Chapter: Cryptography and Network Security Principles and Practice : System Security : Malicious Software
Computer Viruses: Nature, Classification, Virus Kits
VIRUSES
The Nature of Viruses
A computer virus
is a piece of software
that can “infect” other programs by modifying
them; the modification includes injecting the original program
with a routine to make copies of the virus
program, which can then go on to infect other
programs. Computer viruses first appeared in the early
1980s, and the term itself is attributed to Fred Cohen
in 1983. Cohen is the author of a groundbreaking book on the subject [COHE94].
Biological viruses are tiny scraps of
genetic code—DNA or RNA—that can take over the machinery of a living
cell and trick
it into making
thousands of flaw- less replicas of the original
virus. Like its biological counterpart, a computer virus carries in its instructional code the recipe for making
perfect copies of itself. The typical virus becomes embedded in a program on a
computer. Then, whenever the
infected computer comes
into contact with an uninfected piece of software, a fresh copy of the
virus passes into the new program. Thus, the
infection can be spread from computer to computer by unsuspecting users who
either swap disks or send programs to one another over a network. In a network
environment, the ability to access applications and system services
on other computers
provides a perfect
cul- ture for the spread of a virus.
A virus can do anything
that other programs
do. The difference is that a virus
attaches itself to another program and executes secretly when the host program
is run. Once a virus is executing, it can perform
any function, such
as erasing files
and programs that is allowed by the privileges of the current
user.
A computer virus has three parts [AYCO06]:
• Infection mechanism: The means by which
a virus spreads, enabling it to repli-
cate. The mechanism is also referred
to as the infection vector.
• Trigger: The
event
or condition that determines when the payload
is activated or delivered.
• Payload: What the virus does,
besides spreading. The payload may involve
damage or may involve
benign but noticeable activity.
During its lifetime, a typical virus goes through the
following four phases:
• Dormant phase: The virus is idle. The virus will eventually be activated
by some event, such as a date, the presence of another program or file, or the
capacity of the disk exceeding some limit. Not all viruses have this stage.
• Propagation phase: The virus places
a copy of itself into other programs
or into certain system areas
on the disk. The copy may not be
identical to the propa- gating version;
viruses often morph
to evade detection. Each infected program will now contain a clone of the virus, which
will itself enter
a propagation phase.
• Triggering phase: The virus is activated to perform the function for which it was intended. As
with the dormant phase, the triggering phase can be caused by a variety of system events, including a count
of the number of times that this copy
of the virus has made copies of itself.
• Execution phase: The function is performed. The function may be harmless, such as a message on the screen, or damaging,
such as the destruction of programs and data files.
Most viruses
carry out their work in a manner that is specific
to a particular oper-
ating system and, in some cases, specific to a particular hardware platform. Thus, they are designed to take advantage
of the details and weaknesses of particular systems.
VIRUS STRUCTURE A virus can be prepended
or postpended to an executable program, or it can be embedded in
some other fashion. The key to its
operation is that the infected
program, when invoked,
will first execute
the virus code and then execute the original code of the program.
A very general
depiction of virus
structure is shown
in Figure 21.1 (based on [COHE94]). In this case,
the virus code,
V, is prepended to infected programs, and it is assumed
that the entry
point to the program, when invoked, is the first
line of the program.
The infected program
begins with the
virus code and
works as follows. The first line of code is a jump to the main virus
program. The second line is a special marker that is used by the virus to determine
whether or not a potential
victim program has already been infected with this virus. When
the program is invoked, control
is imme- diately transferred to the main virus program.
The virus program may first seek out
uninfected executable files and infect them. Next, the virus may perform
some action, usually
detrimental to the system. This action could be performed every time
the program is invoked, or it could
be a logic bomb that triggers only under certain conditions. Finally, the
virus transfers control
to the original program. If the
infection

phase of the program is reasonably rapid,
a user is unlikely to notice any difference
between the execution of an infected and an uninfected program.
