Chapter: Information Security : Physical Design
Intrusion Detection System
INTRUSION DETECTION SYSTEM
1 Introduction
Intrusion: type of
attack on information assets in which instigator attempts to gain entry into or disrupt system with harmful
intent
Intrusion detection: consists
of procedures and systems created and operated to detect system intrusions
Intrusion reaction: encompasses
actions an organization undertakes when intrusion event is detected
Intrusion correction activities: finalize
restoration of operations to a normal state
Intrusion prevention: consists
of activities that seek to deter an intrusion from occurring
2 Intrusion Detection Systems (IDSs)
Detects a violation of its configuration and activates alarm
Many IDSs
enable administrators to configure systems to notify them directly of trouble
via e-mail or pagers
Systems can also be configured to notify an external security service
organization of a
“break-in”
3 IDS Terminology
Alert or alarm
False negative
The
failure of an IDS system to react to an actual attack event.
False positive
An alarm
or alert that indicates that an attack is in progress or that an attack has
successfully occurred when in fact there was no such attack.
Confidence value
Alarm filtering
4. IDSs Classification
All IDSs use one of two detection
methods:
Signature-based
Statistical
anomaly-based
IDSs operate as:
network-based
host-based
application-based systems
1 Signature-Based IDS
Examine data traffic in search of patterns that match known signatures
Widely used because many attacks have clear and distinct signatures
Problem with this approach is that as new attack strategies are
identified, the IDS’s database of signatures must be continually updated
2 Statistical Anomaly-Based IDS
The
statistical anomaly-based IDS (stat IDS) or behavior-based IDS sample network
activity to compare to traffic that is known to be normal
When measured activity is outside baseline parameters or clipping level,
IDS will trigger an alert
IDS can detect new types of attacks
Requires much more overhead and processing capacity than signature-based
May
generate many false positives
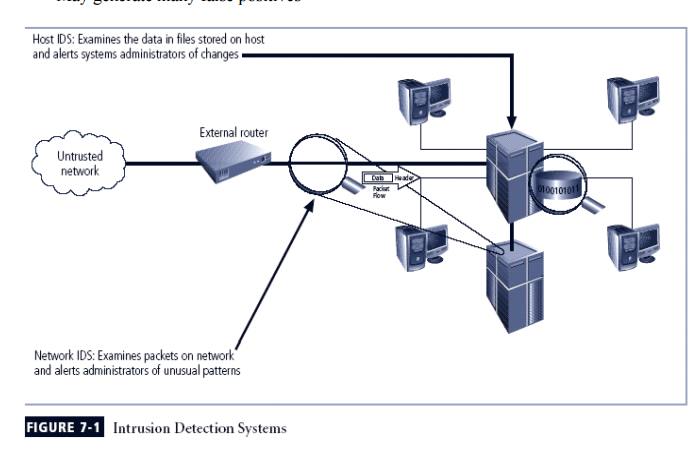
Resides on computer or appliance connected to segment of an
organization’s network; looks for signs of attacks
When examining packets, a NIDS looks for attack patterns
Installed at specific place in the network where it can watch traffic
going into and out of particular network segment
NIDS Signature Matching
To detect an attack, NIDSs look for attack patterns
Done by using special implementation of TCP/IP stack:
In process of protocol stack verification, NIDSs
look for invalid data packets
In application protocol verification, higher-order
protocols are examined for unexpected packet behavior or improper use
Advantages and Disadvantages of NIDSs
Good network design and placement of NIDS can enable organization to use
a few devices to monitor large network
NIDSs are usually passive and can be deployed into existing networks with
little disruption to normal network operations
NIDSs not usually susceptible to direct attack and may not be detectable
by attackers
Can become overwhelmed by network volume and fail to recognize attacks
Require access to all traffic to be monitored
Cannot analyze encrypted packets
Cannot reliably ascertain if attack was successful or not
Some forms of attack are not easily discerned by NIDSs, specifically
those involving fragmented packets
4 Host-Based IDS
Benchmark
and monitor the status of key system files and detect when intruder creates,
modifies, or deletes files
Most
HIDSs work on the principle of configuration or change management
Advantage
over NIDS: can usually be installed so that it can access information encrypted
when traveling over network
Advantages and Disadvantages of HIDSs
Can detect local events on host
systems and detect attacks that may elude a network-based IDS
Functions
on host system, where encrypted traffic will have been decrypted and is
available for processing
Not
affected by use of switched network protocols
Can
detect inconsistencies in how applications and systems programs were used by
examining records stored in audit logs
Pose more
management issues
Vulnerable
both to direct attacks and attacks against host operating system
Does not
detect multi-host scanning, nor scanning of non-host network devices
Susceptible
to some denial-of-service attacks
Can use
large amounts of disk space
Can
inflict a performance overhead on its host systems
5 Application-Based IDS
Application-based IDS (AppIDS) examines application for abnormal events
AppIDS may be configured to intercept requests:
File System
Network
Configuration
Execution Space
Advantages and Disadvantages of AppIDSs
Advantages
Aware of specific users; can observe interaction
between application and user
Able to operate even when incoming data is
encrypted
Disadvantages
More susceptible to attack
Less capable of detecting software tampering
May be taken in by forms of spoofing
Selecting IDS Approaches and Products
ü Technical and policy
considerations
What is your systems environment?
