Chapter: Cryptography and Network Security Principles and Practice : Network and Internet Security : Wireless Network Security
WAP End-to-End Security
WAP END-TO-END SECURITY
The basic WAP
transmission model involving a WAP client,
a WAP gateway, and a Web server
results in a security gap,
as illustrated in Figure 17.19.
This figure corre- sponds to the protocol
architecture shown in Figure 17.14.
The mobile device estab- lishes a secure WTLS session with
the WAP gateway. The WAP gateway, in turn,
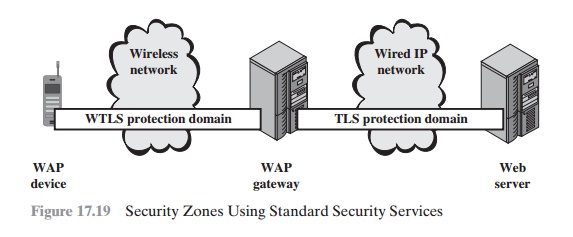
establishes a secure SSL or TLS session with the Web server. Within the gateway, data are not encrypted during the translation process. The gateway is thus a point at which
the data may be compromised.
There are a number of approaches to
providing end-to-end security between the mobile client and the Web server. In
the WAP version 2 (known as WAP2) architecture document, the WAP forum defines
several protocol arrange- ments that allow for end-to-end security.
Version 1 of WAP assumed a simplified set of
protocols over the wireless network and assumed that the wireless network did
not support IP. WAP2 provides the option for the mobile device to implement
full TCP/IP-based protocols and operate over an IP-capable wireless network.
Figure 17.20 shows two ways in which this IP capability can be exploited to
provide end-to- end security. In both approaches, the mobile client implements
TCP/IP and HTTP.
The first approach (Figure 17.20a) is to
make use of TLS between client and server. A secure TLS session is set up
between the endpoints. The WAP gateway
acts as a TCP-level gateway
and splices together
two TCP connections to carry the
traffic between the endpoints. However, the TCP user data field (TLS records) remains encrypted as it passes through the gateway, so end-to-end security is maintained.
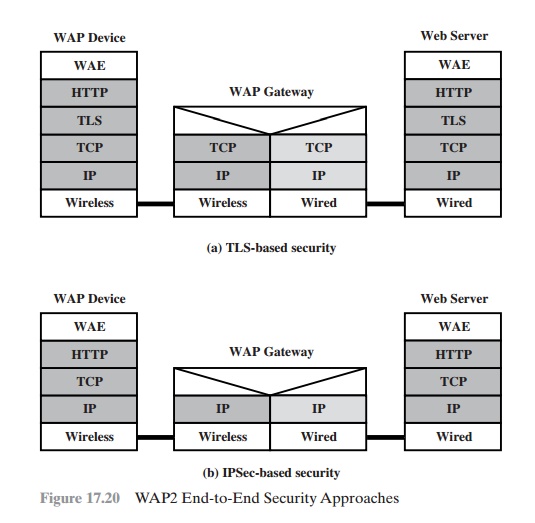
Another possible approach
is shown in Figure 17.20b.
Here we assume
that the WAP gateway acts as a simple Internet
router. In this case, end-to-end security can be provided
at the IP level using
IPsec (discussed in Chapter 19).
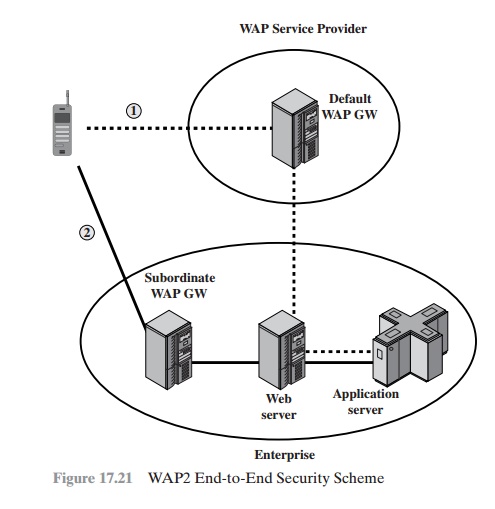
Yet another, somewhat more complicated, approach has been defined in
more specific terms by the WAP forum in specification entitled “WAP Transport Layer End-to-End Security.” This approach is illustrated in
Figure 17.21, which is based on a figure in [ASHL01].
In this scenario, the WAP client
connects to its usual WAP
gateway and attempts to send a
request through the gateway
to a secure domain. The secure
content server determines the need for
security that requires that the mobile client connect to its local WAP gateway rather than its default
WAP gateway. The Web server
responds to the initial client
request with an HTTP redirect message that redirects
the client to a WAP gateway that is
part of the enterprise network. This message
passes back through the default gateway, which validates
the redirect and sends it to the client. The client caches the redirect information
and establishes a secure session
with the enterprise WAP gateway using WTLS.
After the connection is terminated, the default gateway is reselected and used for subsequent
communication to other Web servers.
Note that this approach requires
that the enterprise maintain a WAP gateway on the wireless
net- work that the client is using.
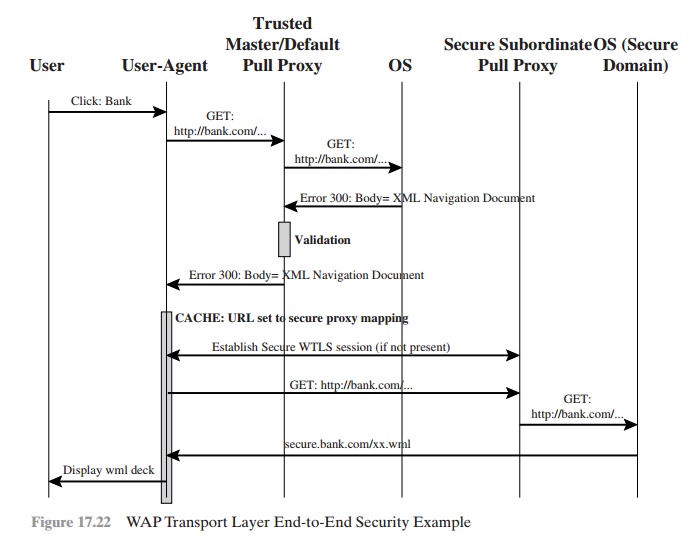
Figure 17.22, from the WAP specification,
illustrates the dialogue.
Related Topics