A virus such as the one just described is
easily detected because an infected version of a program is longer than the
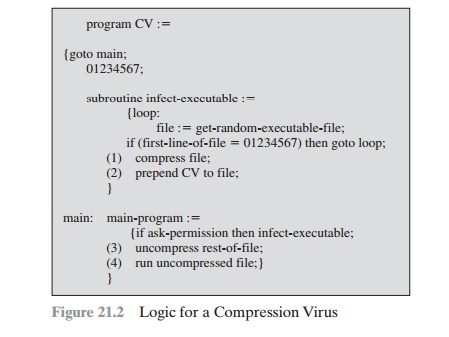
corresponding uninfected one. A way to thwart
such a simple means of detecting a virus is to compress
the executable file so
that both the infected and uninfected versions are of identical length. Figure
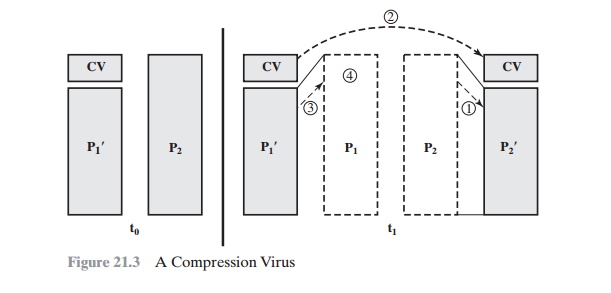
21.2 [COHE94] shows in general terms the logic required. The key lines in this virus are
numbered, and Figure 21.3 [COHE94] illustrates the operation. We assume that program P1 is infected with
the virus CV. When this program is
invoked, control passes to its virus, which
performs the following steps:
1.
For
each uninfected file P2 that is found, the virus first compresses that file to produce P¿2 , which is shorter than the original program by the size of the virus.
2.
A copy of the virus is prepended
to the compressed program.
3.
The compressed version of the original infected program,
P1¿ , is uncompressed.
4.
The uncompressed original program
is executed.
In this example, the virus does nothing
other than propagate. As previously mentioned, the virus may include a logic
bomb.
INITIAL INFECTION Once a virus has gained entry to a system by infecting a
single program, it is in a position to potentially infect some or all other executable files on
that system when the infected
program executes. Thus, viral infection can be completely
prevented by preventing the virus from gaining entry in the first place. Unfortunately, prevention is extraordinarily difficult
because a virus can be part of any
program outside a system. Thus, unless
one is content to take an absolutely bare piece of iron and write all
one’s own system and application
programs, one is vulnerable. Many forms of infection can
also be blocked by denying normal users the right to modify programs
on the system.
The lack of
access controls on early PCs
is a key reason why
traditional machine code based viruses
spread rapidly on these systems.
In contrast, while it is easy enough to write a machine code
virus for UNIX systems, they were almost never seen in practice
because the existence
of access controls
on these systems
pre- vented effective propagation of the virus. Traditional machine code
based viruses are now less prevalent, because
modern PC OSs do have more effective access con- trols. However,
virus creators have found other avenues, such as macro and e-mail viruses,
as discussed subsequently.
Viruses Classification
There has been a continuous
arms race between virus writers and writers of
antivirus software since viruses first appeared. As effective
countermeasures are developed for
existing types of viruses, newer
types are developed. There is no simple or universally agreed upon classification scheme for viruses,
In this section, we follow [AYCO06] and classify viruses along two
orthogonal axes: the type of target the virus tries to infect and the method
the virus uses to conceal itself from detection by users and antivirus software.
A virus classification by target includes the following categories:
•
Boot sector infector: Infects a master
boot record or boot record
and spreads when a system is booted from the disk containing the virus.
•
File infector: Infects files that
the operating system or shell consider to be executable.
•
Macro virus: Infects files with
macro code that is interpreted by an applica- tion.
A virus classification by concealment
strategy includes the following categories:
Encrypted virus: A typical
approach is as follows. A portion of the virus cre-
ates a random encryption key and encrypts
the remainder of the virus.
The key is stored with the virus. When an infected program is
invoked, the virus uses the stored random key to decrypt
the virus. When the virus replicates, a differ-
ent random key is selected. Because the bulk of the virus is encrypted with a
different key for each instance,
there is no constant bit pattern to observe.
• Stealth virus: A form of virus explicitly designed to hide itself from detection
by antivirus software. Thus, the entire
virus, not just a payload
is hidden.
• Polymorphic virus: A virus that mutates
with every infection, making detec- tion by the “signature” of the virus
impossible.
