Chapter: Cryptography and Network Security Principles and Practice : Network and Internet Security : Wireless Network Security
Wireless Application Protocol Overview
WIRELESS
APPLICATION PROTOCOL OVERVIEW
The Wireless Application Protocol (WAP) is a universal, open standard
developed by the WAP Forum to provide
mobile users of wireless phones and other wireless terminals such as pagers and
personal digital assistants (PDAs) access
to telephony and information services, including the Internet and the Web. WAP
is designed to work with all wireless network technologies (e.g., GSM, CDMA, and TDMA). WAP is based on existing Internet
standards, such as IP, XML, HTML, and
HTTP, as much as possible. It also
includes security facilities. At the time of this writing, the current release
of the WAP specification is version 2.0.
Strongly
affecting the use of mobile
phones and terminals for data services
are the significant limitations of the devices and the networks that
connect them. The devices have limited processors, memory, and battery life. The user interface is also
limited, and the displays small.
The wireless networks are
characterized by relatively low bandwidth, high latency, and unpredictable availability and stability compared to wired connections. Moreover, all of these features vary widely from terminal device to
terminal device and from network
to network. Finally, mobile,
wireless users have different expectations and needs
from other information systems users.
For instance, mobile terminals must be extremely easy to use — much
easier than workstations and personal computers. WAP is designed to deal with these challenges. The WAP specification includes:
•
A programming model based on the WWW Programming Model
•
A markup language, the
Wireless Markup Language,
adhering to XML
•
A specification of a small browser suitable
for a mobile, wireless terminal
•
A lightweight communications protocol stack
•
A framework
for wireless telephony
applications (WTAs)
Operational Overview
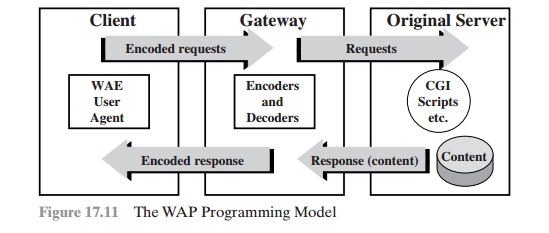
The WAP
Programming Model
is based on three elements: the client, the gateway, and the
original server (Figure 17.11). HTTP is used between
the gateway and the original server to transfer
content. The gateway acts as a proxy server for the wireless domain.
Its processor(s) provide
services that offload the limited
capabilities of the hand-held,
mobile, wireless terminals. For example, the gateway
provides DNS services,
converts between WAP protocol stack and
the WWW stack (HTTP and TCP/IP),
encodes infor-
mation from the Web into a more compact
form that minimizes wireless communica-
tion, and in the other direction, decodes the compacted
form into standard Web com-
munication conventions. The gateway also caches frequently requested information.
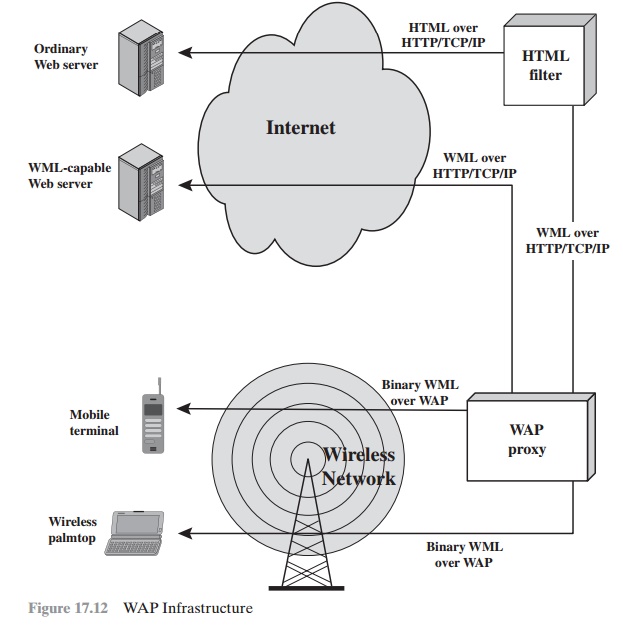
Figure 17.12 illustrates key components in a WAP environment. Using WAP, a mobile user can browse Web content on an ordinary Web server. The Web server provides content in the form of HTML-coded pages that are transmitted using the standard Web protocol stack (HTTP/TCP/IP). The HTML content must go through an HTML filter, which either may be colocated with the WAP proxy or in a separate physical module. The filter translates the HTML content into WML content. If the filter is separate from the proxy, HTTP/TCP/IP is used to deliver the WML to the proxy. The proxy converts the WML to a more compact form known as binary WML and delivers it to the mobile user over a wireless network using the WAP protocol stack. If the Web server is capable of directly generating WML content, then the WML is delivered using HTTP/TCP/IP to the proxy, which converts the WML to binary WML and then delivers it to the mobile node using WAP protocols.
