Chapter: Distributed Systems : Communication in Distributed System
Security model
Security model
The
sharing of resources as a motivating factor for distributed systems, and in
Section 2.3 we described their architecture in terms of processes, potentially
encapsulating higher-level abstractions such as objects, components or
services, and providing access to them through interactions with other
processes. That architectural model provides the basis for our security model:
the
security of a distributed system can be achieved by securing the processes and
the channels used for their interactions and by protecting the objects that
they encapsulate against unauthorized access.
Protection
is described in terms of objects, although the concepts apply equally well to
resources of all types
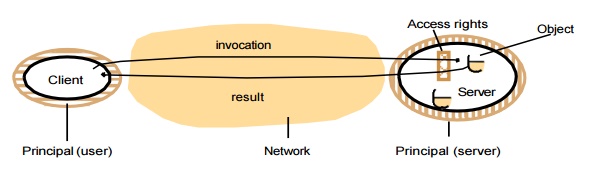
Protecting objects :
Server
that manages a collection of objects on behalf of some users. The users can run
client programs that send invocations to the server to perform operations on
the objects. The server carries out the operation specified in each invocation
and sends the result to the client.
Objects
are intended to be used in different ways by different users. For example, some
objects may hold a user’s private data, such as their mailbox, and other
objects may hold shared data such as web pages. To support this, access rights specify who is allowed to
perform the operations of an object – for example, who is allowed to read or to
write its state.
Securing processes and their
interactions • Processes interact by sending messages.
The messages are exposed to attack because the network and the
communication service that they use are open, to enable any pair of
processes to interact. Servers and peer processes expose their interfaces,
enabling invocations to be sent to them by any other process.
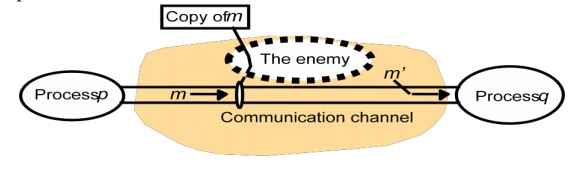
The enemy • To model security threats, we postulate an enemy (sometimes also
known as the adversary) that is capable of sending
any message to any process and reading or copying any message sent between a
pair of processes, as shown in the following figure. Such attacks can be made
simply by using a computer connected to a network to run a program that reads
network messages addressed to other computers on the network, or a program that
generates messages that make false requests to services, purporting to come
from authorized users. The attack may come from a computer that is legitimately
connected to the network or from one that is connected in an unauthorized
manner. The threats from a potential enemy include threats to processes and threats to communication channels.
Defeating security threats
Cryptography and shared secrets: Suppose that a pair
of processes (for example, a particular client and a particular server) share a secret; that is, they both
know the secret but no other process in the distributed system knows it. Then
if a message exchanged by that pair of processes includes information that
proves the sender’s knowledge of the
shared
secret, the recipient knows for sure that the sender was the other process in
the pair. Of course, care must be taken to ensure that the shared secret is not
revealed to an enemy.
Cryptography is the science of keeping
messages secure, and encryption is
the process of scrambling a message
in such a way as to hide its contents. Modern cryptography is based on
encryption algorithms that use secret keys –
large numbers that are difficult to guess – to transform data in a manner that
can only be reversed with knowledge of the corresponding decryption key.
Authentication: The use of shared secrets and
encryption provides the basis for the authentication of messages – proving the identities supplied by
their senders. The basic authentication
technique is to include in a message an encrypted portion that contains enough
of the contents of the message to guarantee its authenticity. The
authentication portion of a request to a file server to read part of a file,
for example, might include a representation of the requesting principal’s
identity, the identity of the file and the date and time of the request, all
encrypted with a secret key shared between the file server and the requesting
process. The server would decrypt this and check that it corresponds to the
unencrypted details specified in the request.
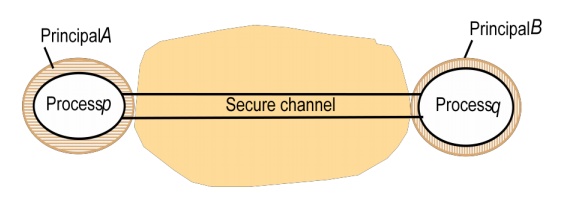
Secure channels: Encryption and authentication are used
to build secure channels as a service layer on top of existing communication services. A secure channel
is a communication channel connecting a pair of processes, each of which acts
on behalf of a principal, as shown in the following figure. A secure channel
has the following properties:
Each of
the processes knows reliably the identity of the principal on whose behalf the
other process is executing. Therefore if a client and server communicate via a
secure channel, the server knows the identity of the principal behind the
invocations and can check their access rights before performing an operation.
This enables the server to protect its objects correctly and allows the client
to be sure that it is receiving results from a bona fide server.
A secure
channel ensures the privacy and integrity (protection against tampering) of the
data transmitted across it.
Each
message includes a physical or logical timestamp to prevent messages from being
replayed or reordered.
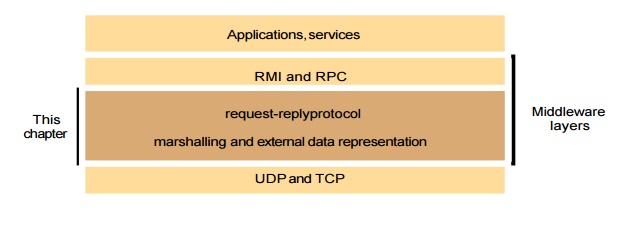
Communication
aspects of middleware, although the principles discussed are more widely
applicable. This one is concerned with the design of the components shown in
the darker layer in the following figure.
The
application program interface to UDP provides a message passing abstraction– the simplest form of interprocess
communication. This enables a sending process to transmit a single message to a
receiving process. The independent packets containing these messages are called
datagrams. In the Java and UNIX APIs,
the sender specifies the destination using a socket – an indirect reference to
a particular port used by the destination process at a destination computer.
The
application program interface to TCP provides the abstraction of a two-way stream between pairs of processes. The
information communicated consists of a stream of data items with no message
boundaries. Streams provide a building block for producer-consumer
communication. A producer and a consumer form a pair of processes in which the
role of the first is to produce data items and the role of the second is to
consume them. The data items sent by the producer to the consumer are queued on
arrival at the receiving host until the consumer is ready to receive them. The
consumer must wait when no data items are available. The producer must wait if
the storage used to hold the queued data items is exhausted.
The API for the Internet protocols
The
general characteristics of interprocess communication and then discuss the
Internet protocols as an example, explaining how programmers can use them,
either by means of UDP messages or through TCP streams.
Related Topics