Chapter: Cryptography and Network Security Principles and Practice : Cryptographic Data Integrity Algorithms : Cryptographic Hash Functions
Applications of Cryptographic Hash Functions
APPLICATIONS
OF CRYPTOGRAPHIC HASH FUNCTIONS
Perhaps the most versatile cryptographic algorithm is the cryptographic hash function.
It is used in a wide variety
of security applications and Internet protocols. To better understand some of the requirements and security
implications for cryptographic hash functions,
it is useful to look at the
range of applications in which
it is employed.
Message
Authentication
Message authentication is a mechanism or
service used to verify the integrity of a message.
Message authentication assures that
data received are exactly as sent (i.e., contain no modification, insertion, deletion, or replay).
In many cases, there is a requirement that the authentication
mechanism assures that purported identity
of the sender is valid. When a hash function is used to provide message
authenti- cation, the hash function value is often referred to as a message digest.
Figure 11.2 illustrates a variety of ways in
which a hash code can be used to provide message authentication, as follows.
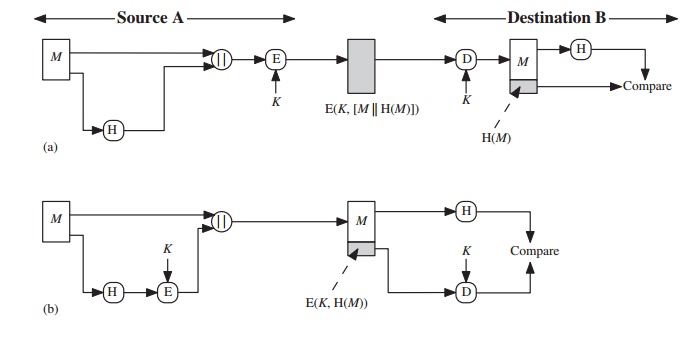
a.
The message plus concatenated hash code is encrypted using symmetric encryption. Because only
A and B share the secret key, the message must have
come from A and has not been altered. The hash
code provides the structure or redundancy
required to achieve authentication.
Because encryption is applied to the entire message plus hash code, confidentiality is also provided.
b.
Only the hash code is encrypted,
using symmetric encryption. This reduces the processing burden for those applications that do not require confidentiality.
It is possible to use a hash function
but no encryption for
message authentication.
The technique assumes that the two communicating parties share a common secret
value S.A computes the hash value over the concatenation of M and S and
appends the resulting hash value to M. Because
B possesses S, it can recompute the hash value to verify. Because
the secret value itself is not sent, an opponent
cannot modify an intercepted message and cannot generate
a false message.
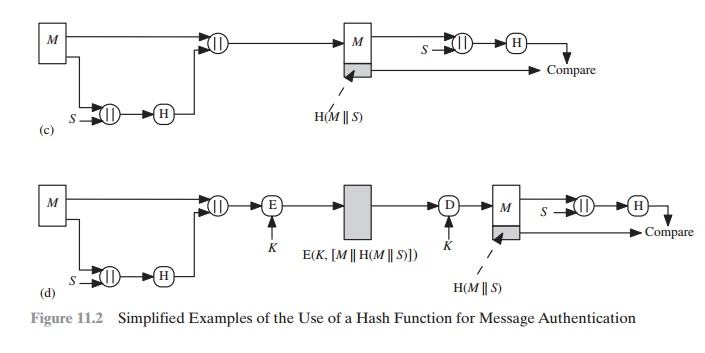
c.
Confidentiality can be added
to the approach of method
(c) by encrypting the
entire message plus the hash code.
When confidentiality is not required,
method (b) has an advantage
over methods
(a)
and (d), which encrypts
the entire message, in that less computation is required.
Nevertheless, there has been growing interest in techniques that avoid
encryption (Figure 11.2c). Several reasons for this interest
are pointed out in [TSUD92].
•
Encryption software
is relatively slow. Even though the
amount of data to be encrypted per message is small, there
may be a steady stream
of messages into and
out of a system.
•
Encryption hardware
costs are not negligible. Low-cost
chip implementations of DES are available, but the cost adds up if all nodes in a network
must have this capability.
