryptographic algorithm strengths and a choice of whether ESP
is to provide both confidentiality and integrity or integrity only. All of the suites offer greater protection than the two VPN suites defined in RFC 4308.
Table 19.4b lists the algorithms and
parameters for the two suites. As with RFC 4308, three categories of secret key
algorithms are listed:
•
Encryption: For ESP, authenticated encryption is provided using the GCM mode
with either 128-bit or 256-bit AES keys. For
IKE encryption, CBC is used, as it was for the VPN suites.
•
Message authentication: For ESP, if
only authentication is required, then
GMAC is used. As discussed in Chapter 12, GMAC is simply
the authentication portion of
GMC. For IKE, message authentication
is provided using HMAC with one
of the SHA-3
hash functions.
•
Pseudorandom function: As with
the VPN suites,
IKEv2 in these
suites gener- ates pseudorandom bits by repeated use
of the MAC used for message authentication.
For the Diffie-Hellman algorithm, the use of elliptic curve groups modulo a
prime is specified. For authentication, elliptic
curve digital signatures are listed. The original IKEv2
documents used RSA-based digital signatures. Equivalent or greater strength can be achieved
using ECC with fewer key bits.
Related Topics