The WAP
architecture is designed to cope with the two principal limitations of wireless Web access: the limitations of the mobile
node (small screen
size, limited input capability) and the low data rates of wireless
digital networks. Even with the introduction of 3G wireless
networks, which provide
broadband data rates,
the small hand-held mobile
nodes continue to have limited input and display capabilities. Thus, WAP or a similar capability will be needed for the indefinite future.
Wireless Markup Language
WML was
designed to describe content and format for presenting data on devices with limited bandwidth, limited screen size, and limited user input capability. It is designed to work with telephone keypads, styluses, and other input devices common to mobile, wireless communication. WML permits
the scaling of displays for use on two-line
screens found in some small devices,
as well as the larger screens found on smart phones.
For an ordinary
PC, a Web browser
provides content in the form of Web pages coded
with the Hypertext Markup Language (HTML). To translate
an HTML- coded Web page into WML with content and format
suitable for wireless devices, much of the information, especially graphics and animation, must be stripped
away. WML presents mainly
text-based information that attempts to capture the essence of the Web page and that is organized for easy access
for users of mobile devices.
Important features of WML include:
•
Text and image support: Formatting and layout commands are provided for text and
limited image capability.
Deck/card organizational metaphor: WML documents
are subdivided into small, well-defined units of user
interaction called cards. Users
navigate by moving back and forth between cards. A card specifies one or more
units of interaction (a menu, a screen of text, or a text-entry field). A WML
deck is similar to an HTML page in that it is identified by a Web address (URL) and is the unit of content
transmission.
•
Support for navigation among cards and decks: WML includes provisions for event handling, which is used for navigation or executing scripts.
In an HTML-based Web browser, a user navigates by clicking on links. At a WML-capable mobile device, a user interacts
with cards, moving
forward and back through the deck.
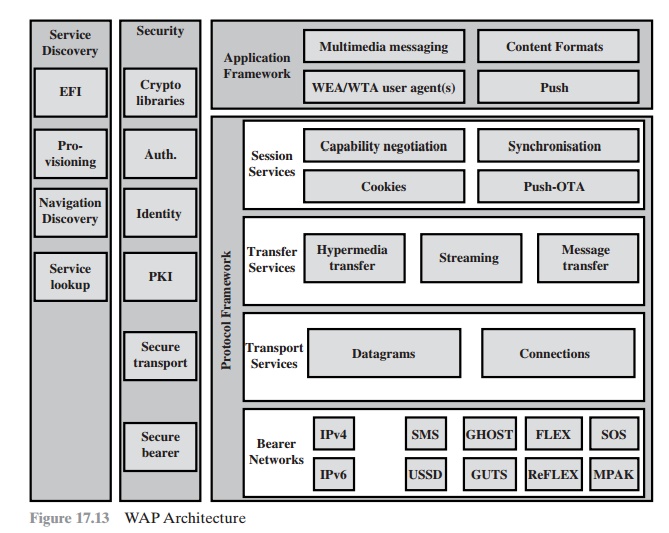
WAP Architecture
Figure 17.13,
from the WAP architecture document, illustrates the overall stack
architecture implemented in a WAP client.
In essence, this is a five-layer model. Each layer provides a set of functions and/or services to other services
and applica- tions through
a set of well-defined interfaces. Each of the layers of the architecture is accessible by the layers above,
as well as by other
services and applications. Many of the services
in the stack may be provided by more than one protocol.