• Metamorphic virus: As with
a polymorphic virus,
a metamorphic virus
mutates with every infection. The difference is that a metamorphic virus
rewrites itself completely at each iteration, increasing the difficulty of detection. Metamorphic viruses may change their behavior as well
as their appearance.
One example of a stealth virus was discussed
earlier: a virus that uses com- pression so that the infected program is
exactly the same length as an uninfected version. Far more sophisticated techniques are possible. For example, a virus can place intercept
logic in disk I/O routines, so that when there is an attempt to read suspected
portions of the disk using these routines, the virus will present back the original, uninfected program. Thus, stealth is not a term that applies
to a virus as such but, rather, refers to a technique
used by a virus to evade detection.
A polymorphic virus creates copies during replication that are functionally equivalent but have distinctly different bit patterns.
As with a stealth virus, the pur- pose is to defeat programs that scan
for viruses. In this case, the “signature” of
the virus will vary with each copy. To achieve this variation, the virus may
randomly insert superfluous instructions or interchange the order of independent instructions. A more effective approach
is to use encryption. The strategy
of the encryption virus is followed. The portion of the virus that is
responsible for generating keys and performing encryption/decryption is referred to as the mutation engine. The muta- tion engine
itself is altered
with each use.
Virus Kits
Another weapon in the virus writers’ armory
is the virus-creation toolkit. Such a toolkit enables a relative novice to
quickly create a number of different viruses. Although viruses created with
toolkits tend to be less sophisticated than viruses designed from scratch, the sheer number of new viruses that can be generated using a
toolkit creates a problem for antivirus schemes.
Macro
Viruses
In the mid-1990s, macro viruses became by
far the most prevalent type of virus. Macro viruses are particularly
threatening for a number of reasons:
1.
A macro virus is platform independent. Many macro viruses
infect Microsoft Word documents or other Microsoft Office
documents. Any hardware plat- form and operating
system that supports
these applications can be infected.
2.
Macro viruses
infect documents, not executable portions
of code. Most of the
information introduced onto a computer
system is in the form of a document
rather than a program.
3.
Macro viruses are easily spread.
A very common
method is by electronic mail.
4.
Because macro
viruses infect user documents rather
than system programs, tra- ditional file system access
controls are of limited use
in preventing their
spread.
Macro viruses take
advantage of a feature found in Word and other office
applications such as Microsoft Excel, namely the macro. In essence, a
macro is an executable program
embedded in a word processing document or other
type of file. Typically, users employ macros to automate
repetitive tasks and thereby save
keystrokes. The macro language is usually some form of the Basic
programming language. A user might define
a sequence of keystrokes in a macro
and set it up so that
the macro is invoked when a function
key or special short combination of keys is input.
Successive releases of MS Office products
provide increased protection against macro viruses. For example, Microsoft offers an optional Macro Virus Protection
tool that detects suspicious Word files
and alerts the customer to the potential risk of opening
a file with macros. Various antivirus product vendors have also
developed tools to detect and correct
macro viruses. As in other types of viruses, the arms race continues in the field
of macro viruses,
but they no longer are the predominant virus threat.
ail Viruses
A more
recent development in malicious
software is the e-mail virus. The first rapidly spreading e-mail viruses, such as Melissa, made use
of a Microsoft Word macro embedded in an attachment. If the recipient
opens the e-mail attachment, the Word macro is activated. Then
1.
The e-mail virus sends
itself to everyone
on the mailing list in the user’s
e-mail package.
2.
The virus does local
damage on the user’s system.
In 1999, a
more powerful version of the e-mail virus appeared. This newer version can be activated
merely by opening
an e-mail that contains the virus rather than
opening an attachment. The virus uses the Visual Basic scripting language supported by the e-mail package.
Thus we see a new generation of malware that arrives via e-mail and uses e-mail
software features to replicate itself
across the Internet. The virus
propagates itself as soon as it is activated (either by
opening an e-mail attachment or by opening the e-mail) to all of the e-mail addresses known to the infected host.
As a result, whereas
viruses used to take months
or years to propagate, they now do so in hours.This makes it very difficult for antivirus
software to respond before much damage is done. Ultimately, a greater
degree of security
must be built
into Internet utility
and applica- tion software on PCs to counter the
growing threat.
Related Topics