Chapter: Security in Computing : Administering Security
Characteristics of a Good Security Policy
Characteristics of a Good Security Policy
If a security policy is
written poorly, it cannot guide the developers and users in providing
appropriate security mechanisms to protect important assets. Certain
characteristics make a security policy a good one.
Coverage
A security policy must be
comprehensive: It must either apply to or explicitly exclude all possible
situations. Furthermore, a security policy may not be updated as each new
situation arises, so it must be general enough to apply naturally to new cases
that occur as the system is used in unusual or unexpected ways.
Durability
A security policy must grow
and adapt well. In large measure, it will survive the system's growth and
expansion without change. If written in a flexible way, the existing policy
will be applicable to new situations. However, there are times when the policy
must change (such as when government regulations mandate new security
constraints), so the policy must be changeable when it needs to be.
An important key to
durability is keeping the policy free from ties to specific data or protection
mechanisms that almost certainly will change. For example, an initial version
of a security policy might require a ten-character password for anyone needing
access to data on the Sun workstation in room 110. But when that workstation is
replaced or moved, the policy's guidance becomes useless. It is preferable to
describe assets needing protection in terms of their function and
characteristics, rather than in terms of specific implementation. For example,
the policy on Sun workstations could be reworded to mandate strong
authentication for access to sensitive student grades or customers' proprietary
data. Better still, we can separate the elements of the policy, having one
policy statement for student grades and another for customers' proprietary
data. Similarly, we may want to define one policy that applies to preserving
the confidentiality of relationships, and another protecting the use of the
system through strong authentication.
Realism
The policy must be realistic.
That is, it must be possible to implement the stated security requirements with
existing technology. Moreover, the implementation must be beneficial in terms
of time, cost, and convenience; the policy should not recommend a control that
works but prevents the system or its users from performing their activities and
functions. Sidebar 8 -7 points out that
sometimes the policy writers are seduced by what is fashionable in security at
the time of writing. It is important to make economically worthwhile
investments in security, just as for any other careful business investment.
Usefulness
An obscure or incomplete
security policy will not be implemented properly, if at all. The policy must be
written in language that can be read, understood, and followed by anyone who
must implement it or is affected by it. For this reason, the policy should be
succinct, clear, and direct.
Examples
To understand the nature of
security policies, we study a few examples to illustrate some of the points
just presented.
Sidebar
8-7: The Economics of Information Security Policy
Anderson [AND02a] asks that we
consider carefully the economic aspects of security when we devise our security
policy. He points out that the security engineering community tends to
overstate security problems because it is in their best interest to do so.
"The typical infosec professional is a firewall vendor struggling to meet
quarterly sales targets to prop up a sagging stock price, or a professor trying
to mine the 'cyberterrorism' industry for grants, or a policeman pitching for
the budget to build up a computer crime agency." Thus, they may exaggerate
a security problem to meet a more pressing goal.
Moreover, the security community is
subject to fads, as in other disciplines. Anderson says that network security
is trendy in 2002, which means that vendors are pushing firewalls and
encryption, products that have been oversold and address only part of the
typical organization's security problems. He suggests that, rather than
focusing on what is fashionable, we focus
instead on asking for a reasonable return on our investment in security.
Soo Hoo's research indicates that a reasonable number is 20 percent,
at a time when companies usually expect a 30 percent return from their
investments in information technology [SOO00]. In this context, it may
be more worthwhile to implement simple, inexpensive measures such as enabling
screen-locking than larger, more complex and expensive measures such as PKI and
centralized access control. As Anderson points out, "you could spend a bit
less on security if you spend it smarter."
Data Sensitivity Policy
Our first example is from an
organization that decided to classify all its data resources into four levels,
based on how severe might be the effect if a resource were damaged. These
levels are listed in Table 8-9. Then,
the required protection was based on the resource's level. Finally, the
organization analyzed its threats, their possible severities, and
countermeasures, and their effectiveness, within each of the four levels.