What are your security goals and objectives?
What is your existing security policy?
Organizational
requirements and constraints
What are requirements that are levied from
outside the organization?
What are your organization’s resource
constraints?
IDS
Control Strategies
An
IDS can be implemented via one of three basic control strategies
Centralized: all IDS control functions are
implemented and managed in a central location
Fully distributed: all control functions are
applied at the physical location of each IDS component
Partially distributed: combines the two;
while individual agents can still analyze and respond to local threats, they
report to a hierarchical central facility to enable organization to detect
widespread attacks
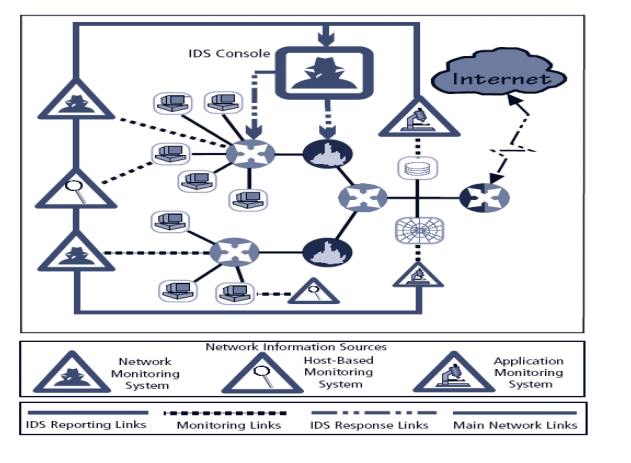
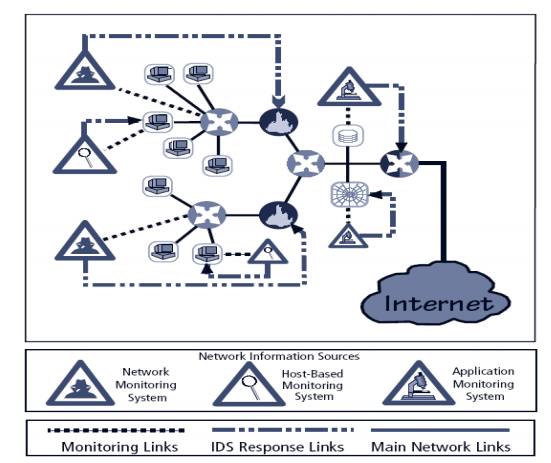
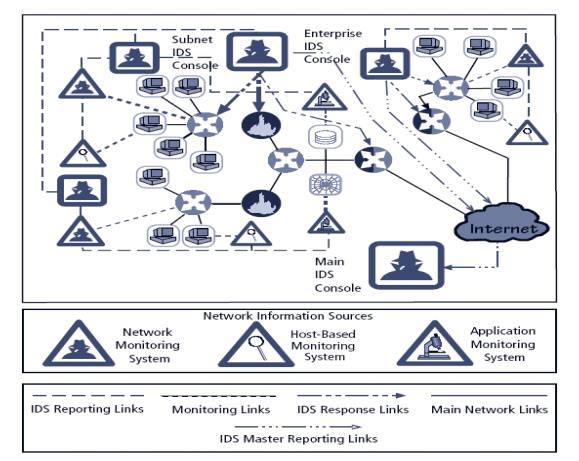
IDS Deployment Overview
Like decision regarding control strategies, decisions about where to
locate elements of intrusion detection systems can be art in itself
Planners must select deployment strategy based on careful analysis of
organization’s information security requirements but, at the same time, causes
minimal impact
NIDS and HIDS can be used in tandem to cover both individual systems
that connect to an organization’s networks and networks themselves
Deploying Network-Based IDSs
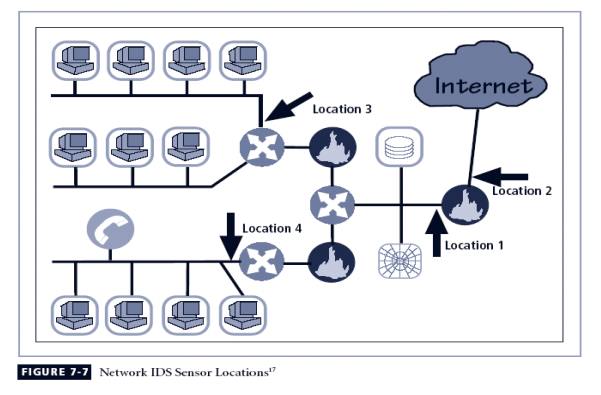
NIST recommends four locations for NIDS sensors
Location 1: behind each external firewall, in the
network DMZ
Location 2: outside an external firewall
Location 3: On major network backbones
Location 4: On critical subnets
Deploying Host-Based IDSs
Proper implementation of HIDSs can be painstaking and time-consuming
task
Deployment begins with implementing most critical systems first
Installation continues until either all systems are installed, or the
organization reaches planned degree of coverage it is willing to live with
Measuring the Effectiveness of IDSs
IDSs are
evaluated using two dominant metrics:
Administrators evaluate the number of
attacks detected in a known collection of probes
Administrators examine the level of use at
which IDSs fail
Evaluation
of IDS might read: at 100 Mb/s, IDS was able to detect 97% of directed attacks
Since
developing this collection can be tedious, most IDS vendors provide testing
mechanisms that verify systems are performing as expected
Some
