Chapter: Cryptography and Network Security Principles and Practice : System Security : Malicious Software
Types of Malicious Software
TYPES OF MALICIOUS
SOFTWARE
The terminology in this area presents problems
because of a lack of universal agree- ment on all of the terms and because
some of the categories overlap.
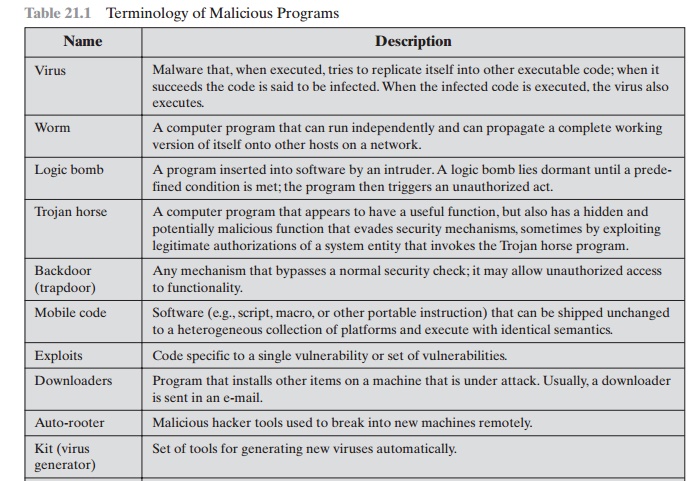
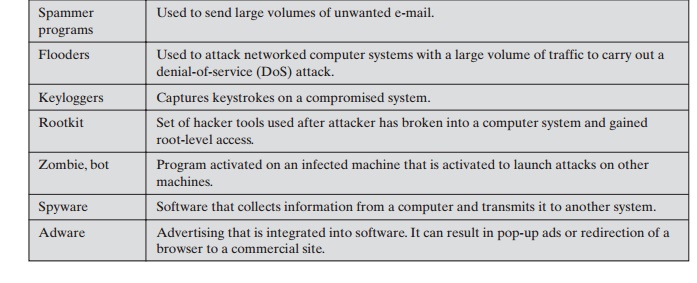
Table 21.1 is a useful guide.
Malicious software
can be divided into two categories: those
that need a host
program, and those that are independent. The former, referred to as parasitic, are essentially
fragments of programs that
cannot exist independently of some actual application program, utility, or
system program. Viruses, logic
bombs,
and
backdoors are examples. Independent malware is a self-contained program that
can be scheduled and run by the operating system. Worms and bot programs are
examples.
We
can also differentiate between those software threats that do not repli- cate
and those that do. The former are programs or fragments of programs that are
activated by a trigger. Examples are logic bombs, backdoors, and bot pro-
grams. The latter consist of either a program fragment or an independent
program that, when executed, may produce one or more copies of itself to be activated later on the same system or
some other system. Viruses and worms are examples.
In the remainder of this section,
we briefly survey some of the key categories
of malicious software, deferring discussion on the key topics of viruses and worms
until the following sections.
Backdoor
A backdoor, also known as a trapdoor, is a secret entry point into a program that allows someone who is aware of the backdoor
to gain access
without going through the
usual security access procedures. Programmers have used backdoors legiti-
mately for many years to debug and
test programs; such a backdoor is called a maintenance
hook. This usually is done when the programmer is developing an application that has an authentication procedure, or a long setup, requiring the user to enter many
different values to run the application. To debug
the program, the developer may wish to gain special privileges or to avoid
all the necessary setup and
authentication. The programmer may
also want to ensure that there is a method of activating the program should
something be wrong with the authentication proce- dure that is being built into
the application. The backdoor is
code that recognizes some special sequence
of input or is triggered by being run from a certain user ID or by an unlikely
sequence of events.
Backdoors become threats when unscrupulous programmers use
them to gain unauthorized access. The backdoor was the basic idea for the
vulnerability portrayed in the movie War
Games. Another example is that during the develop- ment of Multics,
penetration tests were conducted by an Air Force “tiger team” (simulating
adversaries). One tactic employed was to send a bogus operating system update
to a site running Multics. The update contained a Trojan horse (described
later) that could be activated by a backdoor and that allowed the tiger team to
gain access. The threat was so well implemented that the Multics developers
could not find it, even after they were informed of its presence [ENGE80].
It is difficult to implement operating system controls for
backdoors. Security measures must focus on the program development and software
update activities.
Logic Bomb
One of the oldest types of program threat, predating
viruses and worms, is the logic bomb. The logic bomb is code embedded in some
legitimate program that is set to “explode” when certain conditions are met.
Examples of conditions that can be used as triggers for a logic bomb are the
presence or absence of certain files, a particular day of the week or date, or
a particular user running the appli- cation. Once triggered, a bomb may alter
or delete data or entire files, cause a machine halt, or do some other damage.