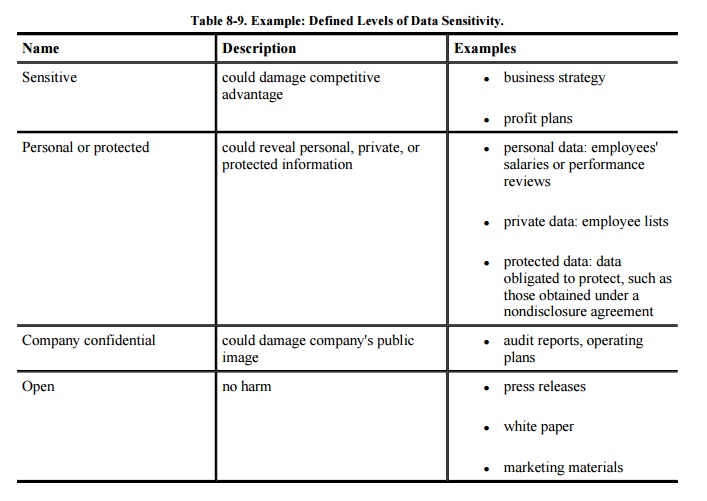
Although the phrases
describing the degree of damage are open to interpretation, the intent of these
levels is clear: All information assets are to be classified as sensitive,
personal, confidential, or open, and protection requirements for these four
types are detailed in the remainder of the organization's policy document.
Government Agency IT Security Policy
The U.S. Department of Energy
(DOE), like many government units, has established its own security policy. The
following excerpt is from the policy on protecting classified material, although
the form is appropriate for many unclassified uses as well.
It is the policy of DOE that
classified information and classified ADP [automatic data processing] systems
shall be protected from unauthorized access (including the enforcement of
need-to-know protections), alteration, disclosure, destruction, penetration,
denial of service, subversion of security measures, or improper use as a result
of espionage, criminal, fraudulent, negligent, abusive, or other improper
actions. The DOE shall use all reasonable measures to protect ADP systems that
process, store, transfer, or provide access to classified information, to
include but not limited to the following: physical security, personnel
security, telecommunications security, administrative security, and hardware
and software security measures. This order establishes this policy and defines
responsibilities for the development, implementation, and periodic evaluation
of the DOE program.
The policy then continues for
several more pages to list specific responsibilities for specific people.
The cited paragraph is
comprehensive, covering practically every possible source (espionage, crime,
fraud, etc.) of practically every possible harm (unauthorized access,
alteration, destruction, etc.), and practically every possible kind of control
(physical, personnel, etc.). The generality of the header paragraph is
complemented by subsequent paragraphs giving specific responsibilities:
"Each data owner shall
determine and declare the required protection level of information . . ."
"Each security officer
shall . . . perform a risk assessment to identify and document specific . . .
assets, . . . threats, . . . and vulnerability . . ."
"Each manager
shall...establish procedures to ensure that systems are continuously monitored...to
detect security infractions . . ." and so on.
Internet Security Policy
The Internet does not have a
governing security policy per se, because it is a federation of users.
Nevertheless, the Internet Society drafted a security policy for its members [PET91]. The policy contains the following
interesting portions.
Users are individually
responsible for understanding and respecting the security policies of the
systems (computers and networks) they are using. Users are individually
accountable for their own behavior.
Users have a responsibility
to employ available security mechanisms and procedures for protecting their own
data. They also have a responsibility for assisting in the protection of the
systems they use.
Computer and network service
providers are responsible for maintaining the security of the systems they
operate. They are further responsible for notifying users of their security
policies and any changes to these policies.
Vendors and system developers
are responsible for providing systems which are sound and which embody adequate
security controls.
Users, service providers, and
hardware and software vendors are responsible for cooperating to provide
security.
Technical improvements in
Internet security protocols should be sought on a continuing basis. At the same
time, personnel developing new protocols, hardware or software for the Internet
are expected to include security considerations as part of the design and
development process.
These statements clearly
state to whom they apply and for what each party is responsible.
Related Topics