For exam- ple, either
HTTP or WSP may provide
the Hypermedia Transfer service.
Common to all five layers are sets of
services that are accessible by multiple layers. These common services fall
into two categories: security services and service discovery.
SECURITY SERVICES The WAP specification includes mechanisms to provide confidentiality, integrity, authentication, and nonrepudiation. The security
services include the following.
•
Cryptographic libraries: This application framework level library
provides ser- vices for signing
of data for integrity and non-repudiation purposes.
•
Authentication: WAP provides various mechanisms for client and server
authentication. At the Session Services layer,
HTTP Client Authentication (RFC2617) may be used to authenticate clients to
proxies and application servers. At the Transport
Services layer, WTLS and TLS handshakes may be used to authenticate clients and servers.
•
Identity: The WAP Identity Module (WIM)
provides the functions
that store and process
information needed for user identification and authentication.
•
PKI: The set of security services that enable the use and management of public-key cryptography and certificates.
•
Secure transport: The Transport Services
layer protocols are defined for
secure transport over datagrams and connections. WTLS is defined
for secure transport over datagrams and TLS is defined
for secure transport over connections (i.e.,
TCP).
•
Secure bearer: Some bearer networks provide bearer-level security. For example, IP networks
(especially in the context of IPv6) provide
bearer-level security with IPsec.
SERVICE
DISCOVERY There is a collection of service discovery services that
enable the WAP client and the Web server
to determine capabilities and services. Examples of service discovery services
include the following.
•
EFI: The External
Functionality Interface (EFI) allows applications to discover what external functions/services
are available on the device.
•
Provisioning: This service allows
a device to be provisioned with the parame- ters necessary to access
network services.
•
Navigation discovery: This service allows
a device to discover new network services (e.g.,
secure pull proxies) during the course of navigation
such as when downloading
resources from a hypermedia server. The WAP Transport-
Level End-to-End Security specification, described in Section
17.5, defines one navigation discovery protocol.
•
Service lookup: This service
provides for the discovery of a service’s parame- ters through a directory lookup by name. One example of
this is the Domain Name System (DNS).
Wireless Application Environment
The WAE specifies an application framework for wireless devices such as mobile
telephones, pagers, and PDAs. In
essence, the WAE consists of tools
and formats that are intended to ease the task of developing applications and devices supported by WAP. The major elements of the WAE model (Figure 17.13) are
•
WAE user agents: Software that executes in the user’s
wireless device and that
provides specific functionality (e.g., display
content) to the end user.
•
Wireless telephony applications (WTA): A collection of telephony-specific extensions for call and feature
control mechanisms that provide authors
advanced mobile network
services. Using WTA, applications developers can use the
microbrowser to originate telephone calls and to respond to events from the
telephone network.
•
Standard content encoding: Defined to allow a WAE user
agent (e.g., a browser) to conveniently navigate Web content. On the server side are content
generators. These are applications (or services) on origin servers (e.g., CGI scripts) that produce standard content
formats in response to requests from user
agents in the mobile terminal. WAE does not specify
any standard content generators but expects that there will be a
variety available running on typical HTTP origin servers
commonly used in WWW today.
•
Push: A service to receive push transmissions from the server,
i.e., transmis- sions that are not in response to a
Web client request but are sent on the
initiative of the server. This service
is supported by the Push-OTA (Push
Over The Air)
session service.
•
Multimedia messaging: Provides for the transfer
and processing of multimedia
messages, such as e-mail and
instant messages, to WAP devices.
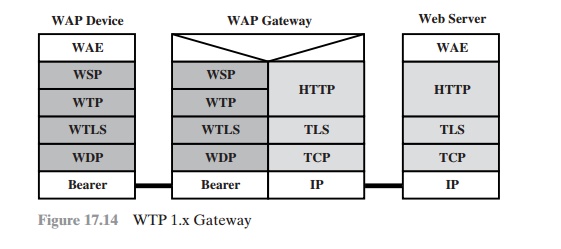
WAP Protocol Architecture
The WAP
architecture illustrated in Figure 17.13 dictates
a collection of services at each level and provides interface
specifications at the boundary between each
pair of layers. Because several of the services in the WAP stack can be provided using different
protocols based on the circumstances, there are more than one possible stack configurations. Figure 17.14 depicts
a common protocol stack configuration in which a WAP client device connects to a Web server
via a WAP gateway.