•
Encryption hardware
is optimized toward
large data sizes. For small
blocks of data, a high proportion of the time
is spent in initialization/invocation overhead.
•
Encryption algorithms may be covered
by patents, and there
is a cost associated with licensing their use.
More commonly, message authentication is achieved using
a message authentica-
tion code (MAC), also known as a keyed hash function. Typically, MACs are used between two parties that share a
secret key to authenticate information exchanged between those parties. A
MAC function
takes as input a secret key and a data block and produces
a hash value, referred
to as the MAC. This can then be transmitted with or
stored with the protected message. If the integrity of the message needs to be checked, the MAC function can be applied to the message and the result
compared with the stored MAC value. An attacker
who alters the message will be unable
to alter the MAC value without
knowledge of the secret key. Note that the verifying
party also knows who the sending party is because
no one else knows the secret
key.
Note that the combination of
hashing and encryption results in an overall
function that is, in fact, a MAC (Figure 11.2b).
That is, E(K, H(M)) is a function of a
variable-length message M and a
secret key K, and it produces a
fixed-size output that is secure against an opponent who does not know the
secret key. In practice, specific MAC algorithms are designed that are
generally more efficient than an encryption
algorithm.
We discuss MACs in Chapter 12.
Digital Signatures
Another important
application, which is similar to the message authentication application, is the digital signature. The operation
of the digital signature is similar
to that of the MAC. In the case of the digital signature, the hash value of a message
is encrypted with a user’s private key. Anyone
who knows the user’s public key can verify the integrity of the message
that is associated with the digital
signature. In this case, an attacker who wishes to
alter the message would need to know the user’s private key. As we shall see in Chapter
14, the implications of digital signatures go beyond just message
authentication.
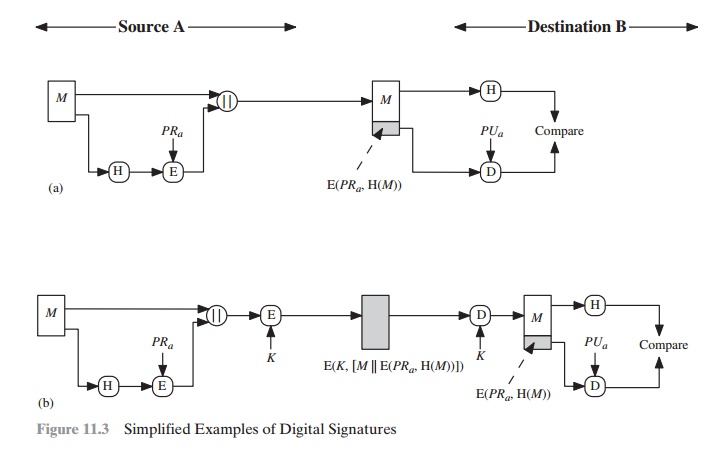
Figure 11.3 illustrates, in a simplified
fashion, how a hash code is used to provide a digital signature.
a.
The hash code is encrypted, using public-key encryption with the sender’s
pri- vate key. As with Figure
11.2b, this provides
authentication. It also provides a digital signature, because only the sender could have produced the encrypted
hash code. In fact,
this is the essence of the digital
signature technique.
b.
If confidentiality as well as a digital
signature is desired,
then the message
plus the private-key-encrypted hash code can be encrypted
using a symmetric secret key. This
is a common technique.
Other Applications
Hash functions are commonly used to create
a one-way password file. Chapter 20 explains a scheme in which a hash of a
password is stored by an operating system rather than the password
itself. Thus, the actual password
is not retrievable by a hacker
who gains access to the password
file. In simple terms,
when a user enters a password,
the hash of that password is compared to the stored hash
value for verification. This approach to password
protection is used by most operating systems.
Hash functions can
be used for
intrusion detection
and virus detection. Store H(F) for each file on
a system and secure the hash values (e.g., on
a CD-R that is
kept secure). One can later determine if a
file has been modified by recomputing H(F). An intruder would need to change F
without changing H(F).
A cryptographic hash function can be used to construct a pseudorandom func- tion (PRF) or a pseudorandom number generator (PRNG). A common application for a hash-based PRF is for the generation of symmetric keys. We discuss
this appli- cation in Chapter 12.
Related Topics