A striking example of how logic bombs can be employed was the case of Tim
Lloyd, who was convicted of setting a logic bomb that cost his employer, Omega
Engineering, more than $10 million, derailed its corporate growth strategy, and
eventually led to the layoff of 80
workers [GAUD00]. Ultimately, Lloyd was sentenced to 41 months in prison and
ordered to pay $2 million in restitution.
Trojan Horses
A Trojan horse1 is a useful, or apparently useful, program or command
procedure containing hidden code that, when invoked, performs some unwanted or
harmful function.
Trojan horse programs
can be used to accomplish functions indirectly that an
unauthorized user could
not accomplish directly. For example,
to gain access
to the files of another user on a shared system,
a user could create a Trojan horse program that, when executed, changes
the invoking user’s
file permissions so that the
files are readable by any
user. The author could then induce users to run the program by placing it in a
common directory and naming it such that it appears to be a useful utility program
or application. An example is a program
that ostensibly produces
a listing of the user’s files
in a desirable format. After another
user has run the program, the author of the program can
then access the information in the user’s files. An example of a Trojan horse program that would be
difficult to detect is a compiler that has been modified to insert additional
code into certain programs as they are compiled, such as a system login
program [THOM84]. The code creates
a backdoor in the login program
that permits the author to log on to the system using a
special password. This
Trojan horse can never be discovered by reading the source
code of the login program.
Another common motivation for the Trojan horse is
data destruction. The program appears
to be performing a useful
function (e.g.,
a calculator program), but it may also be quietly deleting the user’s files. For example, a CBS executive was
victimized by a Trojan horse that
destroyed all information contained in his com- puter’s memory [TIME90]. The Trojan horse was implanted in a graphics
routine offered on an electronic bulletin
board system.
Trojan horses fit into one of three models:
• Continuing to perform
the function of the original
program and additionally performing a separate malicious activity
• Continuing to perform
the function of the original
program but modifying
the function to perform malicious activity (e.g., a Trojan horse
version of a login program that collects passwords) or to disguise
other malicious activity
(e.g., a Trojan horse version of a process
listing program that does not display certain processes that are malicious)
• Performing a
malicious function that completely replaces the function of the original
program
Mobile Code
Mobile code refers to programs (e.g., script, macro, or
other portable instruction) that can be shipped unchanged to a heterogeneous collection of platforms and execute with identical semantics [JANS01]. The term also
applies to situations involving a large homogeneous collection of platforms
(e.g., Microsoft Windows). Mobile code is transmitted
from a remote system to a local system and then executed on the local system without the user’s explicit
instruction. Mobile code often acts as a mechanism for a virus,
worm, or Trojan horse to be transmitted to the user’s workstation. In other cases,
mobile code takes advantage of vulnerabilities to perform its own exploits, such as unauthorized data access or root compromise. Popular vehicles for
mobile code include Java applets, ActiveX, JavaScript, and VBScript. The most common
ways of using
mobile code for
malicious operations on local
system are cross-site scripting,
interactive and dynamic Web sites, e-mail
attachments, and downloads from untrusted sites or of
untrusted software.
Multiple-Threat Malware
Viruses and other malware may operate in multiple ways.
The terminology is far from uniform; this subsection gives
a brief introduction to several related
concepts that could be considered multiple-threat malware.
A multipartite
virus infects
in multiple ways. Typically, the
multipartite virus is capable of infecting multiple
types of files,
so that virus
eradication must deal with
all of the possible sites
of infection.
A blended
attack uses multiple methods of infection or transmission, to maxi-
mize the speed of contagion and the severity
of the attack. Some writers
characterize a blended attack
as a package that includes
multiple types of malware. An example of a blended attack is the Nimda attack,
erroneously referred to as simply a worm. Nimda uses four distribution methods:
• E-mail: A user on a vulnerable
host opens an infected e-mail attachment; Nimda looks for e-mail addresses on the host and then sends copies of itself to
those addresses.
• Windows shares: Nimda scans hosts
for unsecured Windows
file shares; it can
then use NetBIOS86 as a transport mechanism to infect files on that host in the
hopes that a user will run an infected file, which will activate Nimda on that host.
• Web servers: Nimda scans
Web servers, looking for
known vulnerabilities in Microsoft IIS. If it finds
a vulnerable server,
it attempts to transfer a copy of itself to the server
and infect it and its files.
• Web clients: If a vulnerable Web client
visits a Web server that has been infected by Nimda, the client’s workstation
will become infected.
Thus, Nimda has
worm, virus, and
mobile code characteristics. Blended attacks
may also spread through other services, such as instant
messaging and peer-to-peer file sharing.
Related Topics