This con- figuration is common with devices that implement version
1 of the WAP specifica-
tion but is also used in version 2 devices (WAP2)
if the bearer network does not support
TCP/IP.
In the remainder of this subsection, we
provide an overview of the WAP protocols, with the exception of WTLS, which is
treated in Section 17.4.
WIRELESS SESSION PROTOCOL WSP provides
applications with an interface for two
session services. The connection-oriented session
service operates above
WTP, and the connectionless session service operates
above the unreliable transport protocol WDP.
In essence, WSP is based on HTTP with some additions and modifications to optimize
its use over wireless channels. The principal limitations addressed are low data rate
and susceptibility to loss of connection due
to poor coverage or cell overloading.
WSP is a transaction-oriented protocol
based on the concept of a request
and a reply. Each WSP protocol data unit (PDU)
consists of a body, which may contain
WML, WMLScript, or images; and a header,
which contains information about the data in the
body and about the transaction. WSP also defines a server push opera- tion, in which the server sends unrequested content
to a client device. This may be used
for broadcast messages
or for services, such as news headlines or stock quotes, that may be tailored
to each client device.
WIRELESS TRANSACTION PROTOCOL
WTP manages transactions by conveying requests and
responses between a user agent (such as a WAP browser)
and an application server for
such activities as browsing and e-commerce transactions. WTP provides a reliable transport
service but dispenses
with much of the overhead of TCP, resulting in a lightweight protocol that is suitable for
implementation in “thin” clients (e.g., mobile
nodes) and suitable
for use over low-bandwidth wireless links. WTP includes the
following features.
•
Three classes
of transaction service.
•
Optional
user-to-user reliability: WTP user triggers the confirmation of each received message.
•
Optional out-of-band data on acknowledgments.
•
PDU concatenation
and delayed acknowledgment to reduce the number of messages sent.
•
Asynchronous transactions.
WTP is transaction oriented rather than
connection oriented.With WTP, there
is no explicit connection setup or teardown but rather a reliable connectionless service.
WTP provides three transaction classes that
may be invoked by WSP or another higher layer protocol:
•
Class 0: Unreliable invoke
message with no result message
•
Class 1: Reliable invoke
message with no result message
•
Class 2: Unreliable invoke
message with one
reliable result message
Class 0 provides an unreliable datagram service, which
can be used
for an unre- liable push operation. Data from a WTP user are encapsulated by WTP (the initiator,
or client) in an invoke PDU and transmitted to the target WTP (the responder,
or server) with no acknowledgment. The responder WTP delivers the data to the target WTP user.
Class 1 provides a reliable
datagram service, which can be used for a reliable push operation. Data from an initiator
are encapsulated in an invoke PDU and
transmitted to the responder. The responder delivers the data to the
target WTP user and acknowledges receipt of the data by sending back an ACK PDU to the WTP entity on the initiator side,
which confirms the transaction to the source
WTP user. The responder WTP maintains state information for some time after the ACK has been sent to handle possible retransmission of the ACK if it gets lost and/or the
initiator retransmits the invoke PDU.
Class 2 provides a request/response transaction service and supports
the execu- tion of multiple transactions during one WSP session.
Data from an initiator are encapsulated in an invoke PDU and transmitted to the
responder, which delivers the data to
the target WTP user. The
target WTP user prepares response data, which are handed down to the local WTP entity.
The responder WTP entity sends these data back
in a result PDU. If there is a delay in generating the response
data beyond a timer threshold, the responder
may send an ACK PDU before sending
the result PDU. This prevents the initiator
from unnecessarily retransmitting the invoke
message.
WIRELESS DATAGRAM
PROTOCOL WDP is used to adapt
a higher-layer WAP protocol to the communication mechanism
(called the bearer) used between the mobile node and the WAP gateway.
Adaptation may include partitioning data into segments of appropriate size for the bearer and interfacing with the bearer
network. WDP hides details
of the various bearer networks
from the other
layers of WAP. In some
instances, WAP is implemented on top of IP.
Related Topics