of these testing processes will enable the administrator to:
Record and retransmit packets from real
virus or worm scan
Record and retransmit packets from a real
virus or worm scan with incomplete TCP/IP session connections (missing SYN packets)
Conduct a real virus or worm scan against an
invulnerable system
Honey
Pots, Honey Nets, and Padded Cell Systems
Honey
pots: decoy systems designed to lure potential attackers away from critical
systems and encourage attacks against the themselves
Honey
nets: collection of honey pots connecting several honey pot systems on a subnet
Honey
pots designed to:
Divert attacker from accessing critical
systems
Collect information about attacker’s
activity
Encourage attacker to stay on system long
enough for administrators to document event and, perhaps, respond
Padded cell: honey pot that has been
protected so it cannot be easily compromised
In addition to attracting attackers with
tempting data, a padded cell operates in tandem with a traditional IDS
When the IDS detects attackers, it
seamlessly transfers them to a special simulated environment where they can
cause no harm—the nature of this host environment is what gives approach the
name padded cell
Advantages
Attackers can be diverted to targets they
cannot damage
Administrators have time to decide how to
respond to attacker
Attackers’ actions can be easily and more
extensively monitored, and records can be used to refine threat models and
improve system protections
Honey pots may be effective at catching
insiders who are snooping around a network
Disadvantages
Legal implications of using such devices are
not well defined
Honey pots and padded cells have not yet
been shown to be generally useful security technologies
Expert attacker, once diverted into a decoy
system, may become angry and launch a more hostile attack against an
organization’s systems
Administrators and security managers will
need a high level of expertise to use these systems
Trap
and Trace Systems
Use combination of techniques to detect an
intrusion and trace it back to its source
Trap usually consists of honey pot or padded
cell and alarm
Legal drawbacks to trap and trace
Enticement: process of attracting attention
to system by placing tantalizing bits of information in key locations
Entrapment: action of luring an individual
into committing a crime to get a conviction.
Enticement is legal and ethical, whereas
entrapment is not
Related Topics